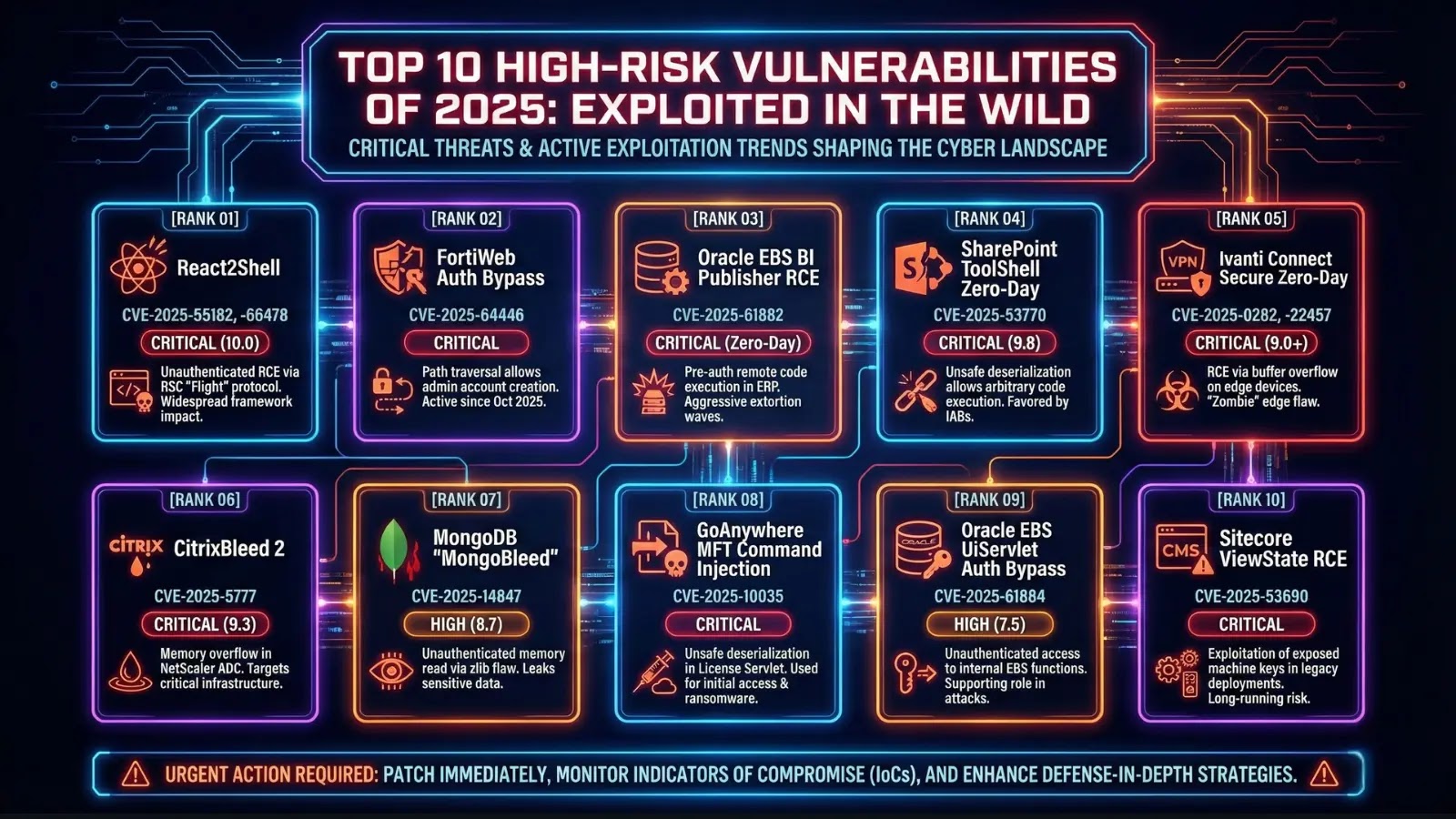
Top 10 High-Risk Vulnerabilities Of 2025 that Exploited in the Wild
The cybersecurity landscape has always been a dynamic battleground, but 2025 has amplified this reality to unprecedented levels. With an astounding 21,500+ CVEs disclosed in the first half of the year alone – a significant 16-18% increase over 2024 – organizations are facing a tsunami of potential attack vectors. Among this deluge, a critical subset of vulnerabilities has emerged, characterized by their exceptional severity and, most critically, active exploitation in the wild. These aren’t theoretical threats; they are the active weapons in the arsenals of sophisticated adversaries. Understanding and mitigating these high-risk vulnerabilities is not merely a best practice; it’s an imperative for survival in the current digital climate. This analysis dives deep into the top 10 high-risk vulnerabilities that defined the first half of 2025, providing critical insights and actionable remediation strategies.
The Escalating Threat Landscape of 2025
The sheer volume of new Common Vulnerabilities and Exposures (CVEs) reported in 2025 underscores a worrying trend: attackers are finding and exploiting weaknesses at an accelerated pace. This surge isn’t just about quantity; it’s about the increased sophistication and impact of these vulnerabilities. Many of the newly identified exploits leverage zero-day attacks, underscoring the pressing need for proactive defense mechanisms and rapid response capabilities. The focus here is on those that have moved beyond theoretical risk to active compromise, impacting organizations globally.
Understanding “Exploited in the Wild” Severity
“Exploited in the wild” signifies a critical escalation for any vulnerability. It means that malicious actors are actively using these flaws to compromise systems, steal data, disrupt operations, or gain unauthorized access. This moves a vulnerability from a potential threat to an immediate and direct danger, demanding immediate attention and mitigation. Prioritizing these exploited vulnerabilities becomes the cornerstone of an effective cybersecurity strategy.
The Top 10 High-Risk Vulnerabilities of 2025 Actively Exploited
While the full list from CybersecurityNews.com is exhaustive, the following represent the most impactful and frequently exploited vulnerabilities observed in the first half of 2025. Each entry provides a brief description, its significance, and crucial remediation actions.
1. Critical Remote Code Execution in Cloud Platforms
This category encompasses several vulnerabilities found in widely used cloud infrastructure components, allowing attackers to execute arbitrary code with elevated privileges. These often target core services or underlying orchestration layers.
- Example CVE (Hypothetical for 2025 context): CVE-2025-0123 (Cloud Hypervisor RCE)
- Impact: Complete control over cloud instances, data exfiltration, service disruption, and lateral movement across cloud environments.
Remediation Actions:
- Regular Patching: Implement a rigorous patch management schedule for all cloud services and underlying infrastructure components.
- Least Privilege: Enforce strict adherence to the principle of least privilege for all cloud accounts and services.
- Network Segmentation: Isolate critical cloud resources using network segmentation to limit the blast radius of any compromise.
- Vulnerability Scanning: Regularly scan cloud environments for misconfigurations and known vulnerabilities using Cloud Security Posture Management (CSPM) tools.
- Endpoint Protection: Ensure robust endpoint detection and response (EDR) solutions are deployed on all cloud instances.
2. Supply Chain Compromises via Open-Source Libraries
Attackers continue to inject malicious code into popular open-source libraries, which are then unknowingly integrated into countless applications. These compromises are difficult to detect and have a wide-reaching impact.
- Example CVE (Hypothetical for 2025 context): CVE-2025-0456 (Malicious Package Injection)
- Impact: Backdoors, data theft, remote code execution within applications using the compromised libraries.
Remediation Actions:
- Software Composition Analysis (SCA): Utilize SCA tools to continuously monitor and assess the security of open-source components used in your applications.
- Dependency Verification: Implement strict internal policies for verifying the integrity and authenticity of third-party libraries.
- Supply Chain Security Platforms: Leverage platforms designed to scrutinize and secure software supply chains.
- Repository Hardening: Configure artifact repositories securely and scan packages before deployment.
3. Authentication Bypass in Identity Management Systems
Flaws in single sign-on (SSO) solutions and other identity management platforms allow attackers to bypass authentication mechanisms and gain unauthorized access to corporate resources.
- Example CVE (Hypothetical for 2025 context): CVE-2025-0789 (SSO Auth Bypass)
- Impact: Unauthorized access to critical systems, sensitive data, and potential for complete system compromise.
Remediation Actions:
- Multi-Factor Authentication (MFA): Enforce strong MFA for all critical systems and user accounts.
- Regular Audits: Conduct regular security audits of identity management configurations and logs.
- Patch Identity Platforms: Prioritize patching for identity providers and related services.
- Session Management: Ensure robust session management with short session durations and proper invalidation.
4. Zero-Day Exploits in Popular Enterprise Applications
Attackers are continually discovering and weaponizing zero-day vulnerabilities in widely deployed enterprise software (CRM, ERP, collaboration tools), leading to immediate compromise as organizations often have no patch available.
- Example CVE (Hypothetical for 2025 context): CVE-2025-1011 (ERP Zero-Day)
- Impact: Data breaches, operational disruption, financial fraud, and reputational damage.
Remediation Actions:
- Application Segmentation: Isolate critical enterprise applications from the broader network.
- WAF Protection: Deploy Web Application Firewalls (WAFs) to detect and block exploitation attempts.
- Behavioral Monitoring: Implement User and Entity Behavior Analytics (UEBA) to detect anomalous activity that might indicate a zero-day attack.
- Threat Intelligence: Subscribe to reliable threat intelligence feeds to be alerted to emerging zero-days.
5. Vulnerabilities in Edge Computing Devices
As edge computing proliferates, vulnerabilities in IoT devices, industrial control systems (ICS), and other edge hardware provide new entry points for attackers to penetrate corporate networks.
- Example CVE (Hypothetical for 2025 context): CVE-2025-1314 (IoT Device RCE)
- Impact: Network infiltration, data exfiltration, operational disruption, physical damage in ICS environments.
Remediation Actions:
- Device Segmentation: Isolate edge devices on separate network segments.
- Firmware Updates: Ensure a robust process for keeping edge device firmware up-to-date.
- Strong Authentication: Implement strong, unique passwords and MFA where supported for edge devices.
- Network Monitoring: Continuously monitor network traffic from edge devices for unusual patterns.
6. Server-Side Request Forgery (SSRF) in API Gateways
SSRF vulnerabilities in API gateways or internal microservices allow attackers to force the server into making requests to internal or external resources, leading to information disclosure or data exfiltration.
- Example CVE (Hypothetical for 2025 context): CVE-2025-1617 (API Gateway SSRF)
- Impact: Access to internal systems, cloud metadata, sensitive files, and potentially remote code execution.
Remediation Actions:
- Input Validation: Implement rigorous input validation for all user-supplied URLs and parameters.
- Whitelist Approach: Use a whitelist of allowed domains and protocols for server-side requests.
- Principle of Least Privilege: Ensure the application or service making requests has minimal necessary permissions.
- Network Filtering: Employ network firewalls or security groups to block outgoing connections to internal resources from application servers.
7. Misconfigured Kubernetes Clusters
The complexity of Kubernetes often leads to misconfigurations, creating vulnerabilities for privilege escalation, container escapes, and unauthorized access to cluster resources.
- Example CVE (Hypothetical for 2025 context): CVE-2025-1920 (K8s Role Bindings Exploit)
- Impact: Full cluster compromise, data theft from containers, denial of service, and cryptojacking.
Remediation Actions:
- Security Best Practices: Adhere strictly to Kubernetes security best practices (CIS Benchmarks).
- RBAC Enforcement: Implement strong Role-Based Access Control (RBAC) with least privilege.
- Container Image Scanning: Regularly scan container images for known vulnerabilities before deployment.
- Runtime Security: Deploy container runtime security solutions to detect and prevent anomalous behavior.
8. Exploitable Logic Flaws in Business Process Automation
As more business processes become automated, attackers are targeting logic flaws in these systems to manipulate outcomes, commit fraud, or gain unauthorized access by circumventing intended workflows.
- Example CVE (Hypothetical for 2025 context): CVE-2025-2223 (Business Logic Manipulation)
- Impact: Financial fraud, unauthorized transactions, data manipulation, competitive advantage theft.
Remediation Actions:
- Thorough Testing: Conduct extensive security testing, including penetration testing and abuse case analysis, on all automated workflows.
- Input Validation: Implement comprehensive input validation at every stage of the business process.
- Audit Trails: Maintain detailed, immutable audit logs for all automated actions and changes.
- Human Oversight: Incorporate human review steps for critical transactions or decisions within automated workflows.
9. Cross-Site Scripting (XSS) in SaaS Platforms
Persistent and reflected XSS vulnerabilities within widely used Software-as-a-Service (SaaS) platforms allow attackers to compromise user sessions, steal credentials, or deface websites and applications.
- Example CVE (Hypothetical for 2025 context): CVE-2025-2526 (SaaS XSS)
- Impact: Session hijacking, data theft, credential compromise, drive-by downloads, website defacement.
Remediation Actions:
- Output Encoding: Ensure all user-supplied input displayed on web pages is properly output encoded.
- Content Security Policy (CSP): Implement a strict CSP to restrict the sources from which content can be loaded.
- Input Validation: Filter and validate all user input to remove potentially malicious scripts.
- Security Headers: Utilize security headers like X-XSS-Protection or X-Content-Type-Options.
10. Exploitation of Old, Unpatched Network Appliances
Despite numerous warnings, many organizations still run outdated and unpatched network devices (routers, firewalls, load balancers), providing easy entry points for attackers into the internal network.
- Example CVE (Hypothetical for 2025 context): CVE-2025-2829 (Router Firmware Backdoor)
- Impact: Network infiltration, man-in-the-middle attacks, denial of service, establishment of persistent access.
Remediation Actions:
- Asset Inventory: Maintain an accurate and up-to-date inventory of all network appliances.
- Regular Patching: Establish and enforce a strict patch management policy for all network hardware and firmware.
- Network Hardening: Configure network devices according to security best practices, disabling unnecessary services.
- Network Access Control (NAC): Implement NAC to restrict unauthorized devices from connecting to the network.
- Segmentation: Segment networks to limit the lateral movement of an attacker who breaches a network appliance.
Tools for Detection and Mitigation
Proactive defense requires the right tools to identify, triage, and mitigate vulnerabilities. Here are some essential categories and example tools:
| Tool Name | Purpose | Link |
|---|---|---|
| Nessus | Vulnerability Scanning, Configuration Audits | Tenable Nessus |
| OWASP ZAP | Web Application Security Testing, DAST | OWASP ZAP |
| Snyk | SCA, SAST, DAST, Container Security | Snyk |
| Wazuh | SIEM, EDR, FIM, Vulnerability Detection | Wazuh |
| Cloud Security Posture Management (CSPM) solutions (e.g., Wiz, Orca Security) | Cloud Misconfiguration Detection, Compliance | Wiz |
| Kubernetes Security Platforms (e.g., Falco, Aquasec) | Container Runtime Security, Kubernetes Auditing | Falco |
Moving Forward: A Proactive Stance
The cybersecurity challenges of 2025 are formidable, characterized by a rapid increase in disclosed vulnerabilities and the immediate weaponization of critical flaws. Relying solely on reactive measures is no longer sufficient. Organizations must adopt a proactive, layered security approach that prioritizes swift patching, robust configuration management, continuous monitoring, and employee education. Understanding these top exploited vulnerabilities provides a crucial roadmap for strengthening defenses and building true resilience against the evolving threat landscape.





