Stealthy CastleLoader Malware Attacking US Government Agencies and Critical Infrastructure
Stealthy CastleLoader Malware: An Evolving Threat to US Government and Critical Infrastructure
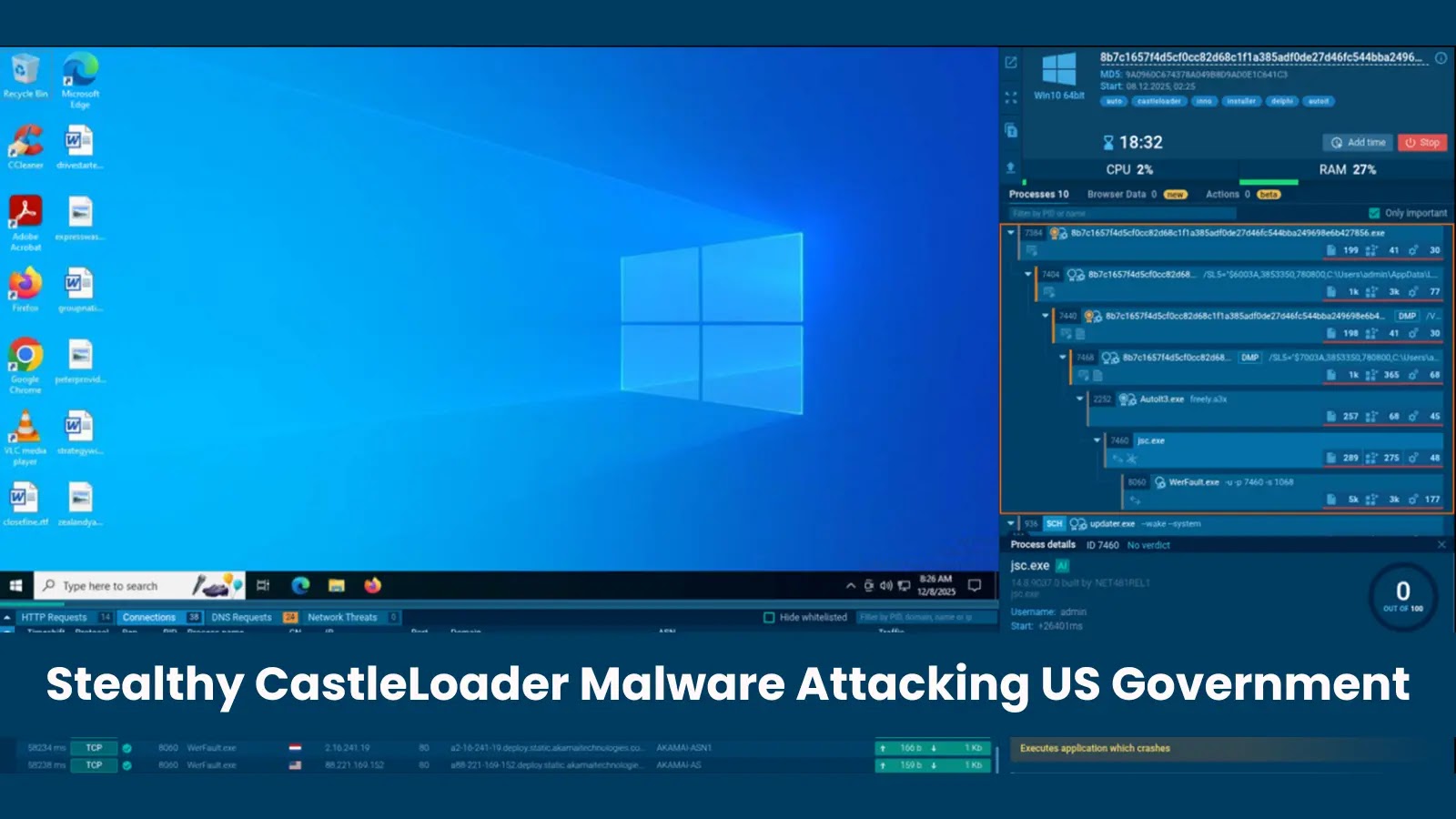
The cybersecurity landscape has recently witnessed the emergence of a highly sophisticated and stealthy malware loader known as CastleLoader. First identified in early 2025, this formidable threat has been leveraged as the initial access point in several coordinated attacks, specifically targeting US government agencies and critical infrastructure organizations. Its ability to bypass conventional security measures and establish a persistent foothold makes it a significant concern for national security and economic stability.
The scope of CastleLoader’s targeting is broad, encompassing federal agencies, information technology firms, logistics companies, and essential infrastructure providers. This wide-ranging campaign underscores the adaptability and strategic intent behind its deployment, suggesting a well-resourced and advanced persistent threat (APT) actor at play. Understanding CastleLoader’s characteristics and its operational tactics is paramount for defenders to effectively mitigate its impact.
What is CastleLoader? Dissecting a Stealthy Threat
CastleLoader is not the final payload but rather a sophisticated initial access loader. Its primary function is to discreetly establish a beachhead within a compromised network, prepare the environment for subsequent stages of an attack, and download additional malicious payloads. What distinguishes CastleLoader is its emphasis on stealth and evasion, making detection particularly challenging.
- Evasive Techniques: CastleLoader employs various advanced techniques to avoid detection by antivirus software and intrusion detection systems. This includes code obfuscation, anti-analysis features, and leveraging legitimate system processes to mask its activities.
- Modular Architecture: Its modular design allows threat actors to dynamically load different plugins or follow-up malware depending on the target environment and the objectives of the attack. This flexibility makes it a versatile tool in an attacker’s arsenal.
- Persistence Mechanisms: Once inside a network, CastleLoader focuses on establishing robust persistence mechanisms to ensure continued access, even after system reboots or security cleanups. This often involves manipulating registry keys, scheduled tasks, or exploiting legitimate system services.
- Targeted Deployment: The precision of its deployment against high-value targets such as government entities and critical infrastructure suggests a meticulous reconnaissance phase and potentially tailored variants for specific environments.
CastleLoader’s Impact: Compromising National Security and Essential Services
The targeting of US government agencies and critical infrastructure organizations by CastleLoader presents a multi-faceted risk:
- Espionage and Data Exfiltration: Gaining access to federal agencies can lead to the theft of sensitive government data, intelligence, and classified information, compromising national security.
- Disruption of Essential Services: Attacks on critical infrastructure, including energy grids, water treatment facilities, and transportation networks, could lead to widespread service disruption, economic paralysis, and even public safety hazards.
- Supply Chain Attacks: The compromise of IT firms and logistics companies could be utilized as a stepping stone for further supply chain attacks, allowing threat actors to inject malicious code into trusted software or hardware, affecting numerous downstream customers.
- Financial and Reputational Damage: Beyond direct operational impacts, successful attacks can result in significant financial losses for affected organizations due to remediation efforts, regulatory fines, and long-term damage to public trust and reputation.
Remediation Actions: Fortifying Defenses Against CastleLoader
Given the sophisticated nature of CastleLoader, a multi-layered and proactive cybersecurity strategy is essential for defense. Organizations, especially those within government and critical infrastructure sectors, must implement rigorous measures to prevent, detect, and respond to such threats.
- Strengthen Endpoint Security: Deploy advanced endpoint detection and response (EDR) solutions with behavioral analysis capabilities to identify and block unusual or malicious activities indicative of CastleLoader. Ensure all endpoints are running up-to-date antivirus definitions.
- Implement Network Segmentation: Segment networks to limit the lateral movement of malware if an initial breach occurs. Critical systems should be isolated from less sensitive parts of the network.
- Vulnerability Management and Patching: Regularly scan for and patch all known vulnerabilities across operating systems, applications, and network devices. While no specific CVE has been publicly attributed directly to CastleLoader’s initial infection vector, many loaders leverage unpatched systems. Proactive patching reduces the attack surface.
- Enhanced Email and Web Security: Implement robust email filtering, sandboxing, and web content filtering to prevent phishing attempts and malicious downloads, which are common initial infection vectors for loaders.
- Principle of Least Privilege: Enforce the principle of least privilege for all users and systems. Restrict administrative rights and access to only what is absolutely necessary for job functions.
- Multi-Factor Authentication (MFA): Mandate MFA for all user accounts, especially for remote access and access to critical systems, to prevent unauthorized access even if credentials are stolen.
- Employee Security Awareness Training: Conduct regular and comprehensive training for all employees on identifying phishing attempts, social engineering tactics, and safe computing practices.
- Regular Backups and Disaster Recovery: Implement a robust data backup strategy with offsite storage and test disaster recovery plans regularly to ensure business continuity in case of a successful attack.
- Threat Intelligence Integration: Subscribe to and integrate high-fidelity threat intelligence feeds to stay informed about emerging threats like CastleLoader and update security controls proactively.
Conclusion: A Call for Heightened Vigilance
The emergence of CastleLoader underscores the persistent and evolving threat landscape facing government agencies and critical infrastructure. Its stealthy nature and targeted deployment demand a proactive and adaptive defense posture. As threat actors continue to innovate, organizations must prioritize advanced security controls, maintain vigilant monitoring, and foster a strong security-first culture to safeguard against sophisticated malware campaigns like CastleLoader. Continuous investment in cybersecurity capabilities and collaboration across sectors are vital to protecting these essential digital assets.





