Hackers Use ‘rn’ Typo Trick to Impersonate Marriott in New Phishing Attack
Deceptive ‘rn’ Typo Trick Impersonates Marriott in New Phishing Onslaught
In the intricate landscape of cyber threats, attackers continuously evolve their tactics to compromise unsuspecting individuals and organizations. A recent and particularly insidious campaign highlights this evolution, leveraging a subtle typographic trick known as homoglyph attacks or typosquatting. This technique, which preys on the visual similarities between characters in modern fonts, has been observed impersonating major brands like Marriott International and Microsoft, putting countless users at risk.
The Anatomy of a Homoglyph Phishing Attack
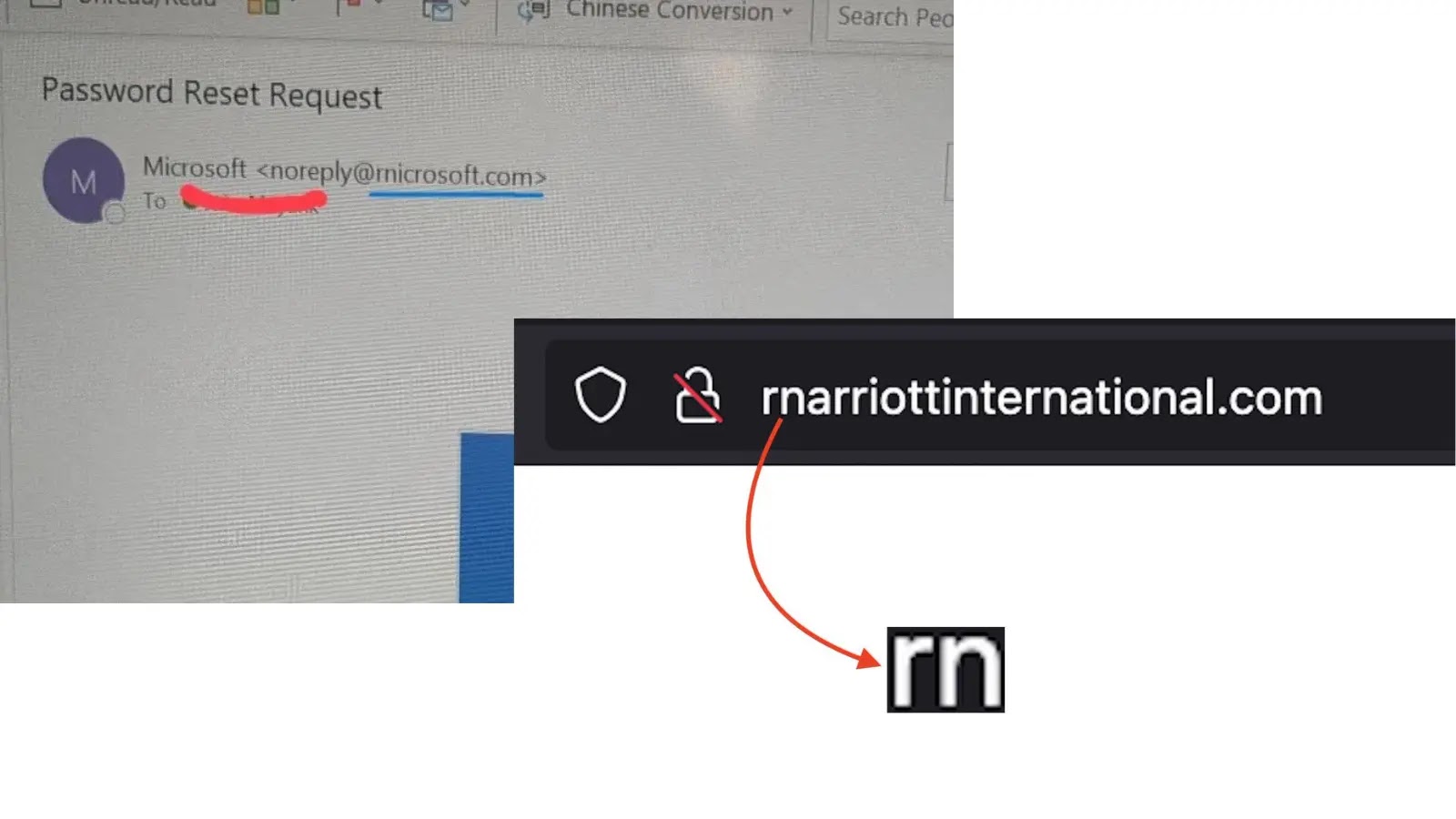
At the core of this sophisticated phishing scheme is the exploitation of visual ambiguity. Hackers are registering malicious domains that cunningly substitute the letter “m” with the combination “rn” (r + n). For example, a legitimate domain like marriott.com could be mirrored by a deceptive domain such as rnarrlott.com. While this difference is immediately apparent when scrutinized, in a quick glance, or when rendered in certain fonts or smaller sizes, the resemblance is startlingly similar.
This subtle alteration makes it incredibly difficult for the average user to distinguish between a genuine website and a fraudulent one. Once a user navigates to one of these fake sites, they are often prompted to enter sensitive information, such as login credentials, payment details, or personal data, which is then siphoned off by the attackers. The psychological impact is significant: users trust the visual cues, leading to a false sense of security.
This specific technique isn’t new; homoglyph attacks have been documented for years, often targeting financial institutions or popular online services. What makes this recent campaign notable is its scale and the specific brands targeted, indicating a calculated effort to maximize potential victims by leveraging widely recognized and trusted entities.
Typosquatting and Homoglyph Attacks: A Deeper Dive
Typosquatting, also known as URL hijacking, is a form of cybercrime where attackers register domain names that are misspellings of popular legitimate websites. The goal is to profit from users making typographical errors when entering URLs into a web browser. These squatting domains often host malware, phishing pages, or unwanted advertisements.
Homoglyph attacks are a specialized form of typosquatting. A homoglyph is a character that looks like another character. These attacks take advantage of the visual similarities between different characters or character combinations. For instance:
- The letter ‘m’ looking like ‘rn’ (as seen in the Marriott attack).
- Using a Cyrillic ‘a’ which looks identical to a Latin ‘a’.
- Substituting ‘l’ (lowercase L) for ‘I’ (uppercase i).
The danger lies in the attacker’s ability to create a near-perfect visual clone of a legitimate URL. Once a user clicks a malicious link from an email or a seemingly legitimate source, their browser displays a URL that appears authentic, leading them into a trap.
Remediation Actions and Protective Measures
Combating sophisticated phishing campaigns requires a multi-layered approach, combining user education with robust technical controls. For individuals and organizations, proactive measures are paramount:
- User Education and Awareness: The first line of defense is a well-informed user base. Train employees and educate customers about the dangers of phishing and homoglyph attacks. Emphasize scrutinizing URLs, especially before entering credentials.
- Verify URLs Meticulously: Before clicking any link or entering sensitive information, always hover over the URL to see the full address. Look for subtle misspellings, substitute characters, or unusual domain extensions.
- Bookmark Official Sites: Encourage users to bookmark legitimate websites for services like Marriott or Microsoft and access them directly from their bookmarks, rather than clicking links in emails.
- Multi-Factor Authentication (MFA): Implement MFA across all critical accounts. Even if credentials are compromised, MFA adds another layer of security, significantly reducing the likelihood of unauthorized access.
- Email Security Solutions: Deploy advanced email security gateways that can detect and block phishing emails, including those leveraging homoglyph domains, before they reach user inboxes.
- DNS Filtering and Web Security: Utilize DNS filtering services and web proxies that can block access to known malicious domains, including typosquatted ones.
- Domain Monitoring: Organizations should actively monitor for typosquatted domains that target their brand. This allows for proactive action, such as issuing cease and desist letters or pursuing domain seizure.
- Regular Security Audits: Conduct regular penetration testing and vulnerability assessments to identify potential weaknesses in your systems that attackers could exploit. While this attack doesn’t have a direct CVE, it represents a social engineering vulnerability.
Tools for Detection and Mitigation
While homoglyph attacks primarily exploit human vulnerabilities, several tools can aid in detection, prevention, and response:
| Tool Name | Purpose | Link |
|---|---|---|
| PhishTank | Community-based phishing URL verification | https://www.phishtank.com/ |
| Google Safe Browsing | Identifies unsafe websites, including phishing pages | https://safebrowsing.google.com/ |
| URLScan.io | Analyzes and screenshots websites for malicious activity | https://urlscan.io/ |
| Proofpoint / Mimecast | Advanced Email Security Gateways (AES) | https://www.proofpoint.com/ / https://www.mimecast.com/ |
| DomainTools Iris | Domain intelligence and monitoring for brand protection | https://www.domaintools.com/products/iris-investigate/ |
Stay Vigilant: The Ever-Evolving Threat Landscape
The ‘rn’ typo trick targeting Marriott and Microsoft customers serves as a stark reminder that cyber attackers are relentlessly innovativ. Their methods often blend technical prowess with a deep understanding of human psychology. As cybersecurity professionals, our role extends beyond implementing technical controls; it encompasses fostering a culture of perpetual vigilance and critical thinking among all users. By understanding these subtle yet potent deceptions, we can collectively enhance our defenses against the persistent threat of phishing.





