Threat Actors Fake BSODs and Trusted Build Tools to Bypass Defenses and Deploy DCRat
Deceptive Tactics: How Threat Actors Leverage Fake BSODs and Trusted Tools to Deploy DCRat
The landscape of cyber threats continues its relentless evolution, with threat actors constantly refining their methods to bypass robust security measures. A recent, particularly insidious campaign, tracked as PHALT#BLYX, highlights this trend by exploiting human trust and system vulnerabilities through a sophisticated blend of social engineering and technical evasion. This operation specifically targets hospitality businesses, demonstrating a calculated approach to compromise sensitive data and disrupt critical operations.
PHALT#BLYX Campaign: A Deep Dive into Deceptive Delivery
The PHALT#BLYX campaign commences with a highly convincing social engineering tactic: deceptive reservation cancellation emails. These emails are crafted to instill a sense of urgency and legitimacy, preying on the administrative tasks common within the hospitality sector. Unsuspecting employees, believing they are managing routine cancellations, are manipulated into initiating what appears to be a legitimate process but is, in reality, the first step in a multi-stage attack. The end goal? The deployment of DCRat, a potent Remote Access Trojan (RAT), allowing attackers extensive control over compromised systems.
The critical element of this initial phase lies in its ability to
- appear benign, ensuring the employee executes malicious code without immediate suspicion. This bypasses many perimeter defenses that rely on identifying overtly malicious attachments or links.
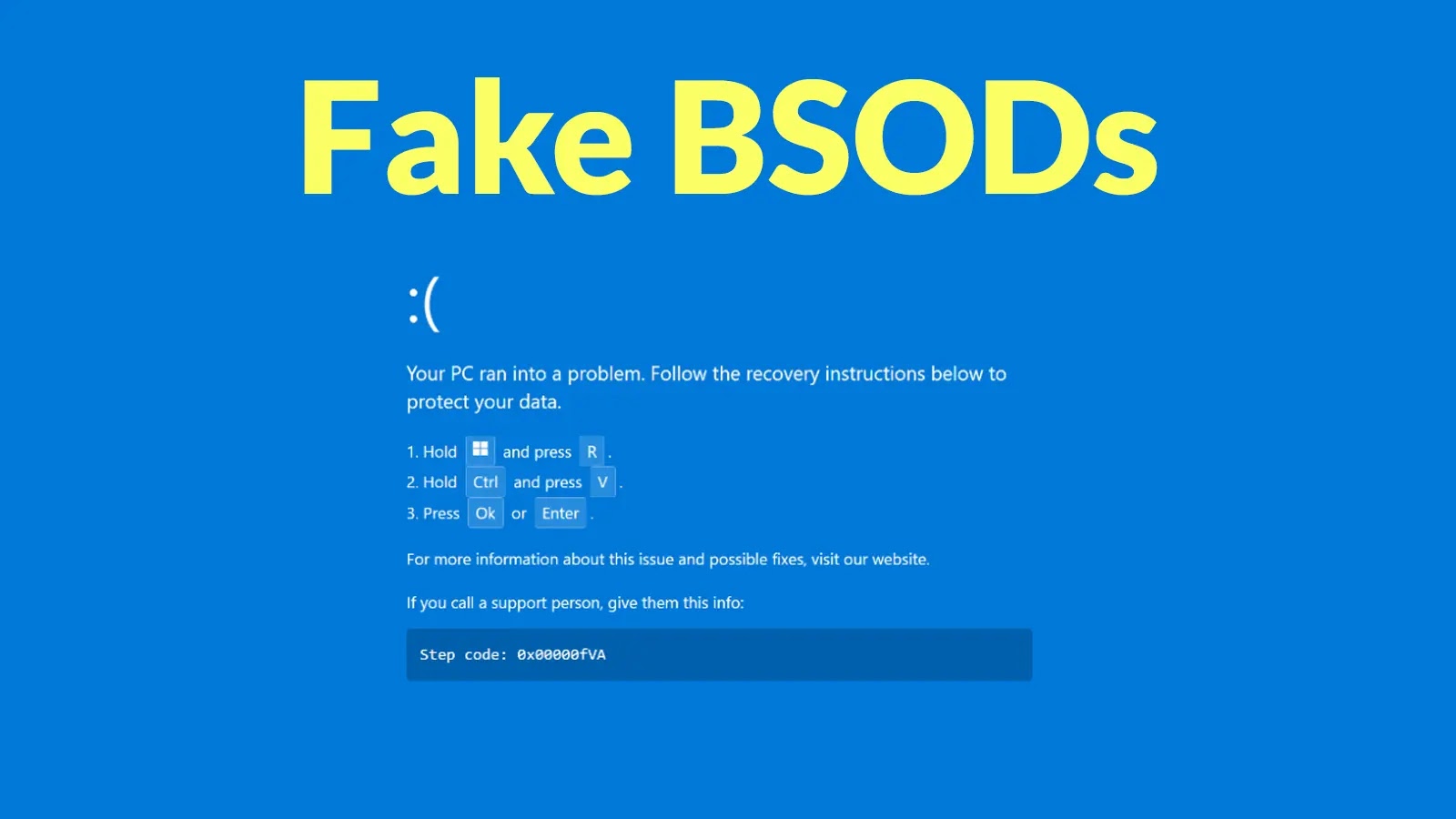
The Illusion of Error: Fake Blue Screen of Death (BSOD)
Following the initial compromise, the PHALT#BLYX campaign employs a cunning psychological warfare tactic: a fake Blue Screen of Death (BSOD). Instead of being an actual system crash, this is a simulated error message designed to panic the user and divert their attention. While the user is occupied with troubleshooting what they perceive as a critical system failure, the malware quietly executes its payload in the background. This misdirection is highly effective, as a BSOD typically elicits an immediate reactive response, drawing focus away from ongoing malicious activity.
The fake BSOD also serves to install a sense of inevitability or helplessness, making the victim less likely to investigate unusual processes or network activity immediately after the “crash.”
Trusted Tools, Malicious Intent: Abusing Microsoft Build Tools
One of the most concerning aspects of the PHALT#BLYX campaign is its strategic abuse of legitimate and trusted Microsoft build tools. Threat actors are increasingly leveraging these tools – often pre-installed or easily accessible within an enterprise environment – to carry out malicious operations. By using tools like MSBuild.exe or similar development utilities, the attackers can:
- Evade Detection: Security solutions often whitelist or grant elevated privileges to these legitimate executables, making their malicious use significantly harder to detect.
- Blend In: The activities generated by these tools appear normal within network traffic and system logs, masquerading as legitimate development or system processes.
- Execute Malicious Code: These tools can be coerced into compiling and executing malicious code, acting as a trusted conduit for malware delivery and persistence.
This tactic highlights a significant challenge for cybersecurity professionals: distinguishing between legitimate system functions and their malicious exploitation. The underlying principle is simple but effective: hide in plain sight.
DCRat: The Ultimate Goal
At the core of the PHALT#BLYX operation is the deployment of DCRat. This Remote Access Trojan is a versatile and dangerous tool for attackers. Once DCRat establishes a foothold, threat actors gain extensive control over the compromised system, including:
- Remote desktop access and control.
- Keylogging capabilities to steal credentials.
- File exfiltration and manipulation.
- Installation of additional malware.
- System information gathering.
The persistent presence of DCRat allows attackers to maintain long-term access, escalate privileges, and move laterally across the network, potentially leading to widespread data breaches or ransomware deployment.
Remediation Actions for Enhanced Security
Defending against sophisticated campaigns like PHALT#BLYX requires a multi-layered approach focusing on both technical controls and human education. Here are actionable steps organizations, particularly those in the hospitality sector, can take:
- Employee Training on Social Engineering: Conduct regular, realistic phishing simulations and provide comprehensive training on identifying deceptive emails, especially those related to common business operations like reservations or cancellations. Emphasize verification procedures for all unexpected requests.
- Endpoint Detection and Response (EDR): Implement robust EDR solutions that can monitor for anomalous behavior, even when legitimate tools are being abused. EDR can detect deviations from normal execution paths or unusual process spawning.
- Application Whitelisting/Control: Restrict the execution of unauthorized applications. While fully whitelisting all legitimate applications can be challenging, focus on critical systems and sensitive data environments.
- Principle of Least Privilege: Ensure users and applications operate with the minimum necessary permissions. This limits the damage an attacker can inflict even if they compromise an account or process.
- Network Segmentation: Isolate critical business systems and sensitive data. This prevents lateral movement should an attacker successfully breach one part of the network.
- Regular Backups: Maintain frequent and tested backups of all critical data, stored ઓફline or in immutable storage, to aid recovery in the event of a successful data compromise or ransomware attack.
- Threat Intelligence Integration: Stay updated with the latest threat intelligence, including indicators of compromise (IoCs) related to campaigns like PHALT#BLYX, to proactively identify and block attacks.
Tools for Detection and Mitigation
| Tool Name | Purpose | Link |
|---|---|---|
| Microsoft Defender for Endpoint | Advanced EDR capabilities, behavioral detection | https://www.microsoft.com/en-us/security/business/endpoint-security/microsoft-defender-for-endpoint |
| Cortex XDR | Cross-platform EDR, analytics, and threat prevention | https://www.paloaltonetworks.com/cortex/cortex-xdr |
| Mandiant Advantage | Threat intelligence and incident response | https://www.mandiant.com/advantage |
| PhishMe (Cofense) | Phishing simulation and security awareness training | https://cofense.com/product-services/phishme-platform/ |
Conclusion: Heightened Vigilance in a Complex Threat Landscape
The PHALT#BLYX campaign serves as a stark reminder that modern cyberattacks are rarely simplistic. They often combine sophisticated social engineering with technical ingenuity to exploit both human and system vulnerabilities. The use of fake BSODs to distract and trusted Microsoft build tools to evade detection represents a calculated strategy to deploy dangerous malware like DCRat. Businesses, especially those handling high volumes of customer interactions, must prioritize comprehensive employee training, robust endpoint security, and active threat intelligence to defend against these increasingly deceptive and potent threats.





