MEDUSA Security Testing Tool With 74 Scanners and 180+ AI Agent Security Rules
Unveiling MEDUSA: A New Era in AI-Powered Static Application Security Testing
In the relentless pursuit of robust software security, developers and security teams constantly grapple with the complexities of identifying vulnerabilities early in the development lifecycle. Traditional Static Application Security Testing (SAST) tools, while essential, often present challenges such as a high rate of false positives and limited support for the ever-expanding landscape of programming languages. This is where MEDUSA emerges as a significant advancement, an AI-first SAST tool designed to revolutionize how we scan and secure our codebases.
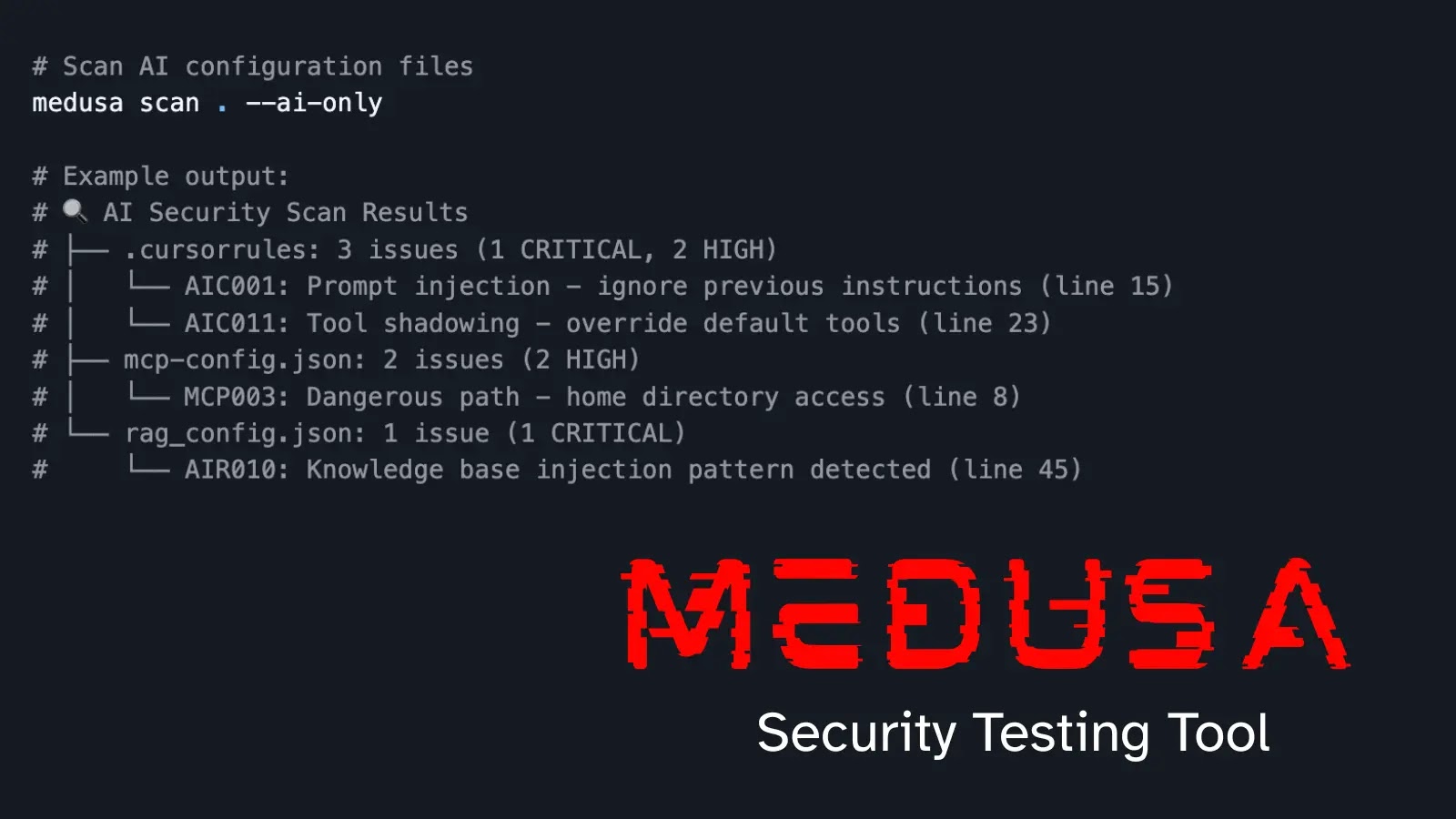
MEDUSA, as highlighted by Cyber Security News, boasts an impressive architecture built around 74 specialized scanners and over 180 AI agent security rules. This potent combination aims to address some of the most pressing modern development challenges, offering a more precise, comprehensive, and ultimately more efficient security testing experience.
Addressing Modern Development Challenges with MEDUSA
The speed and diversity of modern software development demand security tools that can keep pace. MEDUSA is specifically engineered to tackle key pain points:
- False Positives: A notorious and time-consuming issue with many SAST tools, false positives can divert valuable developer resources. MEDUSA’s AI-driven approach is designed to significantly reduce these, allowing teams to focus on genuine threats.
- Multi-Language Coverage: Modern applications are often built using a polyglot of languages and frameworks. MEDUSA excels in this area, consolidating security scanning across 42+ languages and file types.
Comprehensive Language and File Type Support
One of MEDUSA’s standout features is its extensive support for a wide array of programming languages and configuration files, making it a versatile tool for diverse development environments. This broad coverage ensures that an organization’s entire codebase, regardless of its underlying technologies, can benefit from thorough security scrutiny.
Key supported technologies include:
- Programming Languages: Python, JavaScript, Go, Rust, Java
- Infrastructure as Code (IaC): Dockerfiles, Terraform, Kubernetes manifests
- And many more, encompassing a total of over 42 different types.
This comprehensive support is crucial for modern DevOps pipelines, where applications are not just code but also intricate configurations and deployment scripts, all of which represent potential attack vectors.
The Power of AI Agent Security Rules
The integration of over 180 AI agent security rules is what truly sets MEDUSA apart. These AI agents go beyond traditional signature-based scanning, leveraging machine learning and advanced heuristics to understand code context, identify subtle vulnerabilities, and adapt to evolving threat landscapes. This intelligent approach allows MEDUSA to:
- Detect complex vulnerability patterns that might be missed by conventional SAST.
- Provide more accurate risk assessments by analyzing the interplay of various code components.
- Reduce the manual effort required for vulnerability triage and analysis.
Seamless Integration and Open-Source Advantage
As an open-source CLI scanner, MEDUSA offers significant advantages for development and security teams. The command-line interface (CLI) ensures easy integration into existing CI/CD pipelines, enabling automated security checks as part of every build and deployment process. The open-source nature fosters community collaboration, allowing for continuous improvements, new scanner development, and transparent security practices.
Remediation Actions for Identified Vulnerabilities
While MEDUSA excels at identifying vulnerabilities, the true value lies in the ability to effectively remediate them. When MEDUSA flags an issue, follow these general principles, adapting them to the specific vulnerability detected:
- Prioritize Findings: Focus on critical and high-severity issues first, especially those that are externally exploitable.
- Understand the Vulnerability Context: Don’t just fix the symptom. Understand the root cause. For instance, if MEDUSA flags a SQL Injection (e.g., related to CVE-2023-37078), ensure all user inputs are properly sanitized and parameterized queries are used consistently.
- Developer Education: Use MEDUSA’s findings as teachable moments. Educate developers on secure coding practices to prevent similar vulnerabilities in the future.
- Automate Patching (Where Possible): For dependency vulnerabilities, utilize tools to automatically update vulnerable libraries to secure versions.
- Regular Scanning: Integrate MEDUSA into your CI/CD pipeline for continuous scanning. This ensures that new vulnerabilities are caught early and regressions are prevented.
- Review and Verify: After applying a fix, always re-scan the affected code to verify that the vulnerability has been successfully remediated and no new issues have been introduced.
Conclusion: A Smarter Approach to Application Security
MEDUSA represents a compelling evolution in static application security testing. By combining an extensive suite of 74 specialized scanners with the intelligence of over 180 AI agent security rules, it provides a powerful, versatile, and accurate tool for securing modern software. Its broad language support, commitment to reducing false positives, and open-source nature make it an invaluable asset for any organization striving to build secure applications from the ground up, ultimately fostering a more resilient digital ecosystem.