VLAN Segmentation for Data Security
VLANs for Network Segmentation and Data Security Best Practices for VLAN Segmentation
In today’s dynamic network landscape, ensuring robust data security and efficient network management is paramount. VLANs offer a powerful solution, enabling network segmentation that enhances both performance and security. This article explores the best practices for VLAN segmentation, providing insights into how to effectively divide a network into smaller, more manageable segments to safeguard sensitive data and optimize network performance.
Understanding VLANs and Network Segmentation
What are VLANs?
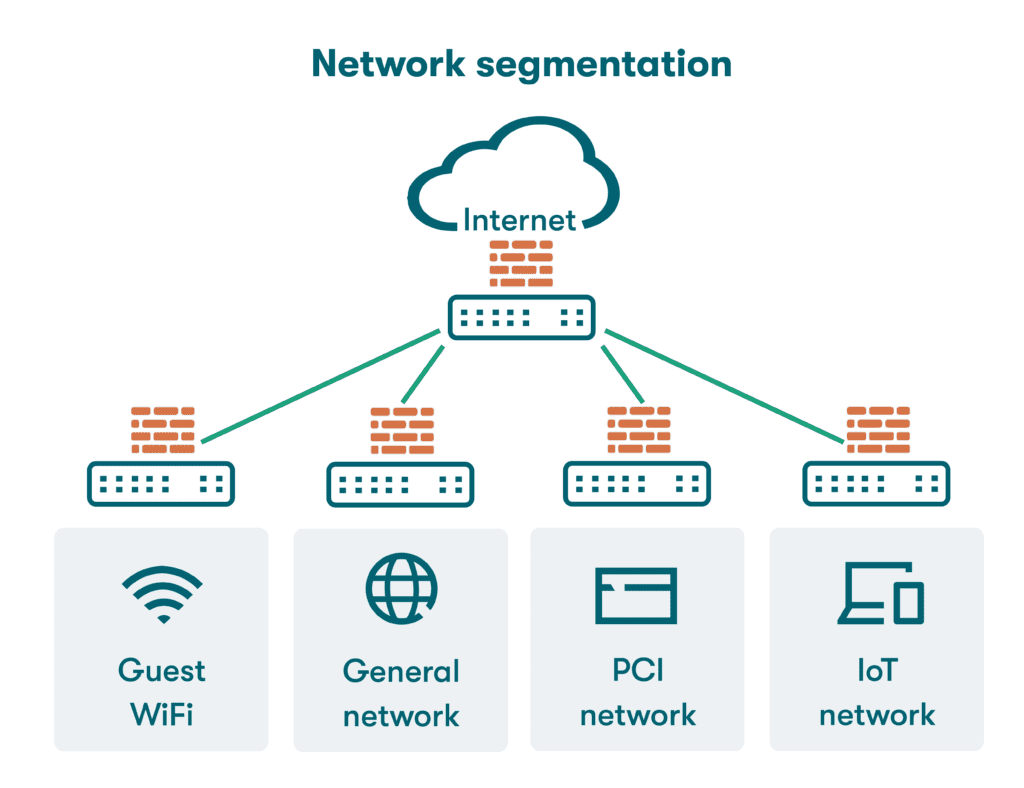
VLANs, or virtual local area networks, are a logical segmentation technique that divides a physical network into multiple, isolated broadcast domains, creating a secure network environment. Unlike physical segmentation, which requires separate hardware, VLANs achieve network segmentation through software configuration. Each VLAN operates as if it were its own independent network, allowing network administrators to segment networks without the constraints of physical cabling. VLANs utilize a VLAN tag to differentiate network traffic, ensuring that data is only delivered to network devices within the same VLAN. This logical segmentation simplifies network administration and improves network efficiency, particularly in a virtual network environment.
Importance of Network Segmentation
Network segmentation is a critical security strategy in modern network architecture. By dividing a network into smaller, isolated network segments, organizations can limit the impact of security threats. Network segmentation helps to contain breaches, preventing attackers from moving laterally across the entire network. This approach also allows for the implementation of granular security policies, tailoring security measures to specific parts of the network. Furthermore, network segmentation improves network performance by reducing network congestion and optimizing network traffic flow within each network segment.
How VLANs Enhance Network Security
VLANs significantly enhance network security by providing a robust network segmentation approach. By isolating sensitive data within specific VLANs, organizations can restrict access and minimize the risk of unauthorized access. VLAN configuration allows network administrators to implement stricter security policies for each network segment, enhancing the overall security posture of the secure network. Additionally, VLANs simplify network monitoring, making it easier to detect and respond to security incidents inside the network. Implementing VLAN segmentation is a best practice for any organization looking to improve security and manage network risks effectively.
Best Practices for VLAN Configuration
Designing Effective VLANs
Designing effective VLANs is crucial for achieving optimal network segmentation and enhanced network performance. When segmenting networks, start by identifying distinct user groups or device types that require isolation, which is a critical step in the segmentation method. Assign each group to a separate VLAN to limit broadcast traffic and enhance network security. It’s a best practice to create a management VLAN for network devices to ensure secure access and management. Avoid creating a single, large flat network; instead, segment a network into smaller, manageable network segments. This approach simplifies network administration and improves network efficiency as the network grows. Proper VLAN configuration also means considering future scalability and ease of management.
Implementing Security Policies
Implementing robust security policies is essential to leverage the full potential of VLANs for network security. Each VLAN should have tailored security measures that restrict access to sensitive data and network resources. Utilize access control lists (ACLs) and firewall rules to control network traffic between VLANs, preventing unauthorized access and potential security threats inside the network. Network administrators should regularly review and update security policies to address new vulnerabilities and evolving threats. Properly configured VLANs, along with well-defined security policies, significantly enhance security posture and protect against internal and external threats, ensuring a secure computer network.
Utilizing VLAN Tags for Traffic Management
VLAN tags are fundamental to managing network traffic effectively in a VLAN environment. The VLAN tag, inserted into the Ethernet frame, allows network devices to identify which VLAN the traffic belongs to. This ensures that network traffic is correctly routed to the appropriate network segment, improving network performance and reducing network congestion. VLAN trunking protocols, such as 802.1Q, enable multiple VLANs to share a single physical network connection. Proper implementation of VLAN tags and trunking protocols ensures efficient use of network resources and simplifies network management. This approach not only improves network performance but also enhances network security by isolating network traffic within each virtual local area network and implementing robust security controls.
Improving Network Performance with VLAN Segmentation
Enhancing Network Efficiency
To significantly enhance network efficiency, consider implementing VLAN segmentation to divide a network into smaller, manageable network segments. This is a best practice for reducing network congestion and improving overall network performance. With VLANs, network administrators can logically segment a network without the need for physical segmentation, optimizing network traffic flow within the network. Each virtual local area network operates independently, ensuring that network resources are used efficiently. Implementing VLAN segmentation can lead to improved network performance and reduced latency, enhancing the user experience inside the network.
Managing Network Traffic Across Segments
Effective management of network traffic across network segments is crucial for maintaining a high-performing network. VLAN configuration allows for the application of specific security policies and traffic-shaping rules to each virtual local area. Using VLAN tags, network devices can accurately route network traffic to the correct network segment, reducing unnecessary broadcast traffic. Proper VLAN segmentation also helps in prioritizing critical applications, ensuring they receive the necessary bandwidth. This approach provides improved network control and visibility, allowing network administrators to effectively manage network resources and maintain optimal network efficiency within the logical network.
Monitoring and Adjusting Network Segments
Continuous network monitoring is essential to ensure that VLAN segmentation is effectively improving network performance and security within the network. Network administrators should regularly monitor network traffic patterns within each virtual local area network to identify potential bottlenecks or security threats. By analyzing network performance metrics, adjustments can be made to VLAN configuration to optimize network traffic flow and improve network efficiency. Regular monitoring also helps in identifying unusual activity that could indicate a security breach inside the network. This proactive approach ensures that VLANs continue to provide enhanced network security and performance, adapting to changing network needs.
Challenges in VLAN Segmentation
Common Issues Faced by Network Administrators
Network administrators often face several challenges when implementing VLAN segmentation. One common issue is the complexity of VLAN configuration, especially in large, complex networks, which can hinder effective network access. Ensuring that VLAN tags are correctly configured across all network devices can be time-consuming and prone to errors. Another challenge is managing network traffic between VLANs, as improper configuration of routing and security policies can lead to network congestion or security vulnerabilities in the secure network. Additionally, maintaining proper documentation of VLAN assignments and configurations is crucial for effective network management but is often overlooked. These challenges highlight the need for careful planning and expertise in VLAN segmentation, especially to protect against potential data breaches.
Strategies for Overcoming Segmentation Challenges
To overcome the challenges of VLAN segmentation, network administrators should adopt a systematic approach. Start by thoroughly planning the network segmentation strategy, clearly defining the purpose of each virtual local area network and its associated security policies. Utilize network management tools to automate VLAN configuration and monitoring, reducing the risk of human error. Regularly review and update VLAN configurations to ensure they align with the evolving network needs and security threats, particularly in the context of potential data breaches. Training network administrators on best practices for VLAN segmentation is also crucial for ensuring successful implementation and management within the data center. By adopting these strategies, organizations can effectively manage network complexity and enhance security posture.
Future Trends in VLAN Segmentation
The future of VLAN segmentation is evolving with advancements in network technology like SDN and cloud-based network management. Software-defined networking (SDN) is playing an increasing role, allowing for more dynamic and automated VLAN configuration within the data center. Cloud-based network management solutions are also becoming more prevalent, simplifying VLAN management and providing greater scalability. Security is an increasing focus, with advanced threat detection and prevention capabilities being integrated into VLAN architectures. As networks continue to grow and become more complex, VLAN segmentation will remain a critical strategy for improving network performance, enhancing security, and simplifying network administration. By staying abreast of these trends, organizations can leverage the full potential of VLANs to secure their network inside and out.
How does logical segmentation using VLANs help divide a large network into smaller parts?
Logical segmentation via VLANs is an approach that divides a network at a data link layer, allowing a physical network to be divided into multiple logical networks. By assigning devices to one VLAN or many VLANs, administrators can split a larger network into smaller subnetworks so that different parts of the network operate independently, reducing broadcast domains and improving security and performance.
What role does network management play when you network into subnetworks or smaller VLANs?
Effective network management is required to plan VLAN IDs, routing between VLANs, and policies that control how traffic flows inside each VLAN. Centralized tools simplify assigning users or devices to a VLAN, monitoring traffic flow across the network, and enforcing access controls so that devices within the same physical network are grouped logically while minimizing misconfiguration and security issues.
Can VLAN segmentation prevent devices within the same physical network from being exposed to the entire network?
Yes. When the network is divided into VLANs, devices assigned to a VLAN cannot directly communicate with devices in other VLANs unless routing is explicitly provided, reducing the risk that hosts within the same physical network are exposed to the entire network. This isolation limits lateral movement and is useful for meeting compliance like payment card industry data security requirements when paired with proper controls.
How do VLANs support compliance with payment card industry data security standards?
VLAN segmentation can isolate cardholder data environments by creating a dedicated VLAN for systems that process or store payment card information. By segmenting the network into subnetworks, organizations can restrict which systems can access card industry data security scope, simplifying audits and reducing the number of systems that must meet the card industry data security standard.
What security issues remain when you segment a network into multiple logical VLANs?
Segmentation reduces many risks but does not eliminate them. Misconfigured inter-VLAN routing, weak ACLs, unprotected trunk links, or VLAN hopping attacks can expose traffic across the network. Proper network management, strict access controls, monitoring, and zero trust network principles are needed so segmentation is effective against security issues.
How does traffic flow inside each VLAN and why is it important to separate network traffic?
Traffic inside a VLAN stays local to that VLAN’s broadcast domain; switches forward Ethernet frames with a VLAN tag only to ports in the same VLAN. Separating network traffic reduces unnecessary broadcasts, lowers the chance of congestion during peak hours, and ensures that sensitive traffic is kept apart from general user traffic to limit exposure and improve performance.
What is the significance of the VLAN to which the frame is assigned when forwarding ethernet frames?
Each Ethernet frame with a VLAN ID is forwarded only to ports in the VLAN to which the frame is assigned. Frames with a VLAN ID preserve logical boundaries within the same physical network, ensuring that devices see only the traffic intended for their segment and that policies can be applied consistently across the network.