Socelars Malware Attacking Windows Systems to Steal Sensitive Business Data
Unmasking Socelars: The Silent Threat to Your Business Data
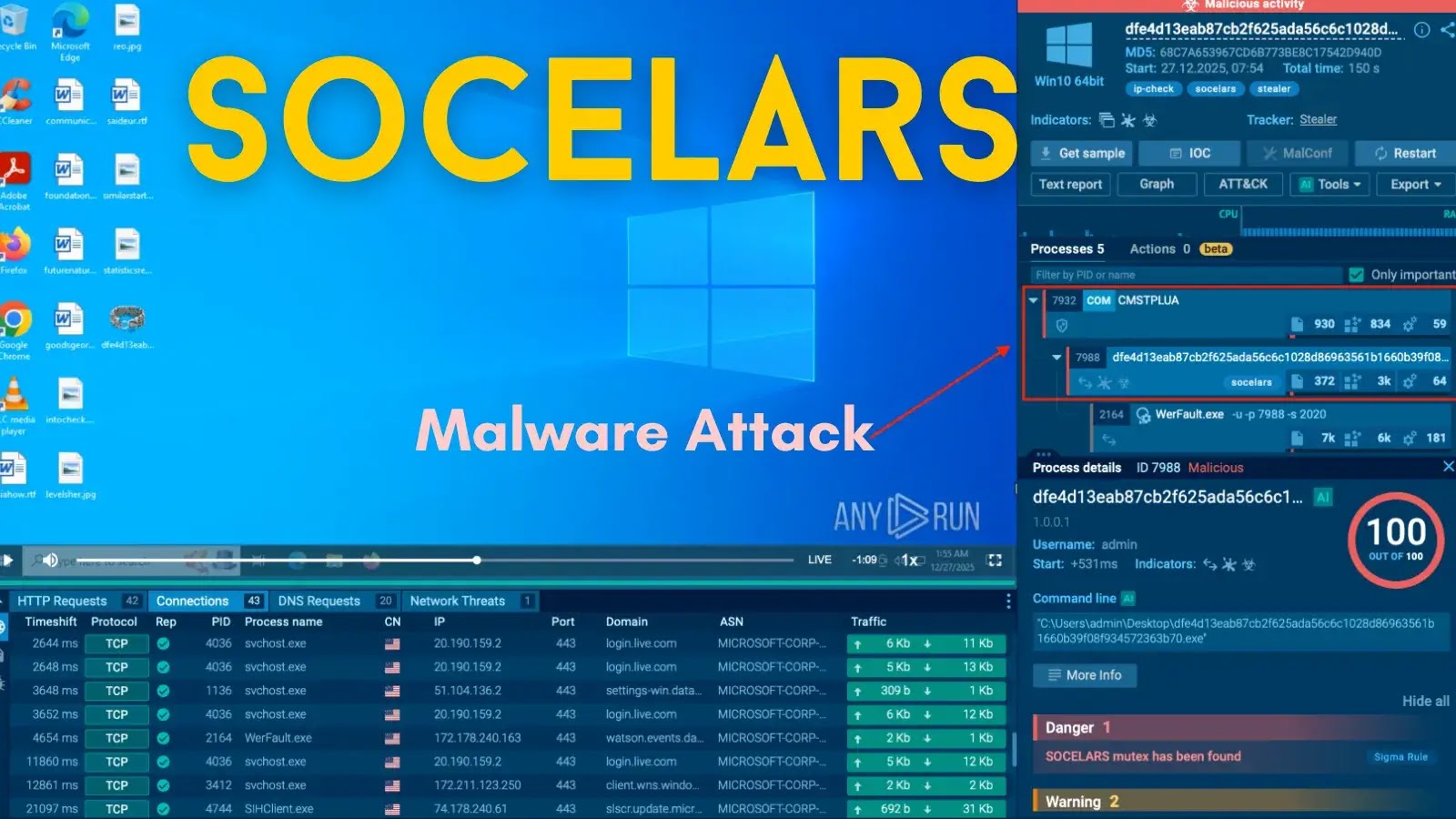
The digital landscape is under constant siege, and a new, insidious threat has emerged: Socelars. This information-stealing malware is actively targeting Windows systems, quietly siphoning off sensitive authentication data. Unlike traditional malware that announces its presence with immediate system disruptions, Socelars operates stealthily, transforming infected machines into conduits for account takeover and financial fraud. For IT professionals, security analysts, and developers, understanding and mitigating this silent infiltrator is paramount to safeguarding critical business assets.
What is Socelars Malware?
Socelars is a sophisticated information stealer primarily focused on collecting sensitive authentication particulars from Windows systems. Its particular emphasis lies in pilfering data related to Facebook Ads Manager accounts and session cookies. While other malware might aim for direct system damage, Socelars is designed for prolonged, undetected data exfiltration, making it a particularly dangerous tool in the arsenal of cybercriminals.
- Silent Operation: Socelars avoids overt system interruptions, making its presence difficult to detect without dedicated security measures.
- Targeted Data: It specifically seeks out credentials and session cookies, enabling deep access to user accounts.
- Account Takeover Focus: The primary objective is to facilitate account takeovers, leading to unauthorized access and financial exploitation.
How Socelars Operates: The Mechanics of Data Theft
The operational methodology of Socelars is designed for efficiency and evasion. It typically gains initial access through phishing campaigns, malicious downloads, or compromised websites. Once resident on a Windows system, it begins its reconnaissance, identifying and extracting valuable authentication tokens and cookies. For instance, by stealing Facebook Ads Manager credentials and session cookies, attackers can gain complete control over advertising campaigns, draining budgets, running fraudulent ads, or even using the compromised accounts for further malicious activities.
This malware’s ability to remain undetected for extended periods makes it a persistent threat. It effectively turns an infected machine into a remote access point for attackers to gather information without triggering immediate security alerts.
Remediation Actions Against Socelars
Proactive and multi-layered security strategies are essential to combat Socelars and similar information-stealing malware. Implementing the following actions can significantly reduce the risk of infection and data compromise:
- 강화된 Endpoint Detection and Response (EDR): Deploy and meticulously monitor EDR solutions capable of detecting anomalous behavior and identifying suspicious process activities, even those operating silently.
- Multi-Factor Authentication (MFA): Mandate MFA for all business accounts, especially those accessing sensitive platforms like Facebook Ads Manager. Even if credentials are stolen, MFA acts as a critical barrier to account takeover.
- Regular Security Awareness Training: Educate employees on identifying and avoiding phishing attempts, malicious links, and suspicious attachments, which are common initial infection vectors.
- Patch Management: Ensure all operating systems, applications, and browsers are kept up-to-date with the latest security patches to close known vulnerabilities.
- Principle of Least Privilege: Implement the principle of least privilege, ensuring users and applications only have the necessary access rights to perform their functions, thereby limiting the potential damage of a compromised account.
- Session Cookie Management: Implement stricter session cookie expiration policies and educate users on the risks of persistent logins on shared or public machines.
- Incident Response Plan: Develop and regularly test a comprehensive incident response plan to quickly detect, contain, and eradicate malware infections and mitigate their impact.
Detection and Mitigation Tools
Utilizing appropriate security tools is crucial for both identifying Socelars and preventing its successful operation.
| Tool Name | Purpose | Link |
|---|---|---|
| Endpoint Detection and Response (EDR) Solutions | Real-time threat detection, investigation, and response on endpoints. | — (Vendor-specific) |
| Security Information and Event Management (SIEM) | Aggregates and analyzes security logs for threat correlation and detection. | — (Vendor-specific) |
| Password Managers with MFA Integration | Securely store passwords and facilitate MFA for enhanced account security. | — (e.g., LastPass, 1Password) |
| Network Intrusion Detection/Prevention Systems (NIDS/NIPS) | Monitor network traffic for malicious activity and block known threats. | — (Vendor-specific) |
Protecting Your Digital Assets from Invisible Threats
The emergence of Socelars serves as a stark reminder that cyber threats are constantly evolving. Malware like Socelars, designed for covert data exfiltration, poses a significant risk to confidential business data and financial stability. By understanding its operational tactics and implementing robust, multi-faceted security measures—from rigorous employee training to advanced EDR solutions and strict access controls—organizations can significantly enhance their defenses against such sophisticated and silent attackers. Vigilance and proactive security hygiene are your strongest allies in the ongoing battle to protect digital assets.





