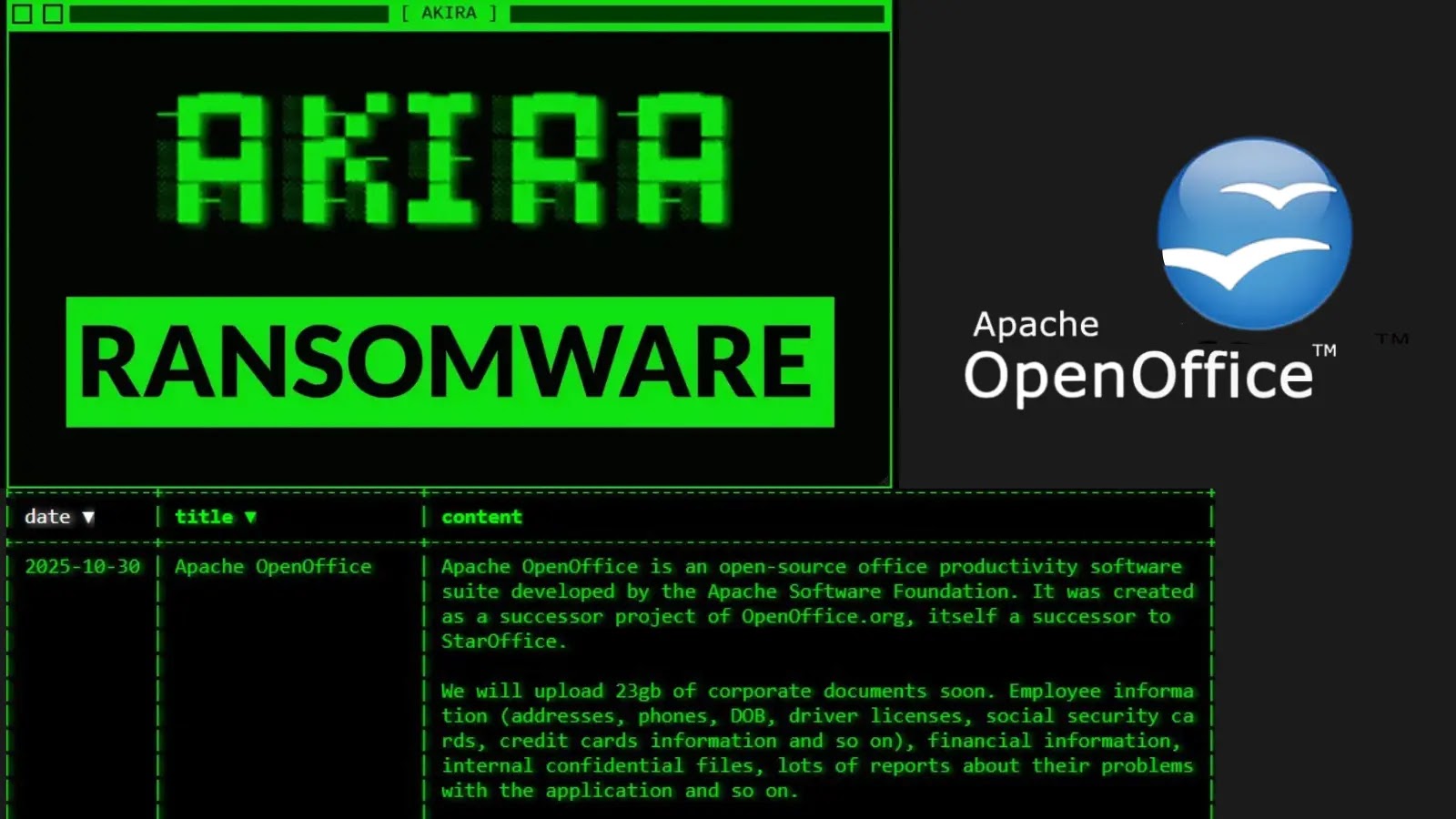
Akira Ransomware Allegedly Claims Theft of 23GB in Apache OpenOffice Breach
The digital strongholds of even the most established open-source projects are not immune to the relentless assault of cyber adversaries. A concerning development has rocked the cybersecurity landscape, with reports emerging of the prolific Akira ransomware group claiming a significant data breach against Apache OpenOffice. This incident not only underscores the pervasive threat of ransomware but also highlights the critical importance of robust security measures for all organizations, regardless of their non-profit or open-source status.
Akira Ransomware Claims 23GB Data Theft from Apache OpenOffice
On October 29, 2025, the notorious Akira ransomware group sent ripples through the cybersecurity community by announcing a successful compromise of Apache OpenOffice’s systems. The group, infamous for its double-extortion methodologies, publicly declared on its dark web leak site the exfiltration of a staggering 23 gigabytes of sensitive corporate data. This declaration was accompanied by the characteristic ransomware threat: a demand for payment to prevent the public release of the stolen information.
The alleged breach against Apache OpenOffice, a widely used open-source productivity suite, serves as a stark reminder that even projects with community-driven development and strong security-aware contributors can fall victim to sophisticated attacks. The sheer volume of data claimed – 23GB – suggests a deep penetration of the organization’s infrastructure.
Understanding Akira Ransomware’s Tactics
Akira is not a new player in the ransomware arena. This group has garnered a reputation for its aggressive and systematic approach to extortion. Their modus operandi often involves:
- Initial Access: Gaining unauthorized entry through various means, including exploiting vulnerabilities in remote access services, phishing campaigns, or compromised credentials.
- Lateral Movement: Navigating through the compromised network to identify and access valuable systems and data.
- Data Exfiltration: Stealing sensitive information before encryption, enabling their potent double-extortion tactic. This is precisely what is alleged in the Apache OpenOffice incident.
- Data Encryption: Encrypting critical files and systems, rendering them inaccessible to the victim.
- Ransom Demand and Leak Site: Issuing a ransom demand, often backed by threats of public data release on a dedicated dark web leak site if payment is not made.
The alleged breach of Apache OpenOffice aligns perfectly with Akira’s established tactics, particularly the heavy reliance on data exfiltration as leverage.
Potential Impact of the Apache OpenOffice Breach
While the full scope of the alleged data theft is yet to be disclosed by Akira, the implications for Apache OpenOffice and its users could be significant. “Sensitive corporate data” could encompass a wide range of information, including, but not limited to:
- Developer communications and private mailing lists.
- Internal project management documents.
- User data from support forums or donation platforms.
- Proprietary code or intellectual property related to Apache’s internal operations.
- Financial records or employee data.
The exposure of such data could lead to severe reputational damage, legal ramifications, and a potential erosion of trust among Apache OpenOffice’s extensive user base and contributors.
Remediation Actions and Prevention Strategies
While the specifics of the breach are still under investigation, organizations can take proactive steps to harden their defenses against similar ransomware attacks. For Apache OpenOffice and other open-source projects, a thorough incident response is paramount:
- Isolate and Contain: Immediately isolate affected systems to prevent further spread of the ransomware.
- Forensic Analysis: Conduct a comprehensive forensic investigation to identify the initial point of compromise, the extent of data exfiltration, and any backdoors left by the attackers.
- Patch Management: Ensure all systems, especially those exposed to the internet, are fully patched and updated. Pay particular attention to vulnerabilities like those reported in common web servers and applications.
- Strong Authentication: Implement multi-factor authentication (MFA) across all services, particularly for administrative access and remote connections.
- Regular Backups: Maintain immutable, offline backups of all critical data. This is crucial for recovery without resorting to ransom payments.
- Network Segmentation: Implement network segmentation to limit lateral movement within the network, restricting an attacker’s ability to access sensitive systems even if an initial breach occurs.
- Employee Training: Conduct regular cybersecurity awareness training for all personnel, focusing on phishing detection, secure browsing habits, and reporting suspicious activities.
- Monitor for CVEs: Actively monitor and patch vulnerabilities. While not directly linked to a specific CVE in this incident, many ransomware attacks leverage existing flaws. For instance, common vulnerabilities in applications like Apache, such as CVE-2021-44228 (Log4Shell), demonstrate the critical need for prompt patching of any disclosed vulnerability.
Security Tools for Detection and Mitigation
Implementing a robust security posture requires a combination of processes, people, and technology. Here are some essential tools that can aid in detecting and mitigating ransomware threats:
| Tool Name | Purpose | Link |
|---|---|---|
| Endpoint Detection and Response (EDR) solutions | Detect and respond to malicious activities on endpoints, including ransomware behavior. | (Vendor Specific – e.g., CrowdStrike, SentinelOne) |
| Intrusion Detection/Prevention Systems (IDS/IPS) | Monitor network traffic for suspicious patterns and block known malicious activities. | (Vendor Specific – e.g., Snort, Suricata) |
| Vulnerability Scanners | Identify security weaknesses and misconfigurations in systems and applications. | (e.g., Nessus, OpenVAS) |
| Security Information and Event Management (SIEM) systems | Collect and analyze security logs from various sources to detect threats and aid in incident response. | (Vendor Specific – e.g., Splunk, QRadar) |
| Email Security Gateways | Filter out phishing emails and malicious attachments before they reach users. | (Vendor Specific – e.g., Proofpoint, Mimecast) |
Key Takeaways from the Apache OpenOffice Incident
The alleged Akira ransomware attack on Apache OpenOffice serves as a stark reminder that no entity is truly immune to cyber threats. The incident underscores the critical necessity of a proactive and multi-layered approach to cybersecurity. Organizations must prioritize robust patch management, strong authentication, regular backups, and comprehensive employee training. Furthermore, incident response planning and the capability to conduct thorough forensic analysis are non-negotiable in today’s threat landscape. The incident should prompt all organizations, particularly those managing open-source projects, to re-evaluate and strengthen their cybersecurity defenses against sophisticated adversaries like Akira.





