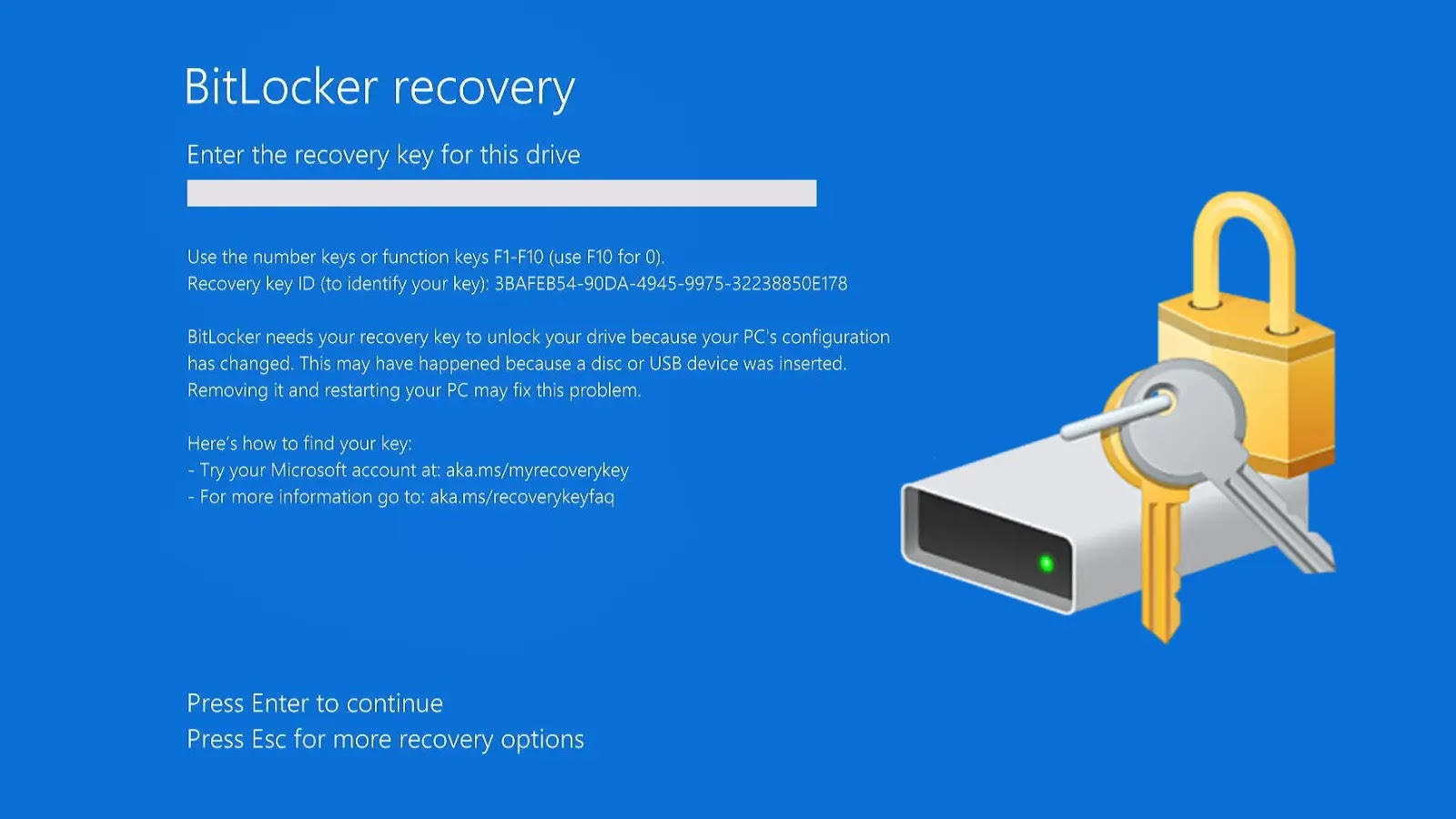
Automatic BitLocker Encryption May Silently Lock Away Your Data
The Silent Encryption Threat: When BitLocker Locks Away Your Data Unprompted
Imagine this: you’ve just finished a routine Windows operating system reinstallation, a common practice for troubleshooting or upgrading. You then attempt to access your meticulously organized backup drives, only to find them inaccessible, encrypted by technology you never explicitly configured. This isn’t a hypothetical IT nightmare; it’s a stark reality experienced by a Reddit user who discovered 3TB of irreplaceable data silently locked away by automatic BitLocker encryption.
This incident, detailed on Reddit and highlighted by Cyber Security News, underscores a critical, often overlooked risk associated with Microsoft’s automatic encryption features in Windows 11. For IT professionals, system administrators, and even power users, understanding this silent threat is paramount to safeguarding valuable data.
Understanding Automatic BitLocker Encryption
BitLocker is a full-disk encryption feature built into Microsoft Windows versions starting with Vista. Its primary purpose is to protect data by encrypting entire volumes. While it’s a powerful security tool, its automatic activation can lead to significant data loss if not properly managed.
In Windows 11, particularly on systems meeting specific hardware requirements (such as having a Trusted Platform Module or TPM 2.0 and UEFI firmware), BitLocker encryption can be enabled automatically without explicit user intervention during the initial setup or even during significant system events like an operating system reinstallation. This feature, often designed to enhance default security, can become a silent data trap when recovery keys are not securely stored or when users are unaware of its activation.
The Reddit Incident: A Case Study in Silent Data Lockout
The Reddit poster’s experience serves as a cautionary tale. After performing a clean reinstall of Windows 11, they found two of their backup drives, containing invaluable data, mysteriously locked with BitLocker. The user had not set up BitLocker manually on these drives, nor were they prompted to save a recovery key during the OS reinstallation process. This scenario is particularly insidious because the user was completely unaware of the encryption until it was too late to easily access their data.
This situation points to a potential gap in user awareness and Microsoft’s implementation of automatic encryption. While security by default is generally a positive step, silent enablement without clear prompts for key management can lead to catastrophic data loss for unsuspecting users.
How BitLocker Can Activate Without Your Direct Input
- Initial Device Setup: On new devices or during a fresh Windows 11 installation on eligible hardware, BitLocker (or Device Encryption, a consumer-friendly version) can activate automatically, often linking the recovery key to the user’s Microsoft account.
- System Upgrades and Reinstallations: As seen in the Reddit incident, performing a major OS intervention or even some updates can trigger BitLocker encryption on eligible drives, especially if they were previously unencrypted but the system meets the hardware prerequisites.
- TPM Presence: Systems equipped with a functional Trusted Platform Module (TPM) are more prone to automatic BitLocker activation as the TPM securely stores the encryption keys related to the system drive.
Remediation Actions and Best Practices
Preventing silent BitLocker lockout requires proactive measures and a clear understanding of your system’s configuration. There is no specific CVE associated with this operational behavior, as it’s a feature, not a vulnerability in the traditional sense, but its unintended consequences can be severe. However, adopting robust data management practices is crucial.
- Always Back Up Your Data: This is the golden rule of data security. Before any major OS reinstall, upgrade, or even significant system changes, ensure all critical data is backed up to multiple, independent locations.
- Verify BitLocker Status: Regularly check the encryption status of all your drives. You can do this by:
- Opening “This PC” or “My Computer,” right-clicking on a drive, and going to “Properties.”
- Using the “Manage BitLocker” control panel option.
- Running
manage-bde -statusin an elevated Command Prompt or PowerShell.
- Securely Store Recovery Keys: If BitLocker is enabled (whether manually or automatically), locate and securely back up your BitLocker recovery key. This key can be saved to your Microsoft account, a USB flash drive, a file, or printed.
- Microsoft Account: Check https://account.microsoft.com/devices/recoverykey for keys linked to your account.
- Disabling Automatic Device Encryption: For advanced users or managed environments, consider disabling automatic device encryption if not explicitly required by policy. This often involves GPO settings in enterprise environments or specific registry modifications for individual machines.
- Clear Communication and User Training: In organizational settings, educate users about BitLocker and the importance of recovery key management. Implement policies that ensure recovery keys are backed up to a central, secure key escrow system.
Tools for BitLocker Management
Effective management of BitLocker is crucial. Here are some tools and commands that aid in this process:
| Tool Name | Purpose | Link (if applicable) |
|---|---|---|
| Manage-bde | Command-line tool for managing BitLocker Drive Encryption. Used for status checks, key management, and encryption/decryption. | Microsoft Docs |
| BitLocker Drive Encryption Control Panel | Graphical user interface for managing BitLocker on individual drives. | Built-in to Windows (Search “Manage BitLocker”) |
| BitLocker Recovery Key Viewer | (For domain environments) Tool to view BitLocker recovery keys stored in Active Directory. | N/A (Active Directory Users and Computers snap-in) |
Conclusion: Prioritizing Proactive Data Protection
The incident of silent BitLocker encryption underscores a critical lesson: never assume your data is fully protected without explicit verification and management. While features like BitLocker are designed to enhance security, their automatic implementation can inadvertently lead to data loss if recovery mechanisms are not firmly established beforehand. Regular data backups, diligent monitoring of encryption status, and secure storage of recovery keys are not just best practices; they are essential safeguards in an increasingly automated digital landscape. Stay informed, stay secure, and always prioritize proactive data protection.





