BodySnatcher – New Vulnerability Allows Attacker to Impersonate Any ServiceNow User
Imagine a scenario where an unauthenticated attacker, without needing any login credentials, could seamlessly step into the shoes of any employee within your organization’s ServiceNow instance. This isn’t a hypothetical threat; it’s the stark reality unveiled by “BodySnatcher,” a critical new vulnerability impacting ServiceNow’s Virtual Agent API and the cutting-edge Now Assist AI Agents application. This significant discovery poses a severe risk to organizations relying on ServiceNow for IT service management, customer service, and more.
Understanding the BodySnatcher Vulnerability
Security researcher Aaron Costello from AppOmni meticulously uncovered BodySnatcher, a flaw tracked as CVE-2025-12420. This vulnerability isn’t a singular misconfiguration but rather a dangerous cocktail of two distinct weaknesses: a hardcoded platform-wide secret combined with insecure account-linking logic. Together, these elements empower an attacker to bypass authentication mechanisms and remotely execute privileged AI agents, effectively impersonating any user on the platform.
The core issue lies in how ServiceNow’s Virtual Agent API and Now Assist AI Agents handle user authentication and session management. The hardcoded secret acts as a master key of sorts, which, when coupled with the faulty account-linking processes, allows an unauthorized entity to trick the system into believing they are a legitimate, authenticated user. This capability grants the attacker the ability to interact with the system and execute actions with the privileges of their chosen victim.
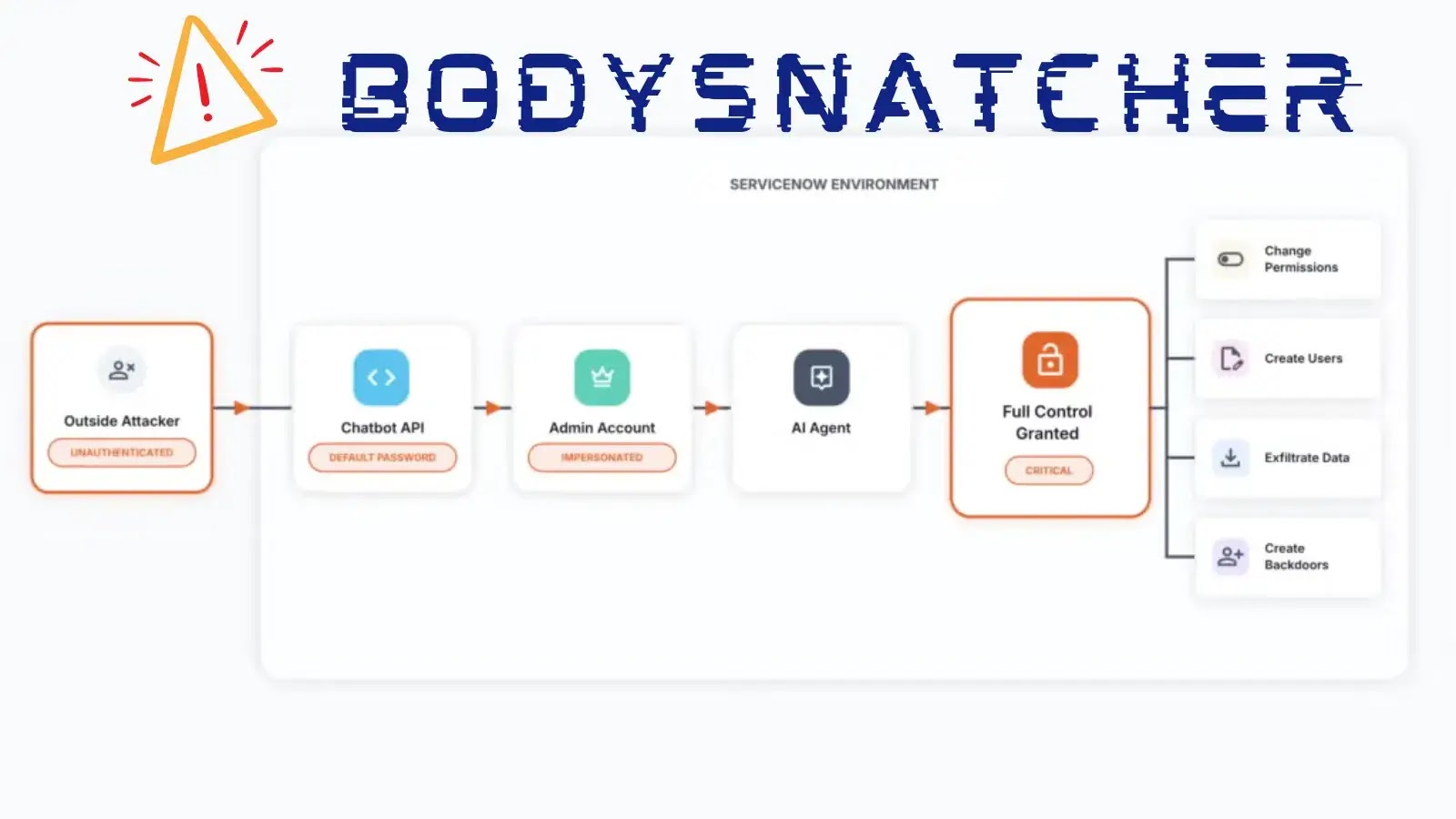
The Mechanics of Impersonation
The “BodySnatcher” attack sequence, while technical, can be summarized as follows:
- An unauthenticated attacker leverages the hardcoded platform-wide secret inherent in the system.
- This secret, combined with flaws in the account-linking logic, enables the attacker to initiate a session as if they were any targeted ServiceNow user.
- Once impersonated, the attacker can then invoke and execute privileged AI agents remotely through the Virtual Agent API.
- This execution can lead to a wide array of malicious activities, from accessing sensitive data to making changes within the ServiceNow environment, all under the guise of an authentic user.
The implications are far-reaching. Imagine an attacker impersonating a high-privilege IT administrator to access critical infrastructure controls, a human resources manager to view sensitive employee data, or a finance executive to approve fraudulent transactions. The potential for data breaches, system compromise, and operational disruption is immense.
Remediation Actions and Mitigating Risk
Addressing the BodySnatcher vulnerability requires immediate attention and systematic remediation. Organizations leveraging ServiceNow, particularly those utilizing the Virtual Agent API and Now Assist AI Agents, must act decisively.
- Apply Patches Immediately: Monitor official ServiceNow advisories and apply all patches related to CVE-2025-12420 as soon as they become available. This is the most crucial step.
- Review API Security: Conduct a comprehensive review of your Virtual Agent API configurations and access controls. Ensure that API endpoints are secured with robust authentication and authorization mechanisms beyond what might be affected by this vulnerability.
- Enhance Monitoring: Increase vigilance for unusual activity within your ServiceNow instance, particularly focusing on interactions with the Virtual Agent and AI Agents. Look for anomalous logins, unusual data access patterns, or unexpected command executions.
- Implement Least Privilege: Reinforce the principle of least privilege for all users and AI agents. Ensure that individuals and automated processes only have the minimum necessary permissions to perform their tasks.
- Segregate Environments: Where possible, segregate critical data and functions within your ServiceNow instance to limit the blast radius of any successful impersonation attack.
- Regular Security Audits: Conduct regular third-party security audits and penetration testing specifically targeting your ServiceNow implementation and integrated APIs.
Tools for Detection and Mitigation
While direct patches are paramount, various cybersecurity tools can aid in detecting suspicious activity and strengthening your overall security posture against such sophisticated threats.
| Tool Name | Purpose | Link |
|---|---|---|
| ServiceNow Security Incident Response (SIR) | Detects, analyzes, and responds to security incidents within the ServiceNow platform. | ServiceNow SIR |
| API Security Gateways (e.g., Akana, Apigee) | Provides advanced authentication, authorization, and threat protection for APIs. | Akana / Apigee |
| Security Information and Event Management (SIEM) | Aggregates and analyzes log data from various sources, including ServiceNow, to detect anomalies. | Splunk / IBM QRadar |
| Identity Governance and Administration (IGA) Solutions | Manages digital identities and access rights across an organization’s IT landscape. | SailPoint / OneLogin |
Protecting Your ServiceNow Ecosystem
The BodySnatcher vulnerability, CVE-2025-12420, serves as a powerful reminder that even sophisticated enterprise platforms are not immune to critical flaws. The combination of a hardcoded secret and insecure account-linking within ServiceNow’s Virtual Agent API and Now Assist AI Agents creates a direct pathway for unauthenticated attackers to impersonate any user. Organizations must prioritize applying official patches, strengthening API security, enhancing monitoring capabilities, and adhering to strict access control principles to safeguard their ServiceNow environments against this critical impersonation threat. Vigilance and proactive security measures are your best defense.





