Chrome Zero-Day Vulnerabilities Exploited in 2025 – A Comprehensive Analysis
Unmasking the Pervasive Threat: Chrome Zero-Day Exploits of 2025
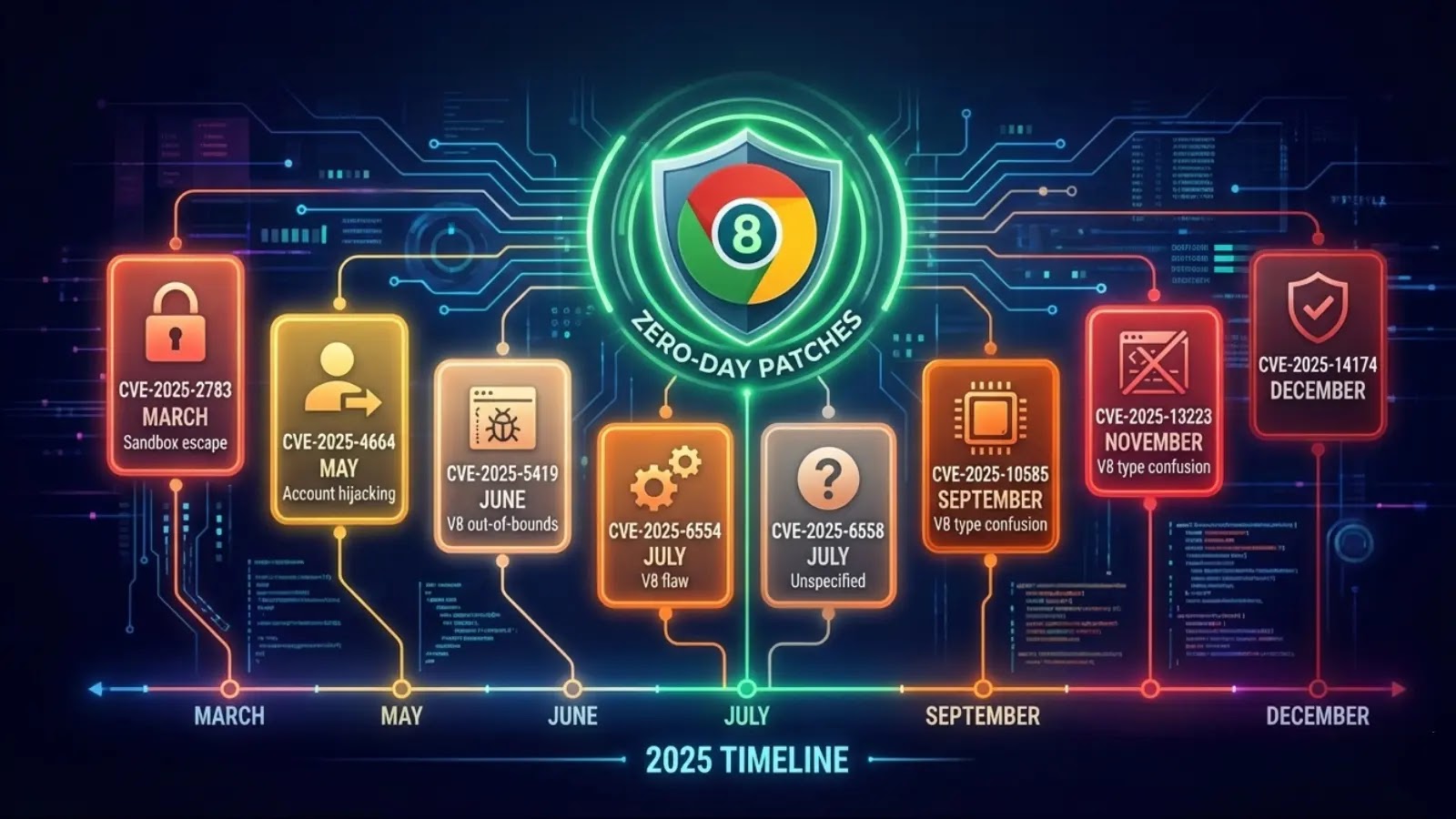
In 2025, Google’s ubiquitous Chrome browser became a prime target for sophisticated threat actors, leading to an alarming wave of actively exploited zero-day vulnerabilities. These critical flaws, eight in total, underscored a persistent and evolving threat landscape, impacting billions of users globally. As cybersecurity analysts, understanding the nature and impact of these exploits is paramount to hardening our defenses and protecting digital assets.
Eight Critical Flaws: A Deep Dive into Chrome’s 2025 Vulnerabilities
Throughout 2025, Google patched a significant number of high-severity zero-day vulnerabilities within its Chrome browser. These weren’t theoretical risks; they were actively exploited in the wild, indicating a coordinated effort by well-resourced adversaries. Each of these flaws carried an average CVSS score of 8.5, firmly placing them in the “high severity” category. While specific details for each individual 2025 zero-day are often kept under wraps by Google to prevent further exploitation, patterns often emerge around areas like use-after-free vulnerabilities, type confusion, and integer overflows within Chrome’s various components, such as the V8 JavaScript engine, WebAssembly, or UI components.
The consistent targeting of Chrome highlights its critical position as the world’s most popular web browser. Its widespread adoption makes it an attractive entry point for data exfiltration, system compromise, and the deployment of additional malware. The ability of attackers to leverage these zero-days meant they could bypass existing security mechanisms, execute arbitrary code, and gain unauthorized access to user systems before a patch was even available.
The Anatomy of a Zero-Day Exploit
A zero-day vulnerability is a software flaw unknown to the vendor, meaning there’s “zero days” for them to fix it before an attacker exploits it. In the context of Chrome, these exploits often leverage weaknesses in:
- V8 JavaScript Engine: Exploits commonly target memory safety issues like use-after-free or type confusion, leading to remote code execution (RCE).
- Browser UI Components: Flaws in Chrome’s user interface rendering or handling of specific web elements could allow for sandbox escapes.
- WebAssembly: Emerging vulnerabilities in WebAssembly execution could open new attack vectors.
- Internals/Extensions: Issues within specific Chrome internals or the way extensions interact with the browser can also be exploited.
Once exploited, a zero-day can lead to a range of severe consequences, including full system compromise, data theft, and the installation of surveillance tools. The silent nature of these attacks, often occurring without user interaction, makes them particularly insidious.
Remediation Actions for Chrome Zero-Day Threats
While zero-days, by definition, exploit unknown vulnerabilities, proactive security practices significantly reduce the attack surface and mitigate their impact. For an IT professional, security analyst, or developer, the following actions are crucial:
- Prompt Patching: The most critical defense. Ensure all Chrome installations are updated immediately upon new security releases. Google’s rapid patching cycles for zero-days are designed to close these windows of opportunity quickly.
- Principle of Least Privilege: Operate with the minimum necessary permissions. This can limit the damage an attacker can inflict even if an exploit is successful.
- Endpoint Detection and Response (EDR): Utilize EDR solutions to monitor for anomalous behavior, unusual process execution, and network connections that could indicate a compromise, even if an initial exploit bypasses traditional antivirus.
- Network Segmentation: Isolate critical systems and sensitive data on separate network segments. This can contain the lateral movement of an attacker post-exploitation.
- Security Awareness Training: Educate users about phishing, suspicious links, and social engineering tactics, which are often used in conjunction with zero-day exploits to deliver malicious payloads.
- Content Security Policy (CSP): Implement robust CSP headers on web applications to reduce the impact of cross-site scripting (XSS) and other client-side attacks that might leverage browser vulnerabilities.
- Regular Security Audits: Conduct frequent security assessments and penetration testing to identify and address potential weaknesses in your infrastructure.
Tools for Detection and Mitigation
While no tool can guarantee protection against every zero-day, a layered security approach using these tools can significantly enhance your defensive posture:
| Tool Name | Purpose | Link |
|---|---|---|
| Google Chrome Enterprise | Centralized management and rapid updates for enterprise environments. | https://chromeenterprise.google/ |
| Windows Defender Advanced Threat Protection (ATP) / Microsoft Defender for Endpoint | Endpoint detection and response (EDR), behavioral analysis, and threat intelligence. | https://www.microsoft.com/en-us/security/business/endpoint-security/microsoft-defender-endpoint |
| CrowdStrike Falcon Insight | Cloud-native EDR and next-gen antivirus for real-time threat detection and response. | https://www.crowdstrike.com/endpoint-security-products/falcon-insight-edr/ |
| Tenable.io (Vulnerability Management) | Continuous vulnerability scanning and assessment across IT infrastructure. | https://www.tenable.com/products/tenable-io |
| OWASP ZAP | Open-source web application security scanner for identifying vulnerabilities in web applications. | https://www.zaproxy.org/ |
Looking Ahead: The Evolving Threat Landscape
The 2025 Chrome zero-day exploits serve as a stark reminder that browser security remains a critical battleground. As browsers become more complex and integrate deeper into operating systems, the potential for sophisticated attacks will only increase. Organizations and individuals must prioritize continuous vigilance, rapid patching, and a multi-layered security strategy to stay ahead of these persistent threats. The proactive investment in robust security practices is not merely a recommendation; it is a necessity in an increasingly hostile digital environment.





