ClickFix Attack Uses Steganography to Hide Malicious Code in Fake Windows Security Update Screen
The Devious Disguise: ClickFix Attack Hides Malware in Fake Windows Updates via Steganography
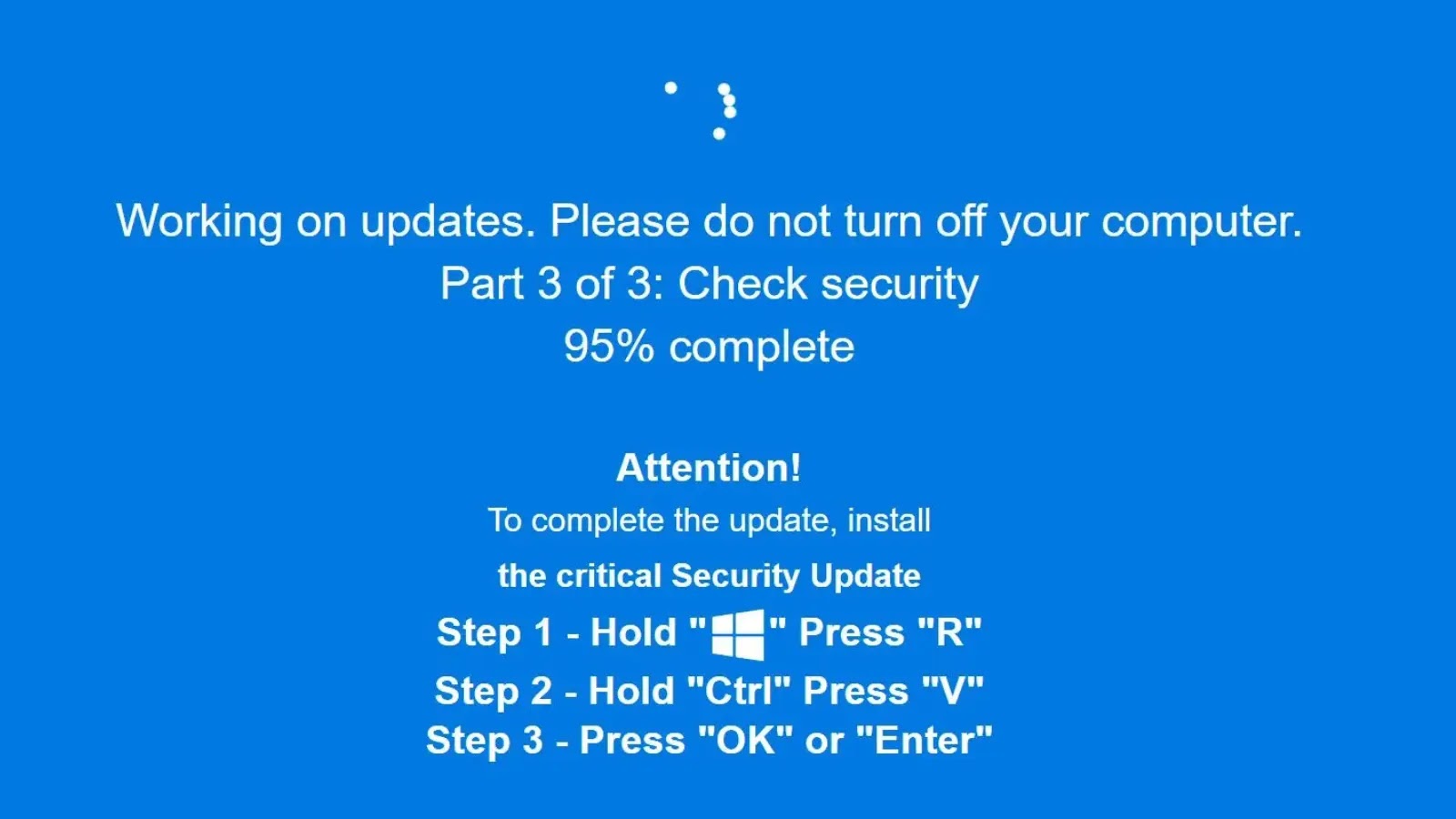
A new, highly concerning cyber threat has emerged, leveraging sophisticated social engineering and technical evasion to deploy infostealing malware. Threat actors behind what’s being dubbed the “ClickFix” campaign are actively exploiting user trust by presenting a remarkably convincing fake Windows security update screen. What makes this attack particularly insidious is its use of steganography – a method of concealing data within ordinary files – to hide malicious code within seemingly innocuous PNG images. This multi-stage, file-light infection chain poses a significant risk to individuals and organizations alike, turning a simple, user-initiated action into a full-blown malware compromise.
Understanding the ClickFix Attack Mechanism
The ClickFix campaign is a prime example of how adversaries innovate to bypass traditional security measures. The initial vector relies heavily on social engineering. Victims are tricked into believing their system requires an urgent Windows security update. This fake update screen is crafted to be highly realistic, reducing user suspicion. The critical step, observed by security researchers, is convincing the user to manually execute a pre-staged command. This seemingly innocuous user action is the gateway for the attack to proceed.
Once the initial command is executed, the attack chain leverages steganography. Malicious code is embedded within a PNG image file. This technique makes detection difficult because the image itself appears legitimate, and typical antivirus solutions might not flag it as suspicious. When the hidden code is extracted and executed, it proceeds to deploy advanced infostealers like LummaC2 and Rhadamanthys. These types of malware are designed to exfiltrate sensitive data, including credentials, financial information, and other personal or corporate data, directly from infected systems.
The Role of Steganography in Evasion
Steganography is not a new concept in cybersecurity, but its application in the ClickFix campaign highlights an evolving trend in attacker tactics. Rather than embedding malicious executable files directly, which are often easily detected by signature-based antivirus, steganography allows attackers to hide payloads within seemingly benign files like images. This makes network traffic analysis and endpoint detection more challenging. The malicious code remains dormant and hidden until a specific trigger or command extracts and executes it, effectively turning a common image into a digital Trojan horse.
Infostealers: LummaC2 and Rhadamanthys
The choice of LummaC2 and Rhadamanthys as the final payloads underscores the financial and data-theft motives behind these attacks. These are potent infostealers with capabilities to:
- Collect browser data (passwords, cookies, autofill data).
- Harvest cryptocurrency wallet details.
- Steal sensitive files from the compromised system.
- Capture screenshots.
- Exfiltrate data to attacker-controlled command-and-control (C2) servers.
The impact of such breaches can range from personal identity theft and financial fraud to corporate espionage and significant data loss, making early detection and prevention paramount.
Remediation Actions and Prevention
Mitigating the risk from sophisticated attacks like ClickFix requires a multi-layered approach focusing on user education, technical controls, and proactive threat hunting.
- User Education: Train employees and educate users about the dangers of unsolicited software updates and the importance of verifying the authenticity of any system prompts. Emphasize never running commands or installing software from unverified sources.
- Verify Updates: Always obtain Windows updates directly through official channels (Windows Update settings) and never through pop-up windows or emailed links.
- Email and Attachment Scrutiny: Exercise extreme caution with emails containing attachments or links, especially if they claim to be about system updates or urgent security notices.
- Endpoint Detection and Response (EDR): Implement robust EDR solutions that can detect fileless attacks, unusual process activity, and anomalous network connections, even if initial payloads bypass traditional antivirus.
- Network Traffic Analysis: Monitor network traffic for suspicious C2 communications or unusual outbound connections, which could indicate data exfiltration.
- Principle of Least Privilege: Limit user permissions to prevent the execution of unauthorized commands or software installations.
- Regular Backups: Maintain regular, offsite backups of critical data to ensure recovery in case of a successful attack.
Conclusion
The ClickFix campaign serves as a stark reminder that cyber threats are constantly evolving, employing social engineering alongside sophisticated technical evasion techniques like steganography. By leveraging fake Windows security update screens and embedding malicious code within seemingly harmless images, attackers aim to bypass conventional defenses. Staying vigilant, educating users, and implementing a robust, multi-faceted security strategy are crucial steps in defending against these insidious and increasingly prevalent threats.





