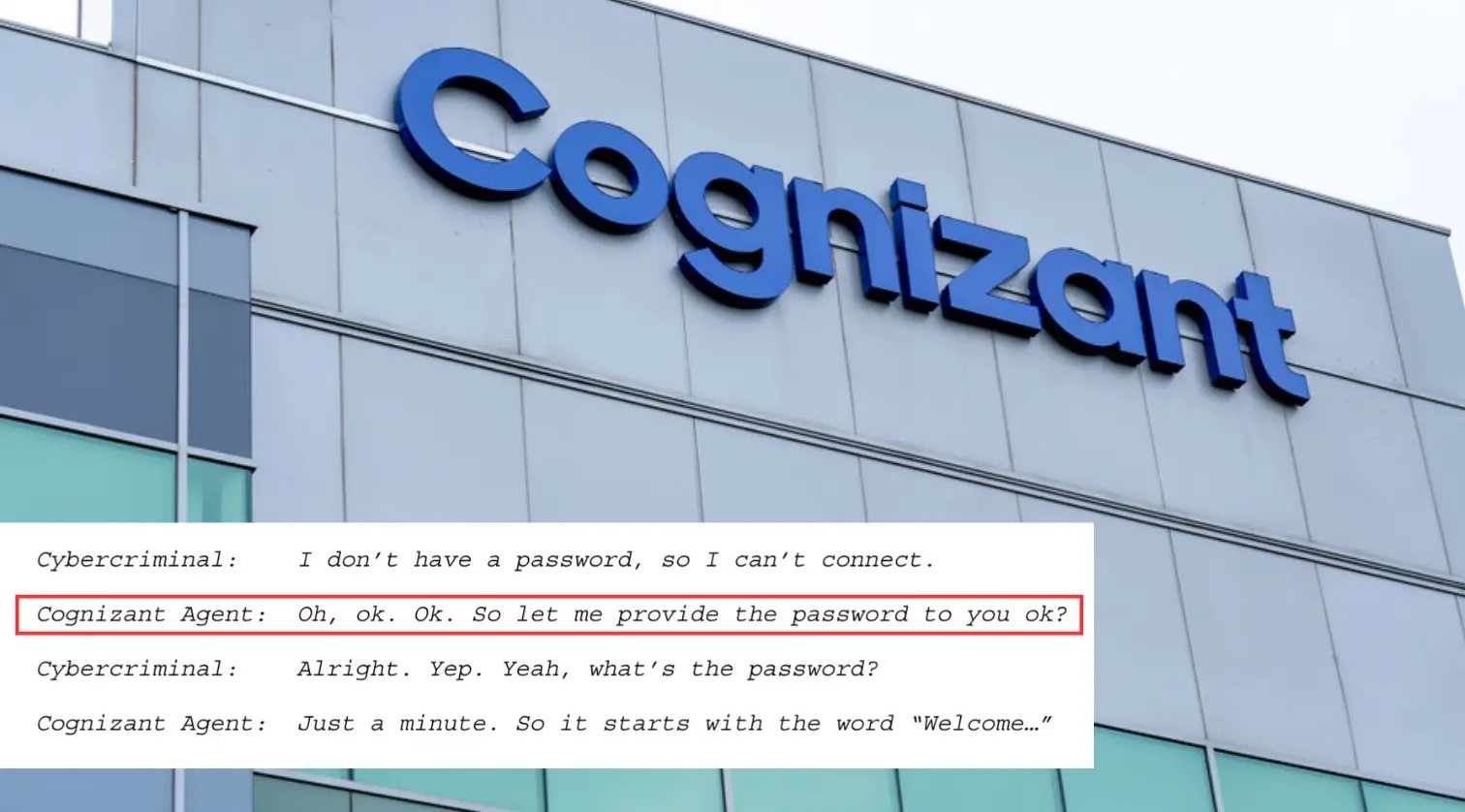
Clorox Sues IT Provider Cognizant For Simply Giving Employee Password to Hackers
The quiet hum of business operations can turn into a cacophony of disruption when cybersecurity fails. This stark reality has hit The Clorox Company, a global leader in household products, which has initiated a significant lawsuit against its IT services provider, Cognizant Technology Solutions. The core of the dispute? Allegations that human error at Cognizant’s help-desk led directly to a devastating cyberattack, costing Clorox an estimated $380 million and causing widespread product shortages. This incident serves as a critical reminder that even seemingly minor vulnerabilities, especially those exploited through social engineering, can have catastrophic financial and operational consequences.
The Breach: A Case of Human Vulnerability
In August 2023, Clorox experienced a severe network intrusion that crippled its operations for months. The subsequent lawsuit filed by Clorox against Cognizant points to a critical lapse: the alleged inadvertent disclosure of an employee’s password by Cognizant help-desk agents to malicious actors. This act, whether stemming from insufficient verification protocols, a sophisticated phishing attack on the agents themselves, or a combination of factors, gifted hackers the keys to Clorox’s digital kingdom. While the specific method of social engineering employed against the help-desk agents isn’t detailed in the immediate source, it highlights the persistent threat of human factors in cybersecurity. This incident underscores that strong technical controls are only as effective as the weakest human link in the security chain.
Impact and Financial Fallout
The fallout from this breach was immediate and extensive. Clorox reported severe operational disruptions, indicating compromised systems vital for manufacturing, logistics, and supply chain management. The direct consequence was prolonged product shortages, impacting consumers and significantly damaging Clorox’s market position and revenue. The staggering $380 million lawsuit reflects not only direct financial losses but also the immense costs associated with recovery, reputational damage, and lost market opportunities. This case serves as a powerful testament to the far-reaching economic implications of a successful cyberattack, particularly when it targets critical infrastructure within a major enterprise. It also emphasizes the importance of robust incident response plans and business continuity strategies.
Third-Party Risk Management: A Critical Examination
This incident vividly illustrates the inherent risks associated with outsourcing IT services. While leveraging external expertise can be cost-effective and efficient, it inherently introduces third-party risk. Organizations must extend their security perimeters to encompass their vendors and service providers. The Clorox-Cognizant lawsuit underscores the need for:
- Rigorous Vendor Vetting: Comprehensive security assessments of potential IT partners before engagement.
- Explicit Contractual Obligations: Service Level Agreements (SLAs) that clearly define cybersecurity responsibilities, reporting requirements, and incident response protocols for vendors.
- Continuous Monitoring: Regular audits and reviews of vendor security practices, not just at the outset of the contract.
- Strong Access Management: Implementing least privilege principles for vendor access and strict authentication mechanisms.
The concept of shared responsibility in cybersecurity is paramount. Even when services are outsourced, the ultimate accountability for data and operational security often remains with the primary organization.
Remediation Actions and Preventative Measures
Preventing similar incidents requires a multi-layered approach focusing on technology, process, and people. While the direct vulnerability exploited here was human, the remediation must address the systemic weaknesses that allowed it to occur.
- Enhanced Help-Desk Authentication Procedures: Implement stringent multi-factor authentication (MFA) for all help-desk password resets and sensitive account modifications. This includes knowledge-based authentication, pre-registered security questions, or biometric verification, beyond simple name or ID verification.
- Security Awareness Training: Provide rigorous and ongoing training for help-desk personnel on social engineering tactics, phishing identification, and the critical importance of verifying identities before granting access or divulging sensitive information.
- Principle of Least Privilege: Ensure that help-desk agents only have the minimum necessary access rights to perform their job functions. This limits the damage an attacker can inflict even if they compromise a help-desk account.
- Robust Identity and Access Management (IAM): Implement a comprehensive IAM solution with strong password policies, regular password rotations, and granular access controls.
- Incident Response Plan Review: Regularly review and drill incident response plans, focusing on scenarios involving third-party compromises and insider threats. This includes clear communication protocols between the organization and its vendors.
- Regular Security Audits: Conduct frequent internal and external penetration tests and vulnerability assessments, specifically targeting social engineering vectors and help-desk processes.
Tools for Enhanced Security
While no tool can entirely prevent human error, a combination of technologies can significantly reduce the attack surface and mitigate the impact of such incidents.
| Tool Name | Purpose | Link |
|---|---|---|
| Ping Identity/Okta/Duo Security (MFA Solutions) | Provides robust multi-factor authentication (MFA) to prevent unauthorized access, even if a password is stolen. Critical for help-desk interactions. | Ping Identity Okta Duo Security |
| KnowBe4/Proofpoint Security Awareness Training | Offers simulated phishing attacks and comprehensive training modules to educate employees, including help-desk staff, on social engineering and cybersecurity best practices. | KnowBe4 Proofpoint |
| SailPoint/Microsoft Entra ID (formerly Azure AD) | Comprehensive Identity and Access Management (IAM) platforms for managing user identities, access rights, and enforcing least privilege. | SailPoint Microsoft Entra ID |
| Vanta/Drata | Automates security and compliance monitoring for third-party vendors and internal systems, helping manage supply chain risk. | Vanta Drata |
Lessons Learned: A Call for Cyber Resilience
The Clorox-Cognizant lawsuit serves as a stark reminder that cyber threats are multifaceted and constantly evolving. This particular incident, while not tied to a specific CVE (as it’s a human/process vulnerability rather than a software flaw like CVE-2023-38831 or CVE-2023-34039), highlights the persistent danger of social engineering. Organizations must recognize their human element as both their first line of defense and potentially their greatest vulnerability. Moving forward, a robust cybersecurity strategy must integrate advanced technological safeguards with continuous employee education, stringent operational procedures, and proactive third-party risk management. Only through such a holistic approach can businesses truly build resilience against the diverse and evolving landscape of cyber threats.





