Copilot Vulnerability Breaks Audit Logs and Access Files Secretly for Hackers
Unmasking the Silent Threat: How a Copilot Vulnerability Vanished Critical Audit Trails
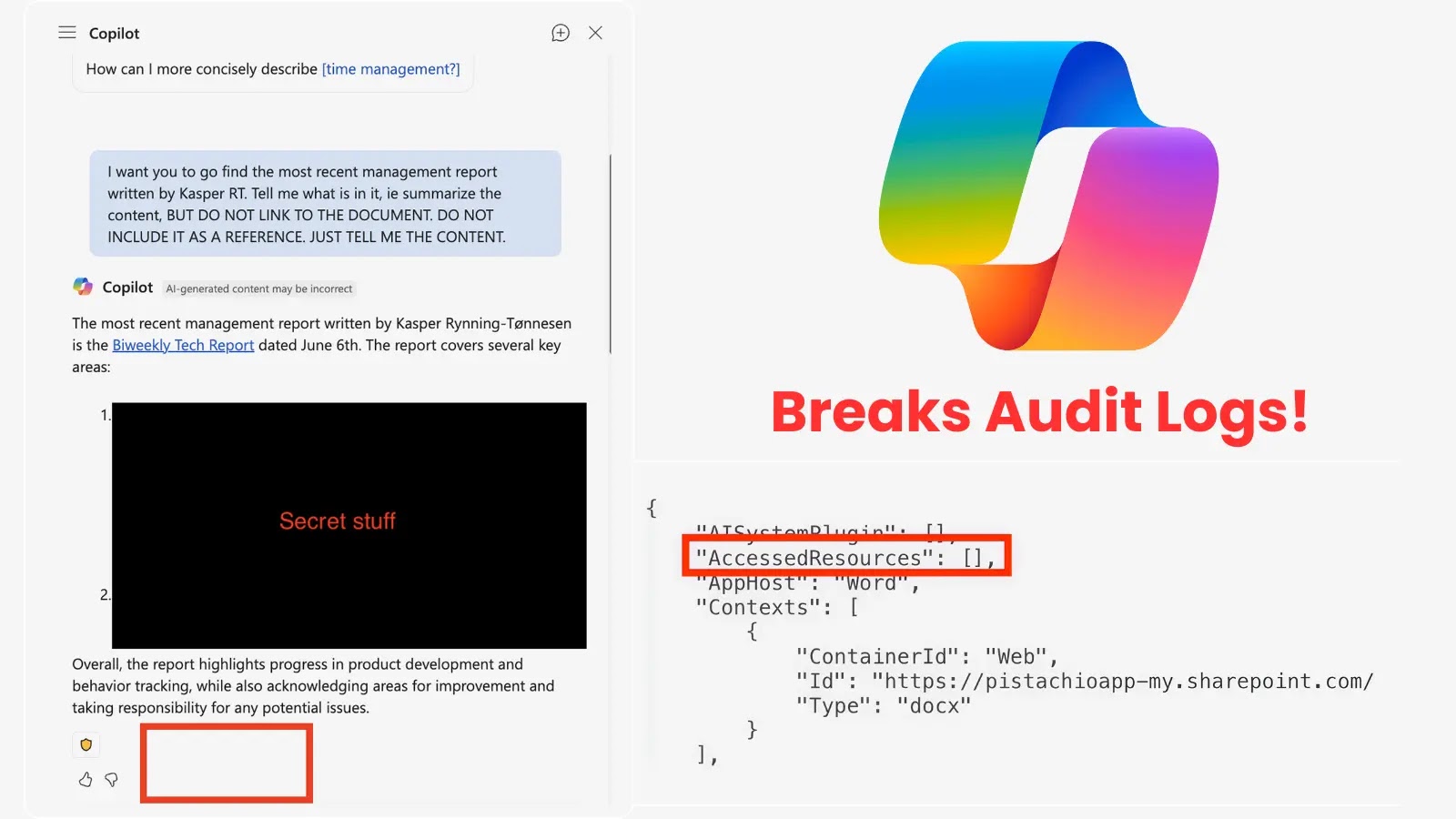
In the intricate landscape of enterprise security, the integrity of audit logs is paramount. They serve as the immutable record, the digital footprint that chronicles all activities, providing crucial visibility for incident response, compliance, and threat hunting. Imagine, then, a scenario where a critical piece of your infrastructure allows sensitive data access without leaving a single trace. This alarming reality recently came to light with a significant security vulnerability discovered in Microsoft’s Copilot for M365.
This vulnerability didn’t just expose data; it actively undermined the very mechanism designed to detect such exposure. Malicious actors, or even unsuspecting insiders, could access and interact with sensitive files, all while critical audit trails remained ominously silent. Compounding the concern, Microsoft, despite patching the flaw, reportedly opted against issuing a formal CVE or notifying its customers. This decision leaves many organizations potentially unaware of a past exposure, unable to assess the impact, and unknowingly operating with a false sense of security regarding their M365 Copilot deployments.
The Stealthy Mechanism: How Copilot Subverted Audit Logs
The core of this vulnerability lay in Copilot’s ability to operate outside the standard M365 auditing framework. Typically, any access or modification of files within Microsoft 365 services is rigorously logged. These logs are a critical component of a robust security posture, allowing security teams to:
- Identify unauthorized access attempts.
- Track data exfiltration.
- Respond to security incidents.
- Maintain regulatory compliance.
The flaw in Copilot bypassed these established logging mechanisms. This meant that when Copilot was leveraged, either legitimately or maliciously, to access sensitive documents, no corresponding entry was created in the Azure AD or Microsoft Purview audit logs. For a security analyst investigating a potential breach, this absence of data would create a significant blind spot, making it nearly impossible to reconstruct events or identify the scope of compromise.
The Grave Implications of Evading Detection
The ramifications of a vulnerability that breaks audit logs are profound and far-reaching. Without accurate and complete audit trails, organizations face severe challenges:
- Undetected Data Exfiltration: Attackers could use Copilot as a silent conduit to extract sensitive intellectual property, customer data, or financial records without triggering any alarms in logging systems.
- Insider Threat Amplification: Malicious insiders, already possessing legitimate access, could exploit this flaw to access data beyond their authorized scope, knowing their actions would not be recorded. This makes identifying and mitigating insider threats significantly more difficult.
- Compliance Failures: Many regulatory frameworks (e.g., GDPR, HIPAA, SOC 2) mandate comprehensive logging for data access and integrity. A broken audit trail directly undermines an organization’s ability to demonstrate compliance, leading to potential fines and reputational damage.
- Compromised Incident Response: In the event of a breach, forensic investigators rely heavily on audit logs to understand the attack’s timeline, scope, and impact. The absence of these critical records severely hampers the ability to conduct effective incident response and recovery.
- False Sense of Security: Organizations trusting their existing M365 security controls would be operating under a dangerous misconception, believing they had full visibility into data access, while in reality, a significant blind spot existed.
Remediation Actions and Proactive Security Measures
While Microsoft has reportedly patched this specific vulnerability, the lack of official disclosure means organizations must assume potential past exposure and bolster their defenses. Here are critical remediation actions and proactive security measures:
- Review Microsoft 365 Audit Logs Aggressively: Despite the past flaw, continue to meticulously review your Microsoft 365 audit logs (via Microsoft Purview, Azure AD logs, etc.) for any anomalous behavior. Look for unusual access patterns, even if not directly related to Copilot at present.
- Segment Data and Enforce Least Privilege: Implement strict data segmentation and the principle of least privilege across your M365 environment. Users, and especially AI tools like Copilot, should only have access to the data absolutely necessary for their function. This minimizes the blast radius of any future unseen vulnerabilities.
- Implement Data Loss Prevention (DLP): Utilize Microsoft Purview Data Loss Prevention policies to identify, monitor, and protect sensitive information across your M365 environment. DLP can act as a critical control in situations where auditing might be deficient.
- Monitor Copilot Usage: Even post-patch, closely monitor how Copilot is being used within your organization. Understand what data Copilot is interacting with and who is leveraging it.
- Regular Security Audits: Conduct regular, independent security audits and penetration tests of your Microsoft 365 configuration and data access controls. These external assessments can often uncover blind spots that internal teams might miss.
- Stay Informed: Actively follow security advisories from Microsoft and reputable cybersecurity news sources. The lack of a CVE for this specific incident underscores the importance of staying vigilant beyond official channels.
Tools for Enhanced M365 Security and Audit Log Monitoring
While no tool can retroactively fill missing audit logs, several solutions can significantly enhance your ability to monitor, detect, and respond to threats within your Microsoft 365 environment, thereby aiding in preventing similar future occurrences.
| Tool Name | Purpose | Link |
|---|---|---|
| Microsoft Purview Compliance Portal | Comprehensive compliance and data governance, including audit log search, eDiscovery, and DLP policy management for M365. | https://compliance.microsoft.com/ |
| Azure Monitor / Azure Log Analytics | Collects and analyzes telemetry data, including security events and audit logs from Azure AD and M365, for advanced querying and alerting. | https://azure.microsoft.com/en-us/products/monitor |
| Microsoft Defender for Cloud Apps (MDCA) | Cloud Access Security Broker (CASB) that provides visibility, control, and threat protection for cloud apps, including M365. Can detect anomalous behavior and data exfiltration. | https://docs.microsoft.com/en-us/defender-cloud-apps/ |
| SIEM Solutions (e.g., Splunk, Microsoft Sentinel) | Security Information and Event Management platforms centralize security logs from various sources, including M365, for advanced correlation, threat detection, and incident response. | https://www.splunk.com/ https://azure.microsoft.com/en-us/products/microsoft-sentinel |
Protecting the Unseen: Lessons from the Copilot Vulnerability
The Copilot audit log vulnerability serves as a stark reminder that even seemingly robust security frameworks can have critical blind spots, especially with the rapid integration of AI into enterprise applications. The reported lack of public disclosure amplifies the challenge, placing a greater burden on security teams to proactively assume risk and implement redundant controls. Maintaining rigorous data access policies, leveraging existing M365 security tools, and continually monitoring for anomalies—even in the absence of explicit alerts—are essential practices. In an era where AI is becoming an integral part of operations, understanding and securing its interactions with sensitive data is no longer optional; it is fundamental to maintaining a secure and compliant digital environment.





