Critical Flaws in Niagara Framework Threaten Smart Buildings and Industrial Systems Worldwide
Smart buildings and industrial control systems (ICS) form the backbone of modern infrastructure, from managing colossal energy grids to optimizing essential manufacturing processes. Their seamless operation is paramount, yet their increasing connectivity introduces complex cybersecurity challenges. A recent alarming discovery by cybersecurity researchers has unveiled over a dozen critical vulnerabilities within Tridium’s Niagara Framework, a widely deployed software platform integral to these environments. These flaws, if exploited, could grant attackers unprecedented access to sensitive control systems, threatening operational continuity, data integrity, and even physical safety.
The Niagara Framework: A Critical Component
The Niagara Framework, developed by Tridium, serves as a universal software infrastructure that connects diverse devices and systems, translating data into actionable insights for building automation, industrial applications, and smart city initiatives. Its ubiquitous presence means vulnerabilities within this framework have far-reaching implications, extending across various critical sectors including commercial real estate, data centers, energy utilities, and manufacturing plants.
Understanding the Vulnerabilities: A Network-Level Threat
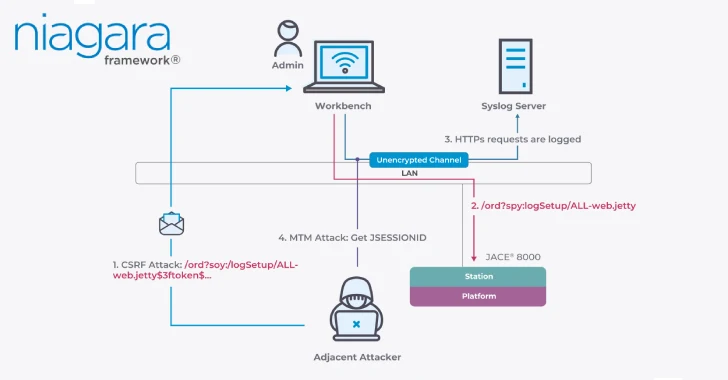
The unearthed vulnerabilities, totaling more than twelve distinct security flaws, primarily present a threat when an attacker is already present on the same network as a vulnerable Niagara system. As highlighted by Nozomi Networks Labs, the severity dramatically escalates if a system is misconfigured to disable encryption on a specific network device. This misconfiguration acts as a critical enabler, transforming theoretical vulnerabilities into fully exploitable pathways for attackers.
While specific CVE details beyond the reported findings are still emerging, the nature of these vulnerabilities suggests potential for various attack vectors, including:
- Information Disclosure: Exposure of sensitive system configurations, user credentials, or operational data.
- Authentication Bypass: Gaining unauthorized access to the Niagara system by circumventing authentication mechanisms.
- Remote Code Execution (RCE): The ability for an attacker to execute arbitrary code on the vulnerable system, leading to complete compromise.
- Denial of Service (DoS): Disrupting the normal operation of the Niagara system, potentially halting critical building or industrial processes.
The Peril of Misconfiguration: Amplifying Risk
The statement from Nozomi Networks Labs underscores a crucial point: “These vulnerabilities are fully exploitable if a Niagara system is misconfigured, thereby disabling encryption on a specific network device.” This emphasizes that while the vulnerabilities exist within the framework, human error or oversight in configuration can dramatically lower the bar for exploitation. Misconfigurations that inadvertently disable encryption effectively expose network communications, making it trivial for an attacker on the same network to intercept, alter, or inject malicious data. This scenario bypasses many common network defenses, making the attack highly effective once inside the perimeter.
Remediation Actions and Mitigations
Addressing these critical vulnerabilities requires a multi-faceted approach, combining immediate technical actions with long-term security best practices. System owners and operators of Niagara Framework deployments should prioritize the following:
- Patch Management: Tridium will likely release patches addressing these vulnerabilities. Immediately apply all available security updates and patches from Tridium once they are released. Regularly check for firmware and software updates for all connected devices and systems.
- Network Segmentation: Implement robust network segmentation to isolate critical ICS/OT (Operational Technology) networks from IT networks and the internet. This limits the lateral movement of attackers even if an initial compromise occurs.
- Strong Encryption Enforcement: Meticulously review and configure all Niagara systems to ensure strong encryption is enabled and utilized for all network communications. Disable any features that allow for unencrypted communication unless absolutely necessary and thoroughly mitigated otherwise.
- Principle of Least Privilege: Enforce the principle of least privilege for all users and services interacting with the Niagara Framework. Grant only the minimum necessary permissions required for operations.
- Regular Security Audits: Conduct regular penetration testing and vulnerability assessments of your Niagara Framework deployments and associated network infrastructure. Pay close attention to configuration auditing to proactively identify and rectify misconfigurations.
- Intrusion Detection/Prevention Systems (IDS/IPS): Deploy and properly configure IDS/IPS solutions capable of monitoring ICS/OT network traffic for anomalous behavior and known attack signatures.
- Employee Training: Educate IT and OT personnel on the importance of secure configurations, patch management, and general cybersecurity hygiene.
Tools for Detection and Mitigation
Leveraging specialized tools can significantly aid in identifying and mitigating risks associated with critical infrastructure systems like those powered by Niagara.
| Tool Name | Purpose | Link |
|---|---|---|
| Nessus | Vulnerability Scanning and Assessment | https://www.tenable.com/products/nessus |
| Shodan | Internet-connected device search engine (for identifying exposed systems) | https://www.shodan.io/ |
| Wireshark | Network Protocol Analyzer (for traffic analysis and anomaly detection) | https://www.wireshark.org/ |
| OpenVAS / Greenbone Community Edition | Vulnerability Management Solution | https://www.greenbone.net/en/community-edition/ |
Looking Ahead: Securing Critical Infrastructure
The discovery of these critical flaws in the Niagara Framework underscores the ongoing and evolving challenges in securing smart buildings and industrial systems. As these environments become more interconnected and reliant on software platforms, the attack surface expands. Proactive vulnerability research, diligent patch management, robust network architecture, and continuous security monitoring are not merely recommendations; they are imperative for maintaining the integrity, availability, and safety of the critical infrastructure that powers our world. Owners and operators must treat cybersecurity as an integral part of operational risk management, ensuring that foundational platforms like the Niagara Framework are hardened against present and future threats. Stay informed by monitoring official advisories from Tridium and cybersecurity research organizations.





