Critical Golden dMSA Attack in Windows Server 2025 Enables Cross-Domain Attacks and Persistent Access
Unveiling the Critical Golden dMSA Attack: A Major Security Flaw in Windows Server 2025
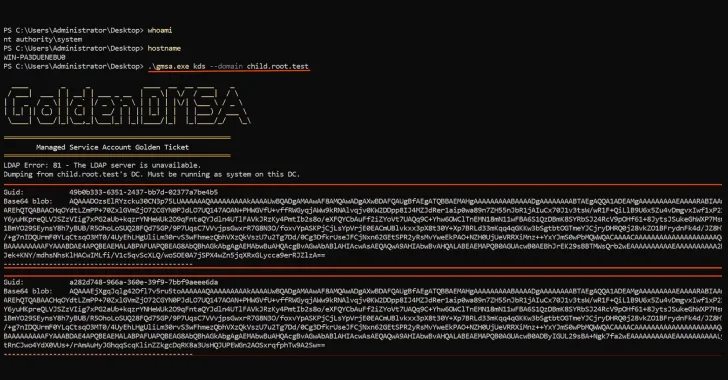
A significant cybersecurity threat has emerged with the disclosure of a “critical design flaw” within delegated Managed Service Accounts (dMSAs) in Windows Server 2025. This vulnerability, dubbed the “Golden dMSA Attack,” poses an unprecedented risk to Active Directory environments, enabling attackers to achieve widespread lateral movement and persistent access across multiple domains. For organizations relying on the latest Windows Server iterations, understanding and addressing this flaw is paramount to maintaining a robust security posture.
Understanding Managed Service Accounts (MSAs) and Delegated MSAs (dMSAs)
To fully grasp the severity of the Golden dMSA Attack, it’s essential to understand the underlying technologies it exploits. Managed Service Accounts (MSAs) were introduced by Microsoft to provide automatic password management and simplified service principal name (SPN) management for services running on Windows servers. This innovation aimed to reduce the administrative overhead associated with traditional service accounts and enhance security by preventing hardcoded passwords.
- Standalone MSAs (sMSAs): Designed for a single computer running a service.
- Group MSAs (gMSAs): Allow multiple servers to run a service under the same identity, distributing the service load while centralizing credential management.
Windows Server 2025 introduced delegated Managed Service Accounts (dMSAs), a feature intended to further streamline the management of services across complex Active Directory environments. dMSAs allow administrators to delegate the management and usage of MSAs more granularly. While this feature enhances operational flexibility, the newly discovered design flaw turns this delegation into a critical vulnerability.
The Golden dMSA Attack: A Deep Dive into the Flaw
Cybersecurity researchers at Semperis have identified what they describe as a “critical design flaw” in how dMSAs are implemented and managed within Windows Server 2025. This flaw, currently awaiting a CVE assignment (e.g., potential placeholder CVE-2025-XXXXX), allows malicious actors to leverage the inherent trust mechanisms within Active Directory to achieve devastating consequences.
The core of the Golden dMSA Attack lies in its ability to compromise the integrity of dMSAs, effectively forging credentials or manipulating trust relationships. This enables attackers to:
- Cross-Domain Lateral Movement: Gain unauthorized access to resources and systems across different Active Directory domains linked by trust. This is particularly dangerous in large enterprise environments with complex multi-domain structures.
- Persistent Access: Establish indefinite access to all managed service accounts and their associated resources. This means an attacker, once inside, can maintain a foothold without detection for extended periods, even surviving password changes or service restarts.
- High-Impact Attacks: The compromise of MSAs, which often run critical services, provides attackers with elevated privileges, potentially leading to data exfiltration, system disruption, or full domain compromise.
The severity of this attack is comparable to other “Golden Ticket” type attacks against Kerberos, but specifically targets the delegated nature of dMSAs, creating a new vector for persistent and pervasive compromise within Active Directory.
Impact and Consequences
The implications of a successful Golden dMSA Attack are severe for any organization deploying Windows Server 2025. The attack fundamentally undermines the security benefits intended by MSAs and dMSAs. Organizations could face:
- Complete Domain Compromise: Attackers can gain administrative control over entire domains, leading to widespread data theft, alteration, or destruction.
- Business Disruption: Critical services running under compromised MSAs can be shut down, modified, or used as platforms for further attacks, leading to operational downtime and financial losses.
- Regulatory Non-Compliance: Data breaches resulting from such an attack can lead to hefty fines and reputational damage due to non-compliance with data protection regulations.
- Loss of Trust: Customers and partners may lose trust in an organization’s ability to protect their data, impacting long-term business relationships.
Remediation Actions and Mitigation Strategies
Given the critical nature of the Golden dMSA Attack, immediate and proactive measures are essential. Organizations running or planning to deploy Windows Server 2025 must prioritize these remediation actions:
- Apply Vendor Patches: The most crucial step is to apply all official security patches released by Microsoft as soon as they become available. Monitor Microsoft’s security advisories closely for updates related to dMSAs and Active Directory.
- Review dMSA Implementations: Conduct a thorough audit of all delegated Managed Service Accounts. Identify all services utilizing dMSAs and assess the scope of their delegated permissions. Limit delegation to the absolute minimum required for operational functionality.
- Principle of Least Privilege: Ensure that all service accounts, including dMSAs, operate with the lowest possible privileges necessary to perform their functions. Avoid granting excessive permissions that could be exploited.
- Enhanced Monitoring and Logging: Implement robust logging and monitoring for Active Directory, focusing on dMSA-related events, account creation, permission changes, and authentication attempts. Look for anomalous behavior, such as unusual access patterns or attempts to modify dMSA properties.
- Regular Active Directory Audits: Perform frequent security audits of your Active Directory environment to detect misconfigurations, dormant accounts, or signs of compromise.
- Network Segmentation: Implement network segmentation to isolate critical services and domains. This can limit the lateral movement capabilities of an attacker even if a dMSA is compromised.
- Incident Response Plan: Ensure your incident response plan is up-to-date and includes procedures for addressing Active Directory compromises and credential theft.
- Educate Administrators: Train your IT and security teams on the risks associated with service accounts, dMSAs, and the importance of secure configuration practices.
Tools for Detection and Mitigation
Leveraging specialized tools can aid in the detection of dMSA misconfigurations or the presence of an attacker exploiting this vulnerability.
| Tool Name | Purpose | Link |
|---|---|---|
| Active Directory Health Check Tools | General AD health and security posture assessment. | (Refer to vendor-specific tools like Microsoft’s Active Directory Best Practices Analyzer or third-party solutions) |
| Security Information and Event Management (SIEM) Systems | Centralized logging and real-time threat detection for AD events. | (e.g., Splunk, Microsoft Sentinel) |
| Identity Governance and Administration (IGA) Solutions | Manage and audit access permissions, including dMSA delegations. | (Refer to enterprise IGA solutions) |
| Incident Response Tools | Forensic analysis and threat containment during/after an attack. | (e.g., Volatility, Kape) |
Conclusion
The discovery of the critical design flaw in delegated Managed Service Accounts within Windows Server 2025 represents a significant challenge for cybersecurity professionals. The Golden dMSA Attack’s potential for cross-domain lateral movement and indefinite persistent access makes it a high-priority threat demanding immediate attention. By understanding the mechanics of this flaw, implementing robust remediation actions, and continuously monitoring Active Directory environments, organizations can significantly reduce their exposure and protect their critical assets from this new and potent form of attack.





