Cursor, Windsurf & Google Antigravity IDEs Recommend Malicious App Extension to Developers
Navigating the AI-Powered IDE Minefield: Malicious Extension Recommendations Threaten Developer Security
The landscape of software development is undergoing a rapid transformation, driven by innovative AI-powered Integrated Development Environments (IDEs). Tools like Cursor, Windsurf, and Google Antigravity promise enhanced productivity and streamlined workflows. However, a recent, critical security vulnerability has cast a shadow over these advancements, exposing millions of developers to the risk of inadvertently installing malicious software extensions. This flaw, rooted in the very mechanisms designed to assist developers, highlights a significant supply chain security concern within the development ecosystem.
The Vulnerability Explained: Ghost Extensions and Execution Risks
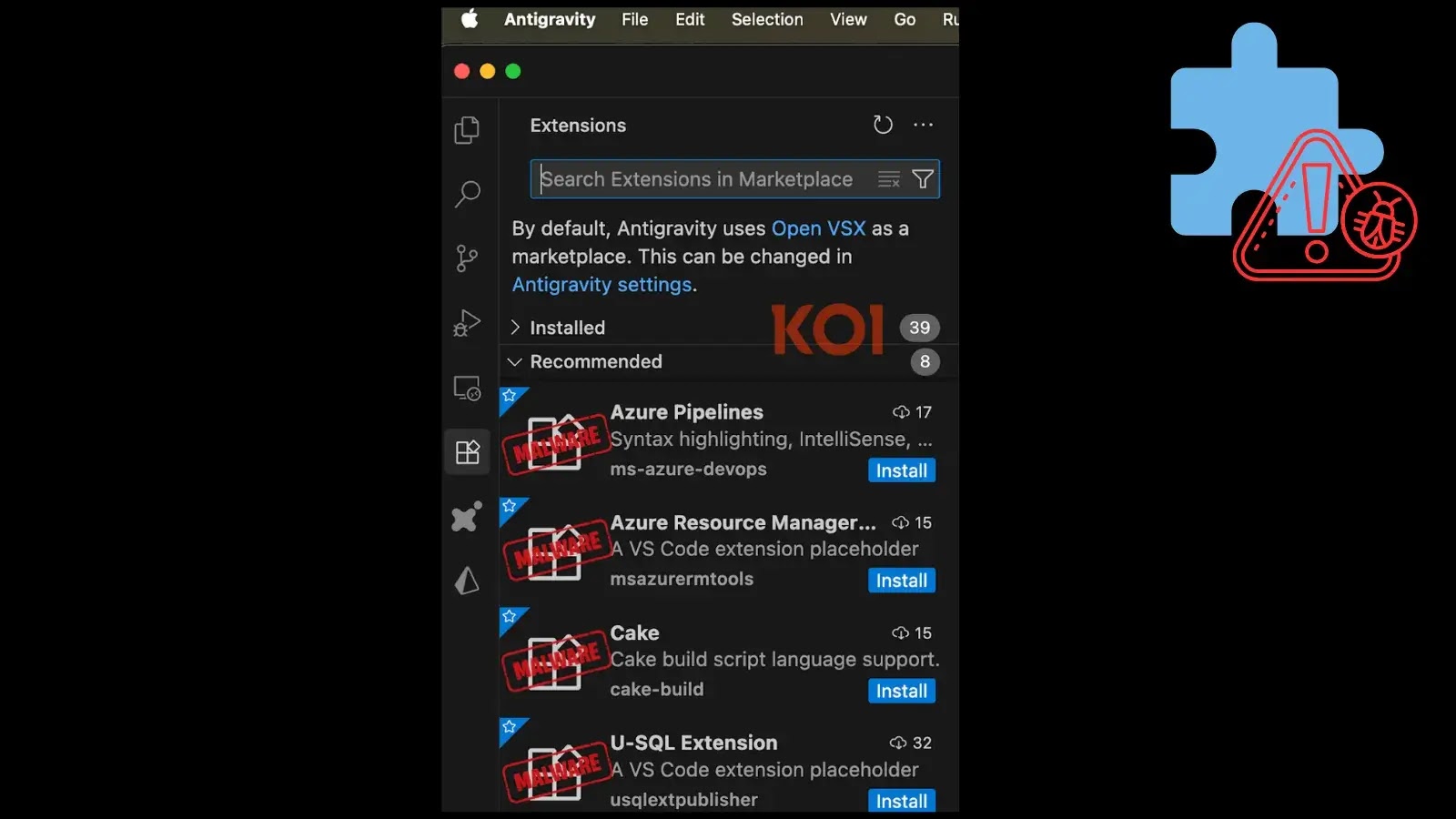
At the heart of this issue lies a concerning vulnerability where popular AI-powered IDEs recommend extensions that, quite simply, do not exist in their respective marketplaces. Specifically, Cursor, Windsurf, and Google Antigravity IDEs, collectively boasting over a million users, have been observed suggesting non-existent extensions. These tools, all forked from VSCode, appear to have inherited or introduced configuration flaws that lead to these erroneous recommendations.
When an IDE recommends an extension, especially one that doesn’t have a legitimate source, it creates an opportunity for attackers. A developer, trusting their development environment, might attempt to install such an extension. In a scenario where an attacker controls a domain or package repository that aligns with the non-existent extension’s name, they could publish a malicious version. The developer, attempting to install the recommended “ghost” extension, would then unknowingly download and execute attacker-controlled code, leading to:
- System Compromise: Remote code execution, backdoor installation, or data exfiltration.
- Credential Theft: Capture of API keys, authentication tokens, and source code repository credentials.
- Supply Chain Attacks: Malicious code injection into projects, impacting downstream users and customers.
While specific CVE numbers for this broad issue are still emerging, the underlying principle aligns with vulnerabilities like CVE-2023-38831, which involves package manager confusion or typosquatting, leading to the installation of unintended or malicious software.
Impact on Developers and the Software Supply Chain
The immediate impact on developers is substantial. Unwittingly installing malicious extensions can lead to compromised workstations, stolen intellectual property, and a complete breakdown of development security. Beyond the individual developer, the implications extend to the entire software supply chain:
- Project Integrity: Malicious extensions could alter source code, inject backdoors, or compromise build processes.
- Reputational Damage: Companies whose software is developed using compromised IDEs face significant reputational and financial costs.
- Trust Erosion: The incident erodes trust in AI-powered development tools, which are designed to enhance security and efficiency, not introduce new risks.
This situation underscores the critical need for robust validation mechanisms within IDEs and extension marketplaces, especially as AI plays a more central role in recommending and automating development tasks.
Remediation Actions and Best Practices
Addressing this vulnerability requires a multi-faceted approach, combining immediate remediation with long-term security best practices:
For Developers:
- Verify Extension Authenticity: Before installing any extension, always cross-reference its existence and legitimacy on the official marketplace (e.g., VSCode Marketplace, respective IDE marketplaces).
- Scrutinize Source Code: Whenever possible, review the source code of extensions, particularly open-source ones, for suspicious activity.
- Principle of Least Privilege: Run IDEs and development tools with the minimum necessary permissions.
- Regular Updates: Keep your IDEs and all installed extensions updated to the latest versions to benefit from security patches.
- Utilize Sandboxing: Consider using virtual environments or containerization for development to isolate potential threats.
For IDE Vendors (Cursor, Windsurf, Google Antigravity, etc.):
- Implement Robust Validation: Enhance mechanisms for verifying the existence and integrity of recommended extensions against official registries.
- Clear User Warnings: Implement prominent warnings when an IDE suggests an extension that cannot be verified or is not found in a legitimate marketplace.
- Security Audits: Conduct regular, thorough security audits of the IDE’s configuration files and extension recommendation logic.
- Transparency: Clearly communicate security posture and incident response plans to users.
Tools for Detection and Mitigation
To aid in detecting and mitigating similar threats, developers and security teams can leverage various tools:
| Tool Name | Purpose | Link |
|---|---|---|
| OWASP Dependency-Check | Identifies known vulnerabilities in project dependencies. | OWASP Dependency-Check |
| Snyk | Finds and fixes vulnerabilities in your code, dependencies, containers, and infrastructure. | Snyk |
| TruffleHog | Scans repositories for exposed secrets. | TruffleHog |
| VSCode Extension Manager | Manually verify installed extensions and their sources. | (Built into VSCode) |
| Containerization Tools (e.g., Docker) | Isolate development environments from host systems. | Docker |
Conclusion: Strengthening the Development Supply Chain
The discovery of AI-powered IDEs recommending non-existent, potentially malicious extensions serves as a stark reminder of the continuous challenges in securing the software supply chain. As development environments become increasingly intelligent and interconnected, the attack surface expands. Developers must adopt a heightened sense of vigilance, verifying every component introduced into their workflow. Simultaneously, IDE vendors bear the crucial responsibility of implementing robust security controls and transparency to build and maintain user trust. Proactive security measures, coupled with a commitment to continuous monitoring and education, are essential to safeguard the integrity of software development in an AI-driven era.





