Cybersecurity in IoT Devices: Challenges and Solutions.
Internet of Things Cybersecurity In: IoT Device Challenges and Solutions Secure IoT
In the burgeoning age of IoT, securing Internet of Things devices is paramount. The proliferation of connected devices has revolutionized industries and daily life, but it has also introduced significant challenges. This article explores the complex landscape of IoT cybersecurity, detailing the security risks inherent in the IoT ecosystem and presenting effective security solutions to protect IoT devices and networks.
Understanding IoT and Its Security Landscape
Overview of the Internet of Things
The Internet of Things represents a vast network of interconnected devices, ranging from smart home appliances to sophisticated industrial sensors. These IoT devices often communicate and exchange data over the IoT network, enabling automation, remote monitoring, and enhanced efficiency. The IoT system’s architecture includes various components, such as sensors, actuators, network infrastructure, and cloud platforms. However, this interconnectedness also expands the attack surface, making securing Internet of Things devices a critical concern. The Internet of Things offers many benefits, yet realizing its full potential requires addressing its inherent security issues comprehensively.
The Importance of IoT Security
IoT security is crucial due to the potential impact of security breaches on individuals, businesses, and critical infrastructure. Compromised IoT devices can be leveraged to launch cyber attacks, steal sensitive data, or disrupt essential services. The lack of robust security measures in many IoT devices often makes them easy targets for cyber threats. A single vulnerability in an IoT device can provide access to an entire IoT network, leading to widespread damage and highlighting the risks associated with IoT devices. Therefore, implementing effective security strategies is not just a matter of best practice but a necessity for maintaining trust and ensuring the reliable operation of IoT environments.
Key Components of the IoT Ecosystem
The IoT ecosystem comprises several essential components, each requiring careful attention to security. IoT devices and software form the foundation, collecting and processing data from the physical world. These IoT devices often have limited processing power and memory, making it challenging to implement advanced security features. The IoT network enables communication between devices and the cloud, while cloud platforms provide storage, analytics, and application services. Each of these elements introduces potential security vulnerabilities that must be addressed through comprehensive security measures and regular security updates. The complexity of the IoT ecosystem demands a holistic approach to IoT cybersecurity to ensure that all components are adequately protected.
Common IoT Security Challenges
Identifying Security Risks in IoT Devices
Identifying security risks in IoT devices is the first step toward effective IoT security. Many IoT devices are designed with minimal security measures, making them vulnerable to cyber threats. Common vulnerabilities include weak default passwords, unencrypted data transmission, and a lack of regular security updates. These vulnerabilities can be exploited by attackers to gain unauthorized access to IoT devices and networks, underscoring the importance of addressing IoT security threats. Thorough risk assessments and penetration testing are essential to uncover these weaknesses. Recognizing these security risks is vital for developing security strategies that secure IoT environments and protect IoT devices from potential cybersecurity attacks and ensuring the security of IoT. Our commitment is to ensure your IoT ecosystem is fortified against these cybersecurity challenges.
Analysis of Security Breaches in IoT
An analysis of security breaches in IoT reveals patterns and trends that can inform security strategies for the security of IoT devices. Real-world incidents highlight the potential consequences of inadequate IoT security, ranging from data theft to physical harm. Attackers often target IoT devices due to their widespread deployment and weak security measures. For example, compromised smart home IoT devices can be used to launch distributed denial-of-service (DDoS) attacks, while vulnerabilities in industrial IoT devices can disrupt critical infrastructure. By studying past security breaches, organizations can learn valuable lessons and proactively implement security solutions to mitigate future cybersecurity challenges. Understanding these incidents is crucial for enhancing cybersecurity in the age of IoT. We focus on best practices for IoT security to ensure your Internet of Things devices are well-protected against cyber attacks.
Addressing IoT Security Challenges
Addressing IoT security challenges requires a multi-faceted approach that encompasses technology, policy, and education. Implementing essential security measures is key; these include:
- Implementing strong authentication mechanisms.
- Encrypting data in transit and at rest.
- Regularly updating IoT devices and software is essential for ensuring the security of IoT and mitigating potential risks associated with IoT devices.
Organizations must also establish clear security policies and procedures to govern the use of IoT technology and conduct regular security audits to identify and remediate vulnerabilities. Employee training is vital to raise awareness about cyber threats and promote secure IoT practices. By taking these steps, businesses can reduce the security risks associated with IoT and protect IoT devices from cybersecurity attacks while keeping security in mind. Our aim is to provide you with comprehensive security to secure IoT and ensure peace of mind in the age of IoT.
Cybersecurity Threats in the Age of IoT
Understanding Cybersecurity Threats to IoT Devices
Understanding cybersecurity threats to IoT devices is fundamental to maintaining a robust IoT security posture in the age of IoT. Many IoT devices are designed with limited processing power and memory, making it difficult to implement complex security measures. These limitations can render IoT devices and networks vulnerable to various cyber threats, including malware infections, data breaches, and unauthorized access. Attackers often exploit vulnerabilities in IoT devices to gain a foothold in the IoT ecosystem, using them as entry points to compromise entire IoT networks. Therefore, a thorough understanding of potential security risks is essential for securing Internet of Things devices and ensuring the security of IoT. Teamwin Global Technologica is dedicated to providing the security solutions you need to secure IoT.
Impact of Cybersecurity Threats on IoT Networks
The impact of cybersecurity threats on IoT networks can be far-reaching and devastating. A successful attack on an IoT network can disrupt critical services, compromise sensitive data, and even cause physical harm. For example, a cyber attack on industrial IoT devices could lead to malfunctions in manufacturing processes, resulting in significant financial losses and safety hazards. Similarly, compromised smart home IoT devices can expose personal information and enable unauthorized access to homes, presenting significant IoT security threats. The interconnected nature of the IoT ecosystem means that a single vulnerability can have cascading effects, amplifying the potential damage. Addressing these cybersecurity challenges effectively is critical for maintaining the integrity and reliability of IoT systems and protecting IoT devices.
Case Studies of IoT Cybersecurity Incidents
Analyzing case studies of IoT security incidents provides valuable insights into the types of cybersecurity threats that IoT devices and networks face and the consequences of security breaches. Several high-profile attacks have demonstrated the potential for cyber criminals to exploit vulnerabilities in IoT devices for malicious purposes. These incidents often highlight common security issues such as weak passwords, unencrypted communication, and a lack of security updates, which are critical for ensuring the security of IoT devices. Studying these security breaches can help organizations better understand the security risks associated with IoT and implement security strategies to protect IoT devices and mitigate future cybersecurity challenges. By learning from past incidents, businesses can enhance their cybersecurity and secure IoT.
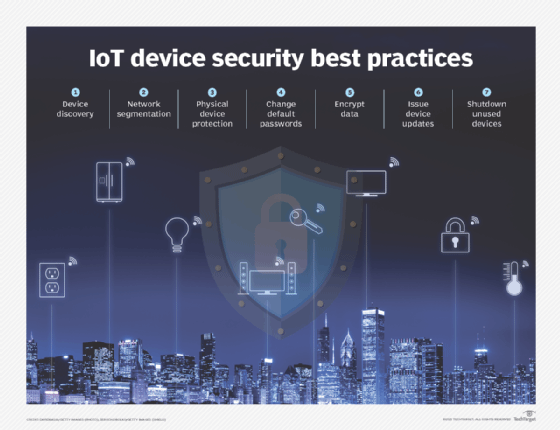
Best Practices for Securing IoT Devices
Implementing Effective IoT Device Security Measures
Implementing effective IoT device security measures requires a holistic approach that addresses both the technical and organizational aspects of IoT security. Some key areas to focus on include:
- Enforcing strong authentication and authorization mechanisms to control access to IoT devices and networks.
- Regular security updates and patch management for addressing known vulnerabilities in IoT devices and software.
Organizations should also establish clear security policies and procedures to govern the use of IoT technology and conduct regular security audits to identify and remediate potential weaknesses in the security of IoT devices. These proactive security strategies are essential for securing Internet of Things devices. Teamwin Global Technologica remains committed to delivering comprehensive security
Security Challenges and Best Practices for IoT Ecosystem
The IoT ecosystem presents unique security challenges due to its distributed nature and the diversity of IoT devices and networks, making the challenges of IoT particularly complex. One significant challenge is the lack of standardization in IoT security, which can make it difficult to implement consistent security measures across different IoT devices. To address this, organizations should adopt several security best practices, such as ensuring the security of IoT devices and recognizing the risks associated with IoT devices.
- Adopting a layered security approach that incorporates multiple layers of protection, including network security, IoT device security, and data security.
- Segmenting the IoT network to isolate critical IoT devices from the rest of the network, limiting the potential impact of a cybersecurity incident.
By implementing these security solutions, organizations can enhance cybersecurity and secure IoT. Our goal is to protect IoT devices from the many targets that there are.
Future Trends in IoT Cybersecurity
As the Internet of Things continues to evolve, so too will the landscape of IoT cybersecurity, presenting new challenges of IoT that must be addressed. Future trends in IoT cybersecurity include the increasing use of artificial intelligence (AI) and machine learning (ML) to detect and respond to cyber threats. AI-powered security tools can analyze large volumes of data to identify anomalous behavior and predict potential attacks, enabling organizations to proactively secure IoT. Another trend is the adoption of blockchain technology to enhance the security and integrity of IoT data. Blockchain can provide a tamper-proof ledger of IoT transactions, making it more difficult for attackers to compromise IoT devices and networks. Teamwin Global Technologica is at the forefront of these advancements, ensuring that our clients are prepared for the cybersecurity challenges of tomorrow.
Surprising Facts about Cybersecurity in IoT Devices
- Over 70% of IoT devices are vulnerable to hacking due to weak security protocols.
- Many IoT devices lack the capability for software updates, leaving them exposed to new threats.
- Cyberattacks on IoT devices have increased by over 300% in the past year.
- IoT devices can often be used as entry points for larger network breaches, compromising entire systems.
- Only 15% of organizations have a dedicated cybersecurity strategy for IoT devices.
What are the common IoT security challenges?
Common IoT security challenges include the vast number of insecure IoT devices, lack of built-in security measures, and the difficulty in managing security across a diverse ecosystem. These challenges pose significant risks as many devices come with default settings that are not secure, making them vulnerable to attacks.
How do cybersecurity threats affect IoT devices?
Cybersecurity threats can lead to significant security breaches in IoT devices. Attackers can gain access to these devices and the networks they are connected to, potentially compromising sensitive data and disrupting services. Understanding these threats is essential for implementing effective cybersecurity measures.
What are the best practices for IoT device security?
Best practices for IoT device security include ensuring all devices are designed with security in mind, regularly updating software for IoT devices, and implementing robust security controls. Additionally, adhering to security standards can help mitigate risks associated with IoT security breaches.
How can organizations address IoT security challenges?
Organizations can address IoT security challenges by conducting regular security assessments, employing strong authentication methods, and ensuring end-to-end encryption for data transmission. Training staff on cybersecurity awareness is also crucial for enhancing overall security posture.
What are the unique challenges posed by IoT devices in healthcare?
IoT devices in healthcare pose unique challenges due to the sensitive nature of health data they collect. Ensuring the privacy and security of this data is paramount, and implementing stringent security measures is necessary to protect against unauthorized access and potential security breaches.
What cybersecurity measures should be taken for IoT ecosystems?
Cybersecurity measures for IoT ecosystems should include continuous monitoring for threats, deploying advanced threat detection tools, and ensuring regular updates and patches are applied to devices. This proactive approach can significantly reduce vulnerabilities across the IoT ecosystem.
How do security breaches occur in IoT devices?
Security breaches in IoT devices often occur due to weak passwords, outdated software, and lack of encryption. Many IoT devices are left unprotected, allowing attackers to exploit these vulnerabilities to gain unauthorized access and control over the devices.
What are the implications of IoT cybersecurity threats for businesses?
The implications of IoT cybersecurity threats for businesses include potential financial losses, damage to reputation, and legal consequences. As IoT devices continue to proliferate, businesses must prioritize IoT device security to protect their assets and maintain customer trust.