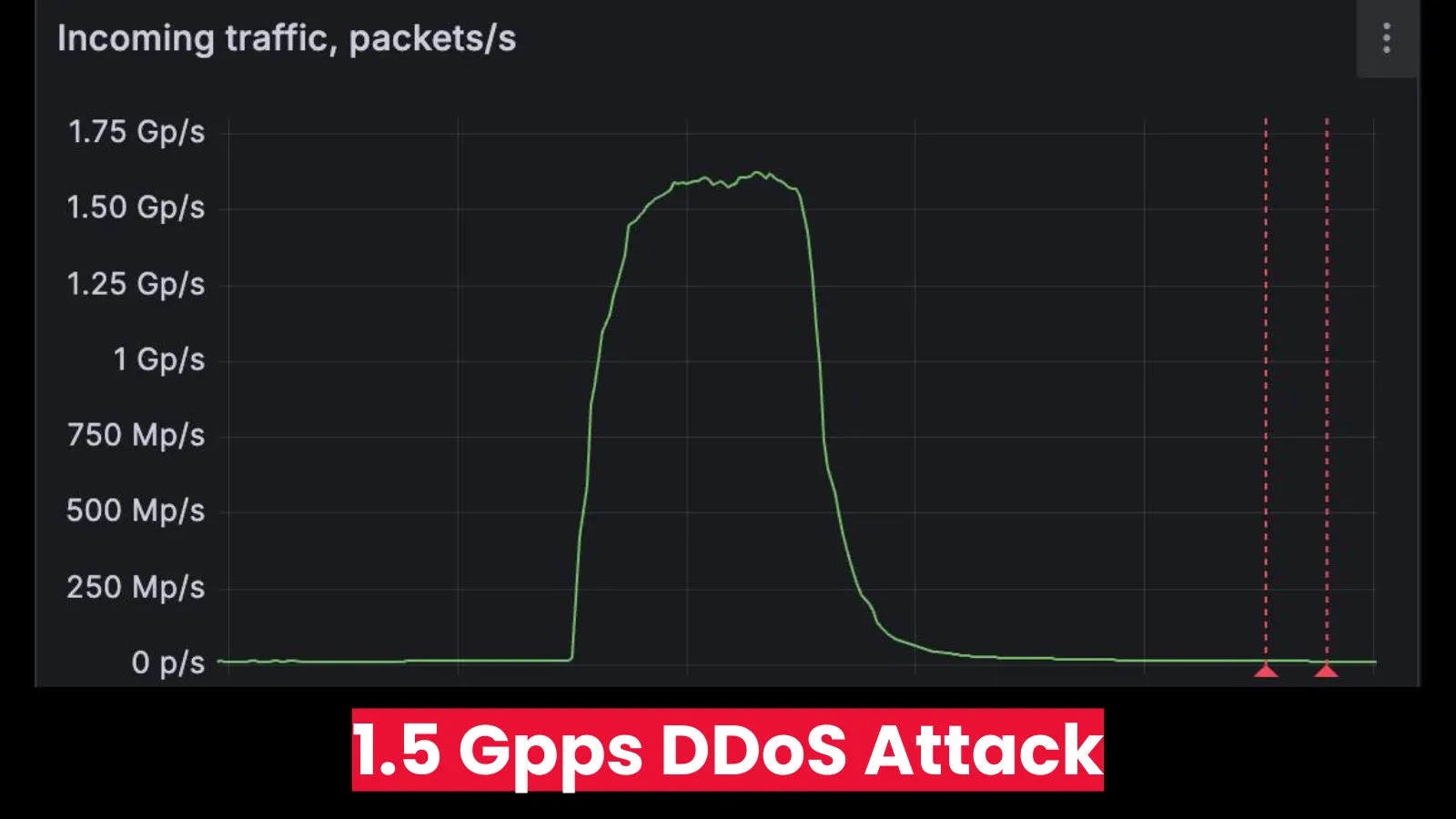
DDoS Mitigation Provider targeted In 1.5 Gpps 1.5 Billion Packets per Second DDoS Attack
The digital landscape is a constant battleground, and even the most prepared organizations can find themselves under unprecedented assault. This week, the cybersecurity community received a stark reminder of the escalating scale of Distributed Denial of Service (DDoS) attacks, as FastNetMon, a leading DDoS detection solution provider, disclosed a record-breaking incident. This attack didn’t target a small business or a personal website; it aimed squarely at a major DDoS scrubbing vendor in Western Europe, pushing packet-forwarding rates to an unfathomable 1.5 billion packets per second (1.5 Gpps). This event underscores the critical need for robust DDoS mitigation strategies and highlights the evolving sophistication of threat actors.
The Anatomy of a Gigascaled DDoS Attack
A DDoS attack of this magnitude, clocking in at 1.5 Gpps, isn’t just about overwhelming a target with traffic; it signifies a coordinated, resource-intensive operation designed to cripple even dedicated mitigation infrastructure. While the specific attack vectors were not detailed in the initial reports, such high packet-per-second rates often indicate sophisticated layer 3/4 amplification or reflection attacks. These methods leverage misconfigured servers or services (e.g., DNS, NTP, Memcached) to amplify small queries into massive responses directed at the victim, generating immense malicious traffic volumes. The sheer scale demonstrates attackers’ access to significant botnet resources or highly effective amplification techniques. The targeting of a scrubbing vendor is particularly noteworthy, suggesting an attempt to disable the very defenses designed to protect others, creating a cascade effect of vulnerability.
Why DDoS Mitigation Providers Become Targets
One might wonder why an attacker would target a DDoS mitigation provider. The answer is multi-faceted:
- Strategic Impact: Successfully disabling a major scrubbing center means countless clients relying on that service lose their primary line of defense, opening them up to future attacks.
- Proof of Capability: A successful attack against a mitigation specialist serves as a dangerous demonstration of the attacker’s power and technical prowess, potentially attracting “customers” for their illicit services.
- Reconnaissance: Such attacks can also be reconnaissance missions, probing the defenses of a mitigation provider to identify weaknesses that could be exploited in future, more targeted assaults.
- Disruption of Service: The primary goal remains disruption. By taking out the defenders, attackers indirectly achieve their objective of taking down client services.
The Significance of 1.5 Billion Packets Per Second
To grasp the scale of 1.5 Gpps, consider that traditional network infrastructure typically handles traffic in megabits or gigabits per second. While throughput (bits per second) is a common metric, packet rate (packets per second) is a more critical indicator of a network device’s processing strain. Each packet requires processing: header parsing, routing lookups, and potentially security checks. At 1.5 billion packets per second, even specialized hardware struggles to keep up. This volume can exhaust CPU resources, fill routing tables, overwhelm firewalls, and saturate network interfaces, leading to complete service outages. This incident stands as one of the largest packet-per-second attacks ever publicly disclosed, surpassing previous records and setting a new benchmark for extreme DDoS. While no specific CVE is associated with the attack itself, the underlying amplification techniques often exploit vulnerabilities or misconfigurations in unpatched systems, highlighting the importance of regular vulnerability management.
Remediation Actions and Best Practices for DDoS Defense
While the immediate details of how FastNetMon and the scrubbing vendor mitigated this specific attack are proprietary, the incident reinforces several fundamental principles for robust DDoS defense:
- Multi-Layered Defense: Relying on a single line of defense is insufficient. Organizations need a combination of on-premise hardware, cloud-based scrubbing services, and intelligent traffic analysis.
- Traffic Anomaly Detection: Implement advanced anomaly detection systems capable of identifying sudden spikes in packet rates or unusual traffic patterns that deviate from normal baselines. This includes leveraging tools that can analyze flow data (e.g., NetFlow, IPFIX).
- Hybrid Mitigation: For attacks of this scale, a hybrid approach combining always-on protection with on-demand cloud scrubbing is essential. On-premise solutions can handle smaller, more frequent attacks, while cloud services absorb the massive volumetric assaults.
- Regular Stress Testing: Proactively test DDoS mitigation capabilities to identify weaknesses before a real attack occurs. This involves simulated attacks and capacity planning.
- Network Redundancy and Scalability: Ensure network infrastructure is designed with redundancy at all critical points and can scale to handle unexpected traffic surges.
- Collaborate with ISPs and Security Vendors: Establish strong relationships with Internet Service Providers (ISPs) and specialized DDoS mitigation vendors. They can offer upstream filtering and expert assistance during an attack.
- Application Layer Protections: While volumetric attacks focus on network layers, don’t neglect application layer DDoS. Web Application Firewalls (WAFs) and rate limiting are crucial.
Relevant Tools for DDoS Mitigation
| Tool Name | Purpose | Link |
|---|---|---|
| FastNetMon | High-performance DDoS detection software for network engineers. | |
| Cloudflare Magic Transit | Cloud-based network-layer DDoS protection and traffic acceleration. | |
| Akamai Prolexic | Dedicated DDoS protection against volumetric, protocol, and application layer attacks. | |
| Arbor Networks (NETSCOUT) | Comprehensive DDoS detection and mitigation solutions (on-premise and cloud). | |
| AWS Shield | Manages and protects against DDoS attacks for applications on Amazon Web Services. |
Looking Ahead: The Evolving DDoS Threat Landscape
The 1.5 Gpps attack against a DDoS scrubbing vendor is a clear indicator that the threat landscape continues to escalate. Attackers are becoming more ambitious, resourceful, and capable of generating unprecedented volumes of malicious traffic. For organizations, this means a continuous investment in robust security infrastructure, proactive planning, and a deep understanding of evolving attack methodologies. Staying informed, prepared, and adaptable is not merely an option—it is a necessity for maintaining operational resilience in the face of these formidable digital threats. The cybersecurity community must continue to share insights and foster collaboration to counter these ever-growing dangers effectively.





