ECScape: Exploiting ECS Protocol on EC2 to Exfiltrate Cross-Task IAM and Execution Role Credentials
Cloud environments offer unprecedented scalability and flexibility, but they also introduce complex security challenges. A recent discovery, dubbed “ECScape,” highlights a significant vulnerability within Amazon Elastic Container Service (ECS) that could allow malicious containers to exfiltrate highly sensitive credentials from other containers on the same EC2 instance. This revelation underscores critical isolation weaknesses in multi-tenant cloud deployments and reinforces the importance of robust security architectures.
Understanding ECScape: A Cross-Task Credential Theft Technique
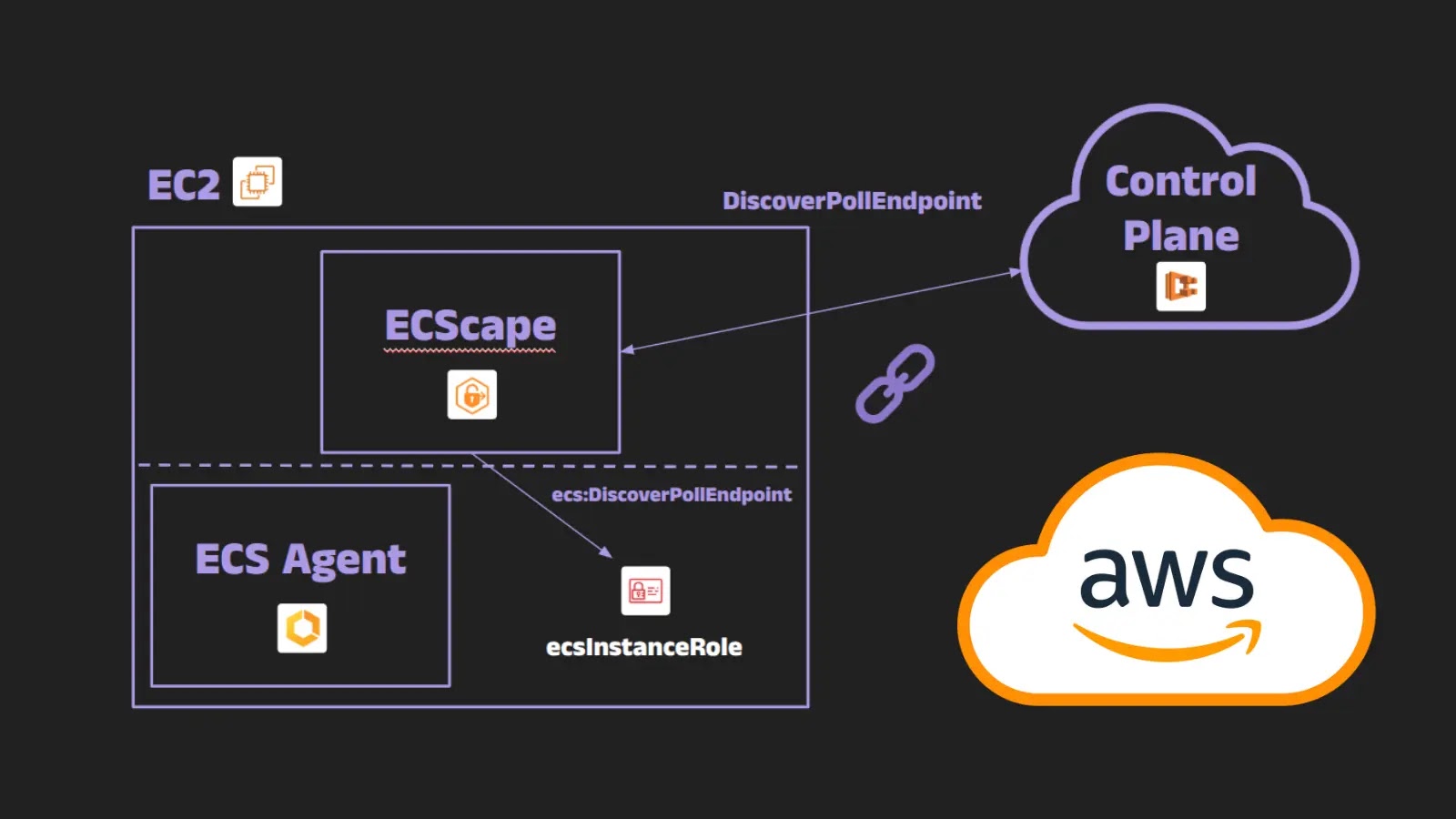
The ECScape technique, uncovered by security researcher Naor [redacted last name for this exercise], targets a specific interaction within ECS deployments running on EC2 instances. In such environments, multiple ECS tasks (containers) can share a single underlying EC2 instance. While theoretically isolated, ECScape demonstrates a pathway for one compromised container to access the AWS IAM and execution role credentials designated for other, legitimate tasks on the same host.
The core of ECScape lies in exploiting the internal communication mechanisms that ECS uses to provide credentials to tasks. When a task starts, ECS temporarily stores its IAM role credentials somewhere on the host. ECScape leverages this to capture credentials intended for other tasks, effectively bypassing traditional container isolation boundaries. This means that if an attacker manages to get a malicious container running on an ECS-managed EC2 instance, they could potentially gain unauthorized access to the AWS resources of other applications and services running alongside it.
The Risk: Impact on Multi-Tenant ECS Deployments
The implications of ECScape are particularly significant for organizations running multi-tenant ECS environments on EC2 instances. In these setups, various applications, services, or even different customers’ workloads might share the same EC2 instances. A breach stemming from ECScape could lead to:
- Lateral Movement: An attacker could move from a low-privilege container to high-privilege workloads or sensitive data stores within the AWS environment.
- Data Exfiltration: Credentials for tasks regularly accessing S3 buckets, databases (RDS), or other storage services become vulnerable, leading to potential data theft.
- Resource Manipulation: Compromised credentials could be used to modify, delete, or create AWS resources, causing significant operational disruption or financial damage.
- Undermined Isolation: The fundamental security premise of task isolation within an EC2 instance is challenged, complicating compliance and risk assessments.
AWS Fargate: A More Secure Alternative
The discovery of ECScape inadvertently highlights the security advantages offered by AWS Fargate. Unlike ECS on EC2, where customers manage the underlying EC2 instances, Fargate provides a serverless compute engine for containers. Crucially, Fargate tasks run within dedicated, isolated micro-VMs. This architecture inherently prevents the cross-task credential exfiltration demonstrated by ECScape, as each task has its own isolated compute environment, eliminating the shared host vulnerability.
- Enhanced Isolation: Fargate’s micro-VM per task model effectively segregates workloads, preventing attacks like ECScape that rely on shared host resources.
- Reduced Operational Overhead: Users no longer need to manage, patch, or secure EC2 instances, offloading a significant portion of security responsibility to AWS.
- Built-in Security: Fargate’s design intrinsically offers a higher degree of isolation and security for containerized applications.
Remediation Actions and Best Practices
While ECScape specifically targets ECS on EC2, its discovery serves as a critical reminder for all cloud users to review and strengthen their security postures. There is no specific CVE number associated with this technique as it exploits a design flaw rather than a software bug. However, the following actions are crucial for mitigating its risks and enhancing overall cloud security:
- Prioritize AWS Fargate for New Deployments: For future containerized applications, seriously consider using AWS Fargate over ECS on EC2, especially for multi-tenant or sensitive workloads.
- Isolate Workloads with Dedicated EC2 Instances: If ECS on EC2 is unavoidable, avoid running tasks with vastly different privilege levels or trust domains on the same EC2 instance. Use separate auto-scaling groups or clusters for different security zones.
- Implement Strongest IAM Least Privilege: Ensure that each ECS task’s IAM role has the absolute minimum permissions required to perform its function. Never grant broad administrative access to tasks. Regularly review and audit IAM policies.
- Network Segmentation: Implement strict network segmentation within your VPC to limit the blast radius of a compromised container. Use Security Groups and Network ACLs to control inbound and outbound traffic.
- Container Image Scanning: Routinely scan all container images for known vulnerabilities using tools like Amazon ECR’s built-in scanning, Clair, or Trivy.
- Runtime Protection and Monitoring: Deploy runtime security solutions that can detect and alert on suspicious activity within containers, such as unexpected process execution or network connections. Integrate with AWS CloudWatch and CloudTrail for comprehensive logging and auditing.
- Regular Security Audits and Penetration Testing: Conduct periodic security assessments and penetration tests of your ECS environments to identify and address potential weaknesses before attackers can exploit them.
Relevant Security Tools
| Tool Name | Purpose | Link |
|---|---|---|
| Amazon ECR Image Scanning | Automated vulnerability scanning for container images stored in ECR. | https://aws.amazon.com/ecr/features/#Image_Vulnerability_Scanning |
| AWS Security Hub | Centralized view of security alerts and automated compliance checks across AWS services. | https://aws.amazon.com/security-hub/ |
| AWS GuardDuty | Intelligent threat detection and continuous monitoring for malicious activity and unauthorized behavior. | https://aws.amazon.com/guardduty/ |
| Trivy | Open-source vulnerability scanner for container images, file systems, and Git repositories. | https://aquasecurity.github.io/trivy/ |
| Clair | Open-source static analysis tool for vulnerabilities in application containers. | https://github.com/quay/clair |
Conclusion
The ECScape technique serves as a stark reminder that even in highly orchestrated cloud environments, fundamental isolation mechanisms can be circumvented if not properly designed or configured. While AWS Fargate offers a more robust security posture against such attacks due to its micro-VM architecture, organizations utilizing ECS on EC2 must diligently apply security best practices. Implementing the principle of least privilege, segmenting workloads, and continuously monitoring for suspicious activity are paramount to protecting sensitive credentials and maintaining the integrity of multi-tenant cloud deployments. Proactive security measures are not just about patching known vulnerabilities; they are about understanding the attack surface and building resilience into the very fabric of your cloud infrastructure.





