Emerging Cyber Threats Featuring QR Codes ClickFix and LOLBins Challenging SOC Defenses
The digital landscape is a constant battleground, and even the most seasoned defenders can find themselves outmaneuvered by novel attack vectors. Recent insights from cybersecurity experts at ANY.RUN reveal a concerning trend: threat actors are increasingly leveraging seemingly innocuous technologies to bypass established Security Operations Center (SOC) defenses. This isn’t about complex zero-days; it’s about cunning social engineering, weaponized everyday tools, and a shift in tactics that demands immediate attention. We’ll dissect these emerging cyber threats, including sophisticated QR code phishing, the deceptively simple ClickFix, and the insidious use of Living Off the Land Binaries (LOLBins), examining how they challenge traditional security paradigms and what your organization can do to safeguard its digital assets.
QR Code Phishing: A Modern Lure
QR codes, once a convenient tool for quick information access, have evolved into a potent phishing vector. Attackers embed malicious links within these scannable squares, often posing as legitimate resources like payment gateways, identity verification pages, or even internal company portals for multi-factor authentication. When an unsuspecting user scans the code, they’re redirected to a spoofed website designed to harvest credentials or install malware. The ease of creation, coupled with the trust users place in scanning familiar codes, makes this a highly effective attack. Traditional email filters and web gateways, designed to scrutinize URL text, often struggle to identify the malicious intent within an image-based QR code, allowing these threats to bypass initial defenses.
For instance, an attacker might distribute flyers containing a malicious QR code disguised as a link to an “urgent software update” or a “new employee benefits portal.” Once scanned, the user is directed to a convincing, yet fake, login page. Submitting credentials on such a page hands control directly to the attacker. This technique exploits user convenience and the difficulty in visually inspecting a QR code’s destination without specialized tools or caution.
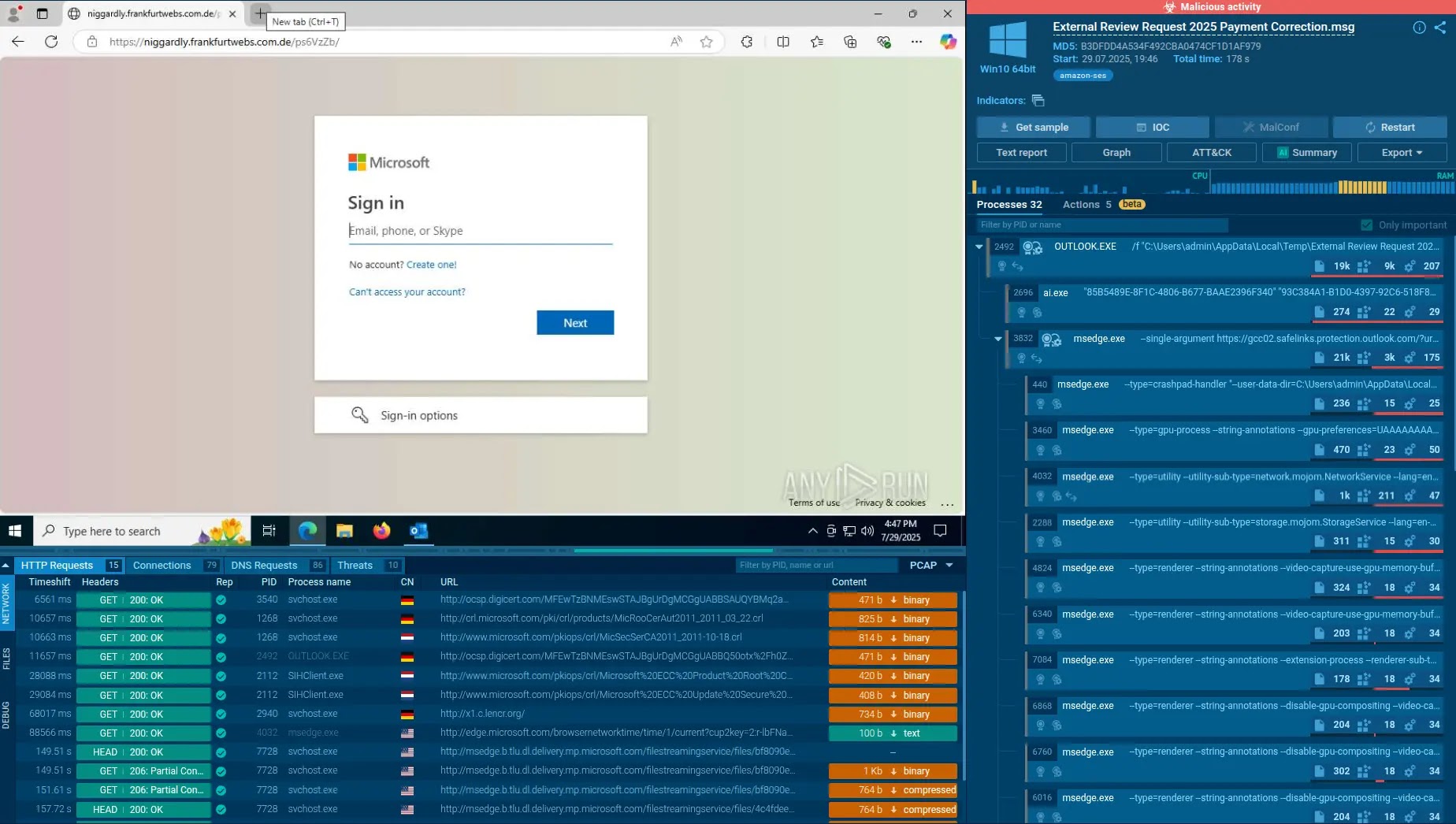
ClickFix Social Engineering: The Illusion of Help
ClickFix, as identified by ANY.RUN, represents a sophisticated social engineering tactic that exploits user trust and the common desire for quick fixes. This attack often involves delivering a malicious payload or facilitating credential theft through a seemingly helpful interaction. Imagine a user encountering an error message on their screen, ostensibly from a system utility or a frequently used application. This message directs them to “click here to fix” the problem, or perhaps to a fake support chat. The “fix” is, of course, the execution of malicious code, the download of malware, or a prompt to enter credentials on a controlled site. The attack preys on human psychology, specifically the instinct to resolve immediate technical issues, making it difficult for users to discern legitimate help from malicious deception.
Attackers often craft these scenarios with high fidelity, mimicking legitimate IT support messages or system alerts, complete with official-looking logos and language. The “fix” offered could be a script execution via PowerShell, leveraging benign system tools for nefarious purposes, a classic example of LOLBins, which we’ll discuss next.
LOLBins: Living Off the Land to Evade Detection
Living Off the Land Binaries (LOLBins) refer to the use of legitimate, pre-installed system tools and scripts within an operating system to carry out malicious activities. Instead of deploying custom malware, which antivirus and endpoint detection and response (EDR) solutions are designed to detect, attackers leverage tools like PowerShell, Command Prompt (cmd.exe), certutil, Bitsadmin, and wmic.exe. This approach makes detection incredibly challenging because the executed processes are inherently trusted by the system and often bypass signature-based and even some behavioral detection mechanisms.
For example, an attacker might use PowerShell to download and execute additional payloads, or certutil.exe to decode a malicious file, or bitsadmin.exe for file transfer. These actions, when performed by legitimate system binaries, can blend seamlessly with normal network and system activity, making it difficult for SOC analysts to distinguish between benign and malicious behavior. Understanding the common usage patterns and deviations for these tools is critical for effective threat hunting.
Remediation Actions for QR Code Phishing, ClickFix, and LOLBins
Defeating these evolving threats requires a multi-layered approach, combining robust technical controls with aggressive security awareness training.
- Enhanced User Awareness Training:
- Educate users about the dangers of unsolicited QR codes, stressing verification before scanning.
- Train employees to be suspicious of “click to fix” prompts, even those appearing to be from legitimate sources. Emphasize reporting unusual requests to IT.
- Implement simulated phishing campaigns that include QR code and social engineering elements.
- Endpoint Detection and Response (EDR) Optimization:
- Configure EDR solutions to monitor for anomalous behavior involving common LOLBins. This includes unusual process trees, outbound connections from system utilities, and atypical command-line arguments.
- Focus on behavioral analysis rather than just signature-based detection for LOLBin activity.
- Network Segmentation and Least Privilege:
- Segment networks to limit the lateral movement of attackers even if an initial compromise occurs.
- Implement the principle of least privilege for all users and applications, restricting the capabilities of LOLBins where possible.
- Implement Secure Browsing and Email Controls:
- Deploy secure web gateways and email security solutions capable of advanced threat protection, including URL rewriting and sandboxing.
- Consider tools that can analyze QR codes in images before rendering them to users.
- Strict Application Whitelisting/Blacklisting:
- For critical systems, consider application whitelisting to prevent unauthorized executables, even LOLBins used maliciously.
- Alternatively, implement strict blacklisting of known malicious command-line parameters for common system utilities.
- Regular Security Audits and Penetration Testing:
- Conduct regular security audits to identify vulnerabilities that could be exploited by these attack vectors.
- Perform penetration tests, including social engineering and LOLBin exploitation scenarios, to validate defenses.
Tools for Detection and Mitigation
| Tool Name | Purpose | Link |
|---|---|---|
| Sysinternals (Process Explorer, Sysmon) | Monitoring and analyzing process activity for LOLBin detection. | https://learn.microsoft.com/en-us/sysinternals/ |
| Elastic Security (SIEM/XDR) | Advanced threat detection, behavioral analytics, and incident response. | https://www.elastic.co/security/ |
| CrowdStrike Falcon Insight XDR | Endpoint protection, threat hunting, and automated response capabilities. | https://www.crowdstrike.com/products/endpoint-security/falcon-insight-xdr/ |
| PhishMe (Cofense T9) | Security awareness training and simulated phishing campaigns for user education. | https://cofense.com/product/cofense-t9/ |
| Proofpoint Email Protection | Email security gateway with advanced threat protection, URL defense, and attachment sandboxing. | https://www.proofpoint.com/us/products/email-protection |
Conclusion: Adapting Defenses for Evolving Threats
The insights from ANY.RUN underscore a critical shift in the threat landscape. Attackers are becoming more adept at exploiting human factors and legitimate system functionalities to bypass security controls. QR code phishing, the ClickFix social engineering tactic, and the widespread use of LOLBins represent a significant challenge to traditional SOC defenses. Effective cybersecurity in this environment necessitates a proactive, adaptive strategy. Organizations must prioritize continuous security awareness training, refine their EDR and SIEM solutions for behavioral anomaly detection, and implement stringent access controls. The battle against cyber threats is ongoing; staying ahead requires vigilance, an understanding of adversary tactics, and the readiness to adapt security postures continually.





