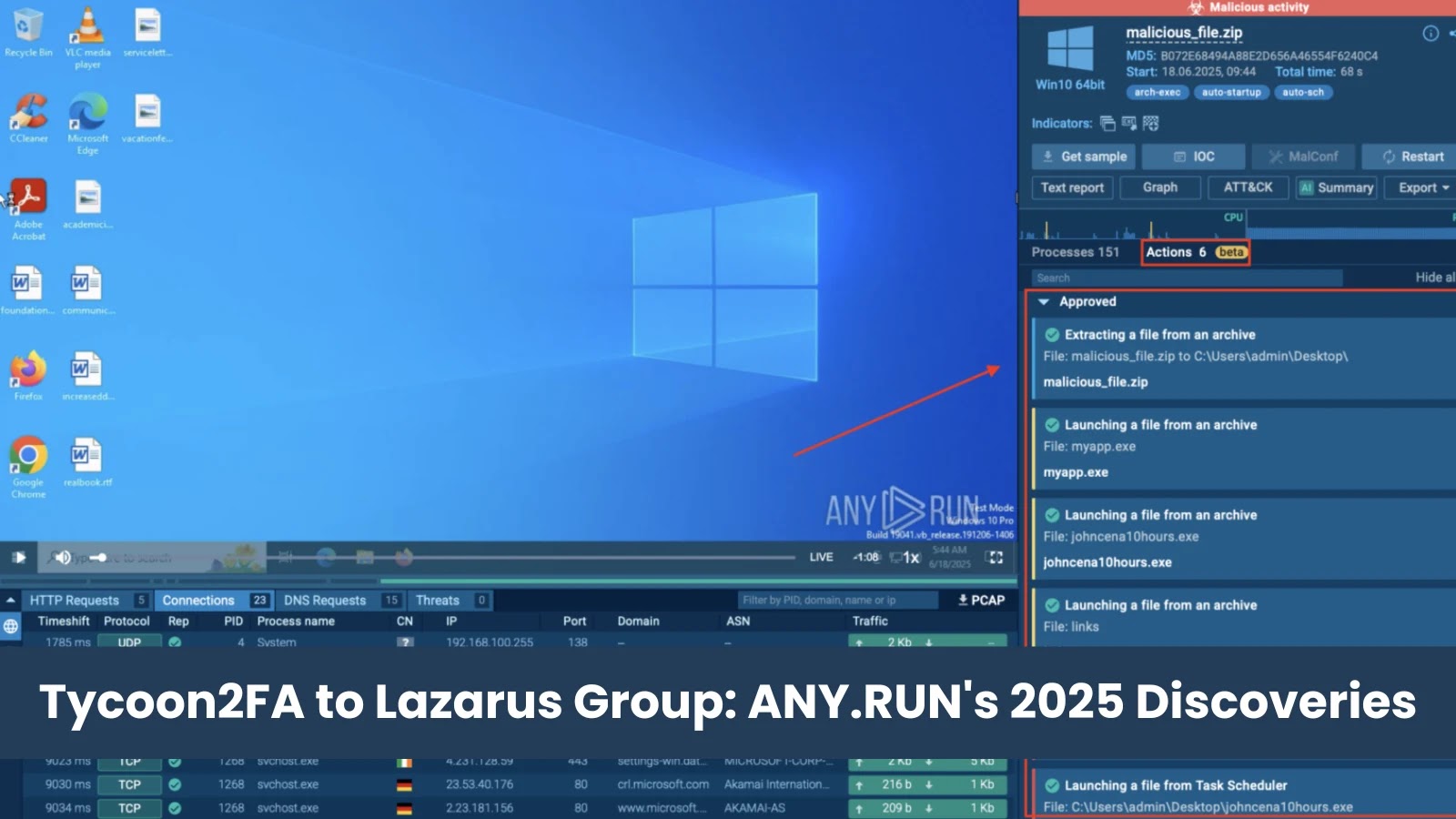
From Tycoon2FA to Lazarus Group – Inside ANY.RUN’s Biggest Discoveries of 2025
Unveiling 2025’s Cyber Landscape: ANY.RUN’s Definitive Impact
The digital realm is a constant battleground, where new threats emerge with alarming speed. For cybersecurity professionals, staying ahead means leveraging powerful tools and collective intelligence. This past year, ANY.RUN, a leading interactive malware analysis platform, significantly amplified that collective intelligence. Their 2025 annual report isn’t just a recap of impressive growth; it’s a testament to the global community’s relentless efforts to dissect and understand the evolving threat landscape.
With its user base dedicating over 400,000 hours to threat analysis – a staggering equivalent of more than 45 years of continuous research – ANY.RUN has become an indispensable resource. Processing 5.7 million analyses across 195 countries, their platform has provided unparalleled visibility into emerging malware campaigns and sophisticated APT groups. Let’s delve into some of the most critical discoveries and insights from ANY.RUN’s 2025 contributions, from the intricate workings of Tycoon2FA to the persistent threat posed by the Lazarus Group.
Tycoon2FA: A New Dimension of Phishing Attacks
Tycoon2FA represents a worrying evolution in phishing tactics. This sophisticated threat specifically targets multi-factor authentication (MFA) mechanisms, which are often considered the last line of defense against account compromise. Unlike traditional phishing that merely steals credentials, Tycoon2FA aims to bypass MFA entirely, granting attackers direct access to sensitive accounts.
ANY.RUN’s analysis of Tycoon2FA samples revealed its reliance on adversary-in-the-middle (AiTM) techniques. Attackers set up a proxy between the victim and the legitimate service, intercepting both initial login credentials and the subsequent MFA token. This allows them to effectively “man-in-the-middle” the authentication process, often without the user’s immediate awareness. The discovery of such specific campaigns highlights the need for organizations to move beyond relying solely on traditional MFA and consider more robust, phishing-resistant alternatives.
Remediation Actions for Tycoon2FA
- Implement FIDO2/WebAuthn: Transition to phishing-resistant MFA methods like FIDO2 security keys or WebAuthn, which cryptographically link authentication to the origin website, making AiTM attacks ineffective.
- Educate Users on AiTM Phishing: Train employees to recognize the subtle indicators of AiTM attacks, such as unusual URL redirection or slight delays in login processes.
- Monitor Authentication Logs: Implement robust logging and monitoring for authentication attempts, looking for anomalies like multiple successful logins from different geolocations in a short timeframe.
- Device Trust Policies: Utilize endpoint security solutions that incorporate device trust, ensuring only authorized and healthy devices can access sensitive resources, even if MFA is compromised.
Lazarus Group’s Enduring Threat Landscape
The infamous Lazarus Group, originating from North Korea, continued its prolific activity throughout 2025, with ANY.RUN playing a crucial role in tracking their evolving toolset and tactics. Known for their blend of cyber espionage, sabotage, and financially motivated operations, Lazarus Group remains a top-tier threat to critical infrastructure and financial institutions globally.
ANY.RUN’s platform identified new variants of their established malware families, such as the remote access trojan (RAT) AppleJeus (targeting cryptocurrency exchanges) and updated versions of their custom backdoors often associated with supply chain attacks. The analysis showcased their persistent efforts to refine evasion techniques and expand their reach, particularly into sectors vital for economic stability. While specific CVEs linked directly to generalized Lazarus Group activity are broad, their exploits often leverage known vulnerabilities. For instance, their past campaigns have sometimes exploited vulnerabilities like CVE-2017-0199 (Microsoft Office/WordPad Remote Code Execution) or even more recent ones depending on their current targeting.
Other Noteworthy Discoveries and Trends
Beyond specific threat groups, ANY.RUN’s 2025 data revealed broader trends in the malware ecosystem:
- Increased Obfuscation and Evasion: Malware authors are investing more heavily in advanced obfuscation techniques, polymorphic code, and anti-analysis measures to evade detection by traditional security solutions and sandboxes.
- Rise of Ransomware-as-a-Service (RaaS): The RaaS model continued its dominance, lowering the barrier to entry for aspiring cybercriminals and leading to a proliferation of ransomware variants.
- Supply Chain Attacks: Attacks targeting software supply chains remained a critical concern, with several high-profile incidents underscoring the vulnerability of trusted software components.
- Cloud-Native Malware: A growing focus on developing malware specifically designed to exploit misconfigurations and vulnerabilities within cloud environments was observed, indicating a shift in attacker priorities.
The Power of Collaborative Threat Intelligence
ANY.RUN’s 2025 achievements underscore the undeniable value of interactive, community-driven threat intelligence. By enabling security researchers and analysts worldwide to collectively analyze, report, and share insights on millions of malware samples, the platform creates a robust defense mechanism. This collective effort not only accelerates detection and analysis but also fosters a deeper understanding of adversary tactics, techniques, and procedures (TTPs).
The ability to interact with malware samples in a secure, sandbox environment allows for dynamic behavioral analysis, revealing runtime characteristics and communication patterns that static analysis might miss. This interactive approach is instrumental in dissecting complex threats like Tycoon2FA or understanding the nuanced behaviors of state-sponsored groups like Lazarus.
Leveraging Tools for Enhanced Detection and Mitigation
Effective defense against the threats identified by platforms like ANY.RUN requires a layered security approach and the utilization of appropriate tools. Here’s a table of categories and representative tools that can aid in detection, analysis, and mitigation:
| Tool Category | Purpose | Key Features/Examples |
|---|---|---|
| Interactive Malware Analysis Sandboxes | Dynamic analysis of suspicious files and URLs, behavioral insights. | ANY.RUN, VirusTotal (sandbox integration), Palo Alto Networks WildFire |
| Endpoint Detection and Response (EDR) | Real-time monitoring, detection, and response to threats on endpoints. | CrowdStrike Falcon, Carbon Black, Microsoft Defender for Endpoint |
| Security Information and Event Management (SIEM) | Centralized logging, correlation, and analysis of security events. | Splunk Enterprise Security, QRadar, Elastic SIEM |
| Threat Intelligence Platforms (TIP) | Aggregating, processing, and sharing threat intelligence. | MISP (Malware Information Sharing Platform), Anomali ThreatStream |
| Multi-Factor Authentication (MFA) Solutions | Enhancing account security beyond passwords. | Duo Security, Okta, YubiKey (FIDO2/WebAuthn hardware tokens) |
Insights Moving Forward: The Essential Role of Proactive Security
ANY.RUN’s 2025 report serves as a critical benchmark, highlighting both the persistent and emerging challenges in cybersecurity. The sheer volume of analyses and the depth of discoveries underline the essential role of proactive security measures and collaborative intelligence sharing. Organizations must continuously adapt their defenses, embracing phishing-resistant authentication, investing in advanced threat detection, and fostering a security-aware culture. The fight against sophisticated adversaries like the Lazarus Group and evolving threats like Tycoon2FA demands a dynamic, informed, and collective response from the entire cybersecurity community.





