GLOBAL GROUP RaaS Operators Enable AI-powered Negotiation Functionality
The landscape of cyber threats continues its relentless evolution, and a formidable new contender has emerged: GLOBAL GROUP, a sophisticated Ransomware-as-a-Service (RaaS) operation. This isn’t just another ransomware group; GLOBAL GROUP distinguishes itself with cutting-edge AI-powered negotiation capabilities and advanced mobile management features. Their targeted campaign impact across critical sectors like healthcare, automotive, and industrial underscores a significant escalation in ransomware tactics.
GLOBAL GROUP: A New Era of RaaS Sophistication
Since its launch in June 2025, GLOBAL GROUP, operated by the ominous threat actor known as “$$$”, has rapidly expanded its nefarious footprint. Within a remarkably short period, they have claimed 17 victims across multiple countries. This aggressive scaling is attributed to their highly automated systems and strategic partnerships, allowing them to penetrate and exploit organizations with alarming efficiency.
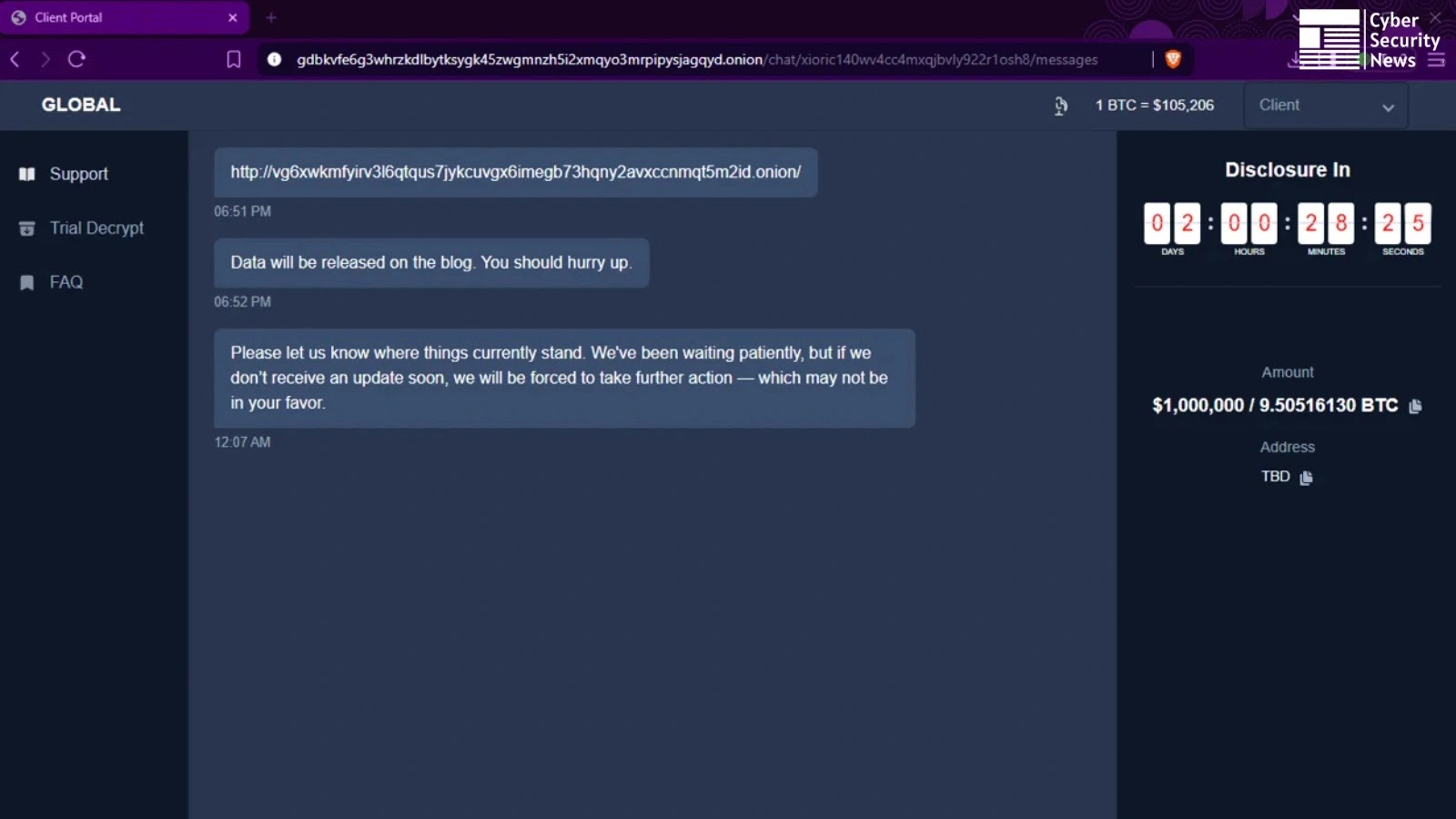
The core innovation propelling GLOBAL GROUP’s success is its integration of AI-powered negotiation functionality. Traditionally, ransomware negotiation has been a labor-intensive process, often involving human interaction, which is prone to inconsistencies and delays. By leveraging Artificial Intelligence, GLOBAL GROUP can automate and optimize the negotiation phase, potentially leading to faster and more successful extortion attempts. This AI integration likely enables dynamic pricing, real-time demand adjustments, and potentially even psychologically engineered negotiation tactics, making it significantly harder for victims to counter.
Furthermore, the mention of mobile management features suggests an advanced operational infrastructure. This could imply a capability for threat actors to manage their ransomware campaigns, victims, and even cryptocurrency transactions directly from mobile devices, enhancing their stealth, flexibility, and global reach. It speaks to a level of operational maturity rarely seen in emerging RaaS groups.
Targeted Sectors and Operational Impact
GLOBAL GROUP’s current victimology paints a clear picture of their strategic intent. By focusing on healthcare, automotive, and industrial sectors, they are targeting industries that are not only rich in valuable data but also highly sensitive to operational disruption. A successful ransomware attack on these sectors can have cascading effects, impacting critical infrastructure, patient care, supply chains, and manufacturing capabilities.
- Healthcare: Highly sensitive patient data, critical operational technology (OT) reliance, and the immediate impact on human lives make healthcare organizations prime targets. Downtime or data breaches can lead to patient safety issues and severe reputational damage.
- Automotive: Modern automotive manufacturing relies heavily on interconnected IT and OT systems. Disruptions can halt production lines, impacting global supply chains and causing significant financial losses.
- Industrial: Industrial control systems (ICS) and operational technology environments are increasingly interconnected with IT networks. Ransomware attacks here can compromise critical infrastructure, machinery, and production, posing risks to safety and economic stability.
The rapid operational scaling and use of automated systems highlight a clear trend: threat actors are investing heavily in enhancing their efficiency and reach. The ability to quickly onboard and manage victims, coupled with strategic partnerships (likely with initial access brokers or other cybercriminal syndicates), allows GLOBAL GROUP to operate as a well-oiled, financially motivated machine.
Remediation Actions and Protective Measures
Countering sophisticated RaaS operations like GLOBAL GROUP requires a multi-layered, proactive cybersecurity strategy. Organizations must prioritize robust defenses to prevent initial access, limit lateral movement, and swiftly detect and respond to threats.
- Implement Strong Access Controls: Enforce Multi-Factor Authentication (MFA) for all services, especially for remote access, VPNs, and critical systems. Implement the principle of least privilege.
- Regular Backups and Disaster Recovery: Maintain immutable, off-site, and offline backups of all critical data. Regularly test backup restoration procedures to ensure business continuity in the event of a successful attack.
- Network Segmentation: Isolate critical operational technology (OT) and sensitive data networks from broader corporate IT networks. This minimizes the blast radius of any breach.
- Endpoint Detection and Response (EDR) / Extended Detection and Response (XDR): Deploy advanced EDR/XDR solutions across all endpoints to detect and respond to suspicious activities, including known ransomware behaviors.
- Vulnerability Management and Patching: Regularly scan for vulnerabilities and apply security patches promptly. Many ransomware attacks exploit known, unpatched vulnerabilities.
- Email and Web Security: Implement robust email filtering to block phishing attempts, and web security gateways to prevent access to malicious websites. End-user awareness training for phishing remains critical.
- Incident Response Plan: Develop and regularly rehearse a comprehensive incident response plan. This includes clear roles, responsibilities, communication protocols, and steps for containment, eradication, and recovery.
- Security Awareness Training: Educate employees about common social engineering tactics, the dangers of suspicious links and attachments, and the importance of reporting anomalies.
- Threat Intelligence Integration: Stay updated with the latest threat intelligence regarding new RaaS groups, their tactics, techniques, and procedures (TTPs), and indicators of compromise (IoCs).
- External Security Audits: Periodically engage third-party security experts to conduct penetration testing and security audits to identify weaknesses before attackers do.
Conclusion
GLOBAL GROUP’s emergence, with its AI-powered negotiation and mobile management capabilities, marks a concerning leap in ransomware sophistication. Their rapid ascension and strategic targeting of critical sectors demand immediate attention from cybersecurity professionals and organizational leadership alike. The threat actor “$$$” has demonstrated an alarming ability to automate and scale operations, placing immense pressure on potential victims. Proactive and comprehensive cybersecurity measures are no longer optional but essential for resilience against these advanced RaaS threats.





