Google Drive Desktop for Windows Vulnerability Grants Full Access to Another User’s Drive
Navigating the Threat Landscape: Unpacking the Google Drive Desktop Vulnerability
In our increasingly interconnected professional lives, cloud storage solutions like Google Drive have become indispensable. They offer unparalleled convenience for collaboration and data accessibility. However, this convenience often comes with inherent security risks, especially when vulnerabilities emerge in the very applications we rely upon. A significant security flaw has recently been identified in the Google Drive Desktop application for Windows, posing a serious threat to data privacy and integrity on shared systems. This vulnerability allows an unauthorized user to gain full access to another user’s Google Drive files without requiring any credentials, highlighting a critical lapse in access control mechanisms.
Understanding the Google Drive Desktop Vulnerability
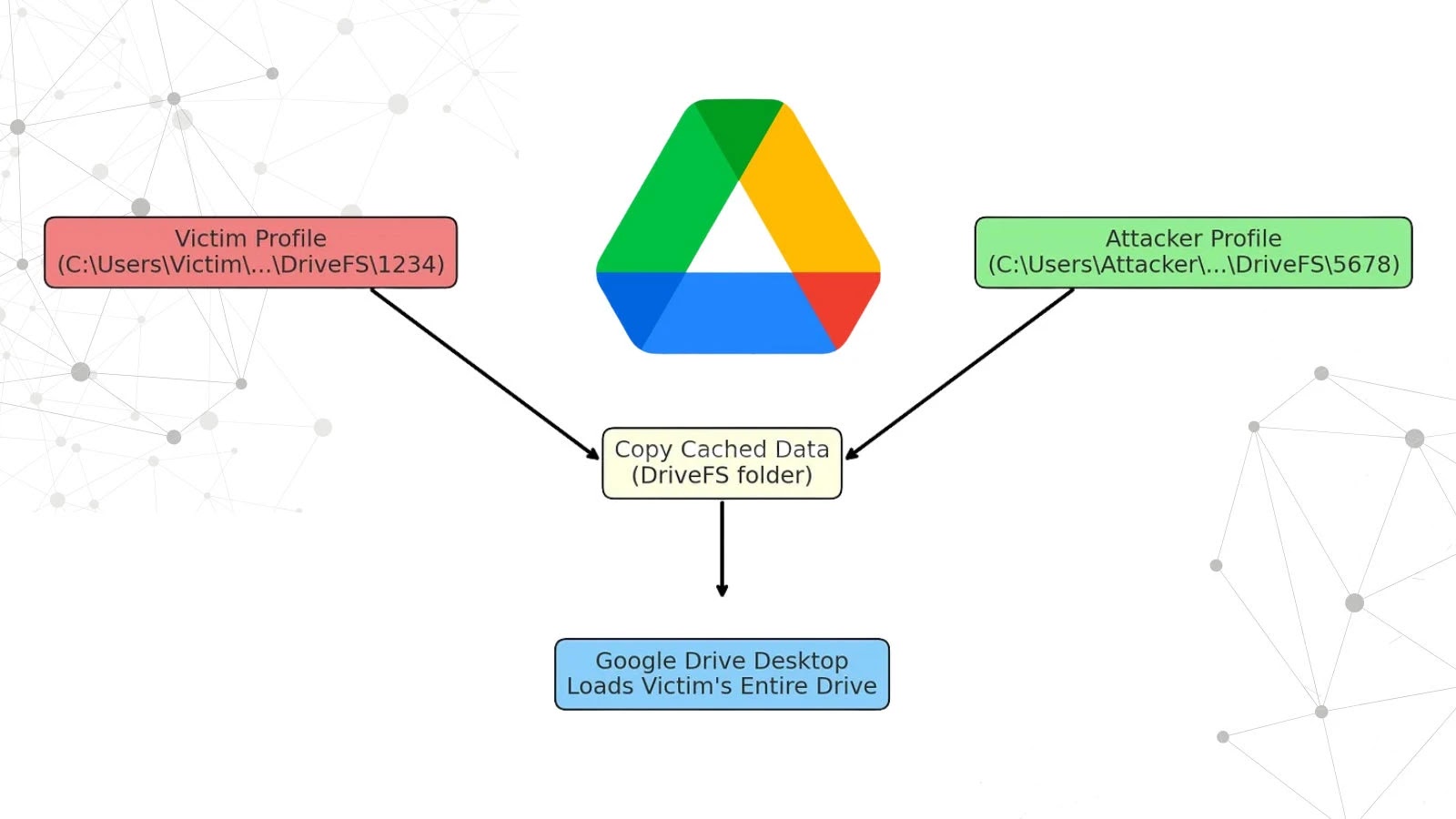
The core of this critical vulnerability lies within the Google Drive Desktop application for Windows, specifically in its handling of cached data and access control. When multiple users share a Windows machine and each utilizes the Google Drive Desktop application, a design flaw or “broken access control” mechanism allows one logged-in user to bypass the intended security boundaries and access the entire Google Drive contents of another user on the same system. This means sensitive documents, private files, and confidential information belonging to User A could be fully exposed to User B, simply because User B is logged into the same machine. No password, no two-factor authentication, no authorization prompts – just complete, unauthorized access.
This issue has been formally recognized as CVE-2023-3004. The vulnerability’s severity stems from the fact that it exploits a trust relationship within the operating system environment itself, rather than a network-based attack. It’s a localized threat that can have broad implications for data security in multi-user environments such as corporate workstations, educational institutions, or even shared family computers. The potential for data exfiltration, modification, or even deletion is considerable, underscoring the urgency of remediation.
Impact of Compromised Access on Shared Endpoints
The ramifications of this Google Drive Desktop vulnerability are substantial, particularly for organizations and individuals utilizing shared Windows machines:
- Data Confidentiality Breach: The most immediate and apparent impact is the direct compromise of sensitive data. Business documents, personal records, financial information, and intellectual property stored in Google Drive become openly accessible to anyone with a local login to the affected machine.
- Increased Insider Threat Risk: The vulnerability significantly amplifies the insider threat. Malicious or even curious individuals within an organization or household can exploit this flaw to snoop on, copy, or tamper with others’ data without leaving a clear digital footprint of unauthorized access.
- Compliance and Regulatory Penalties: For businesses, a data breach stemming from this vulnerability could lead to severe non-compliance penalties under regulations like GDPR, HIPAA, or CCPA, alongside significant reputational damage.
- Data Integrity Concerns: Beyond just viewing, an attacker could potentially modify or delete files, leading to data corruption, operational disruptions, and loss of critical information.
- Expanded Attack Surface: While this vulnerability is local, the compromised Google Drive account could potentially be used as a pivot point for further attacks, such as phishing campaigns targeting the user’s contacts or gaining access to other connected services.
Remediation Actions and Best Practices
Addressing the Google Drive Desktop vulnerability requires immediate action and the adoption of robust security practices. While Google has released updates addressing this specific flaw, users and IT administrators must be proactive.
Immediate Steps:
- Update Google Drive Desktop: Ensure that all instances of the Google Drive Desktop application on Windows are updated to the latest version. This is the most critical step, as Google has patched CVE-2023-3004. Always enable automatic updates if possible.
- Review Shared Machine Practices: Assess whether shared Windows machines are truly necessary for highly sensitive work. If so, implement stricter user isolation policies.
- Educate Users: Inform users about the risks of storing highly sensitive data in local synced folders if sharing a machine. Emphasize the importance of updating all software.
Long-Term Security Best Practices:
- Principle of Least Privilege: Ensure that users only have the minimum necessary access rights on shared systems. Avoid granting administrative privileges unnecessarily.
- Dedicated Workstations: For highly sensitive roles or data, consider using dedicated, non-shared workstations. This limits the exposure to localized vulnerabilities.
- Endpoint Detection and Response (EDR): Utilize EDR solutions to monitor for suspicious activities on endpoints, including unauthorized file access or anomalous process behavior.
- Regular Security Audits: Conduct periodic security audits of your workstation configurations and user access controls to identify and remediate potential vulnerabilities.
- Multi-Factor Authentication (MFA): While MFA wouldn’t directly prevent this local exploit, it remains a critical layer of defense for Google accounts to prevent remote unauthorized access if credentials were somehow compromised.
- Strong Access Controls for Local Data: Encourage users to encrypt sensitive local folders or use strong user account passwords on their Windows machines, even if they perceive the machine as “private.”
Tools for Detection and Mitigation
Effective management of endpoint security requires appropriate tools for monitoring, detection, and remediation. Here’s a table of categories and examples:
| Tool Category | Purpose | Example Tools/Methods |
|---|---|---|
| Endpoint Detection & Response (EDR) | Real-time monitoring of endpoints for suspicious activity, including file access, process execution, and network connections. Essential for identifying anomalous behavior. | CrowdStrike Falcon, Microsoft Defender for Endpoint, SentinelOne |
| Vulnerability Management Platforms | Scanning systems for known vulnerabilities, providing patching recommendations, and tracking compliance with security policies. | Tenable.io, Qualys, Rapid7 InsightVM |
| Configuration Management Tools | Ensuring consistent and secure configuration of all endpoints, including proper permissions and software versions. | Microsoft Intune, SCCM, Group Policy Objects (GPO) |
| File Integrity Monitoring (FIM) | Monitoring critical files and directories for unauthorized changes, which could indicate a compromise. | OSSEC (Open Source), Tripwire, SolarWinds Security Event Manager |
| Security Information and Event Management (SIEM) | Collecting and analyzing security logs from various sources to detect security incidents and provide centralized visibility. | Splunk, IBM QRadar, Elastic SIEM |
Conclusion: Prioritizing Endpoint Security in Shared Environments
The Google Drive Desktop vulnerability, CVE-2023-3004, serves as a stark reminder that security extends beyond network perimeters to the very endpoints where data is accessed and processed. The ease with which one user on a shared Windows machine could gain complete, unauthorized access to another’s Google Drive highlights critical weaknesses in local access control and cached data handling. Proactive patching of applications, stringent user access management, and the deployment of robust endpoint security solutions are not merely best practices but essential fortifications in today’s threat landscape. Prioritizing endpoint security, especially in multi-user environments, is paramount to safeguarding sensitive data and maintaining the trust in cloud-based services.





