“GPUGate” Malware Abuses Google Ads and GitHub to Deliver Advanced Malware Payload
Unmasking GPUGate: A Deceptive New Malware Campaign Exploiting Google Ads and GitHub
The digital landscape is a constant battleground, with threat actors continuously refining their tactics to breach defenses and compromise systems. A recent and particularly insidious campaign, dubbed “GPUGate,” has emerged, showcasing a novel approach to malware delivery by cleverly abusing trusted platforms like Google Ads and GitHub. This advanced persistent threat leverages a unique technique to evade traditional security analysis, posing a significant challenge for cybersecurity professionals.
As expert cybersecurity analysts, understanding the nuances of such sophisticated attacks is paramount. GPUGate represents a significant evolution in malware delivery, highlighting the need for enhanced vigilance and proactive defense strategies.
The Anatomy of Deception: How GPUGate Operates
The “GPUGate” campaign, as identified by the Arctic Wolf Cybersecurity Operations Center, employs a multi-pronged attack chain designed for maximum stealth and effectiveness. It begins with a deceptively simple, yet highly effective, social engineering ploy.
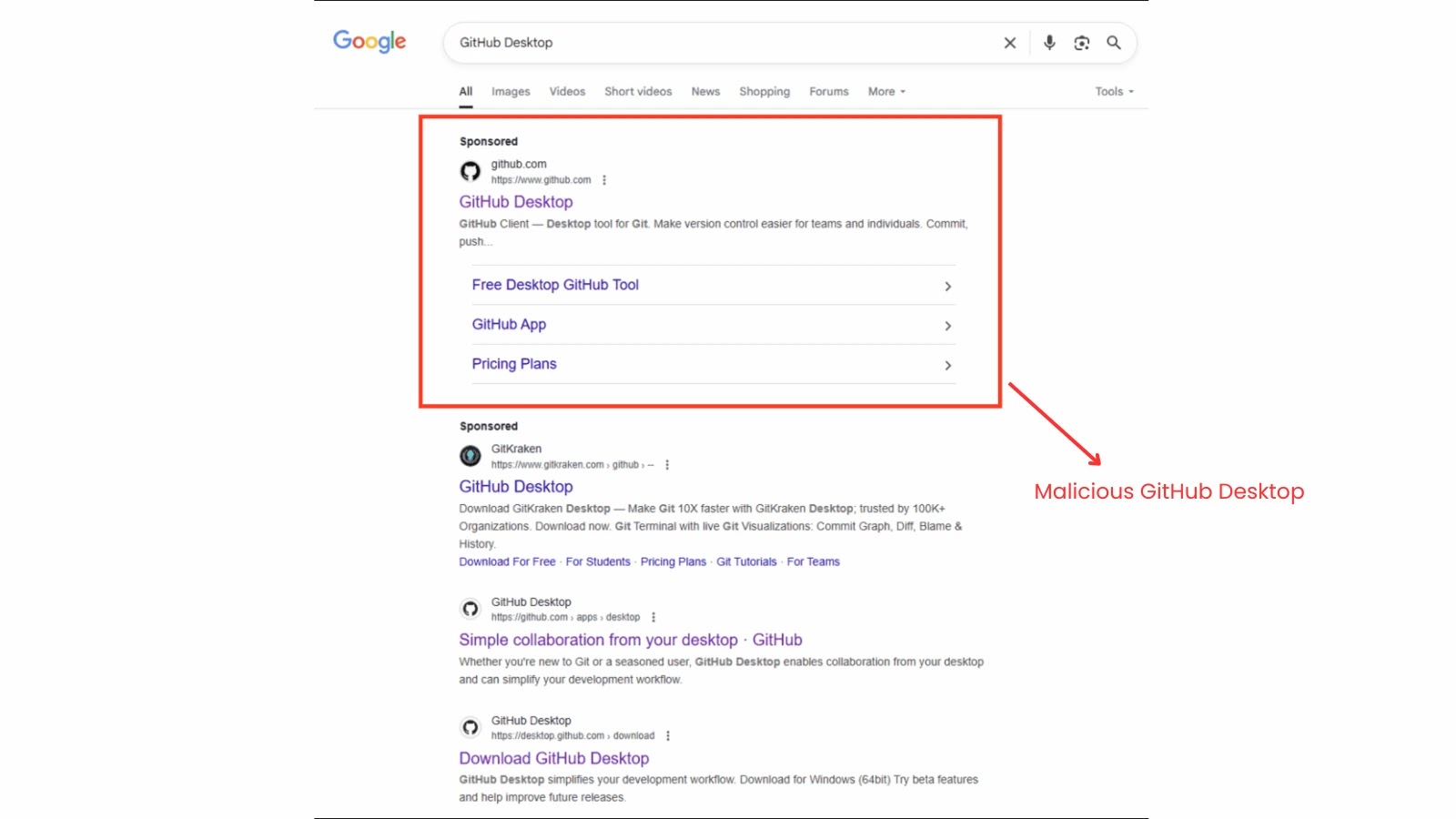
- Google Ads Lure: The initial vector involves sponsored advertisements on Google Ads. These ads are crafted to mimic legitimate software or tool downloads, often appearing at the top of search results for popular utilities or applications. Users, trusting the prevalence and apparent legitimacy of Google’s advertising platform, are tricked into clicking these malicious links.
- GitHub as a Malicious Host: Upon clicking the Google Ad, users are redirected to what appears to be a legitimate GitHub repository. However, this repository is controlled by the threat actors and contains the malicious payload disguised as a legitimate software installer or update. The use of GitHub provides a veneer of legitimacy and leverages the platform’s trusted reputation.
- GPU-Powered Evasion: The truly innovative aspect of GPUGate lies in its ability to evade security analysis. The malware incorporates a technique that leverages the victim’s Graphics Processing Unit (GPU) for malicious activities or to obscure its true nature. This novel approach allows the malware to bypass traditional CPU-centric sandboxing and analysis tools, making detection considerably more difficult. While specific details on how the GPU is utilized for evasion are still emerging, it points to a significant step forward in obfuscation techniques.
- Payload Delivery: The ultimate goal of GPUGate is to deliver an advanced malware payload. While the precise nature of the final payload can vary, it is designed to establish persistence, exfiltrate sensitive data, or set the stage for further compromise. Reports suggest the campaign originates from a Russian-speaking threat group, indicating a sophisticated and well-resourced operation.
Why GPUGate Poses a Significant Threat
The GPUGate campaign is not just another malware variant; it represents a concerning advancement in cyberattack methodologies due to several factors:
- Abuse of Trusted Platforms: Leveraging Google Ads and GitHub, platforms widely used and trusted by millions, grants the campaign an immediate layer of perceived legitimacy, making it difficult for users to discern malicious intent.
- Novel Evasion Techniques: The use of GPU-based evasion introduces a new challenge for traditional security tools. Many sandboxing and analysis environments primarily focus on CPU activity, making the GPU-centric approach a potentially effective circumventor.
- Sophisticated Social Engineering: The initial lure via Google Ads is highly effective, preying on user trust in search engine results and the urgency to find specific software.
Remediation Actions and Proactive Defenses
Addressing the threat posed by GPUGate requires a multi-layered approach, combining technological safeguards with heightened user awareness:
- Enhanced User Awareness Training: Educate users about the dangers of clicking on sponsored ads, even from reputable search engines. Emphasize verifying download sources directly from official vendor websites, not through third-party links or search results.
- Robust Endpoint Detection and Response (EDR): Implement and continuously monitor EDR solutions capable of detecting unusual process behavior, even those exploiting GPUs. Look for anomalous network connections and file modifications.
- Network Traffic Analysis (NTA): Utilize NTA tools to identify suspicious outbound connections from internal systems that might indicate communication with command-and-control servers.
- Web Content Filtering and DNS Filtering: Block access to known malicious domains and categorize suspicious websites, preventing users from reaching the initial GitHub repositories.
- Email Security Gateway (ESG): Although the primary vector is Google Ads, ensure robust email security to block any potential follow-up phishing attempts or credential harvesting.
- Regular Security Audits and Penetration Testing: Proactively identify vulnerabilities in your infrastructure and applications that could be exploited by such sophisticated campaigns.
- Stay Updated with Threat Intelligence: Continuously integrate and act upon the latest threat intelligence regarding new malware variants, attack methodologies, and indicators of compromise (IoCs).
Essential Tools for Detection and Mitigation
Deploying and configuring the right security tools is crucial in the fight against advanced malware like GPUGate.
| Tool Name | Purpose | Link |
|---|---|---|
| Endpoint Detection and Response (EDR) Solutions | Detect and respond to suspicious activity on endpoints, including process injection and anomalous GPU usage. | Gartner Peer Insights (EDR) |
| Network Traffic Analysis (NTA) Platforms | Monitor network traffic for malicious C2 communication, data exfiltration, or unusual patterns. | ExtraHop (Example NTA) |
| Threat Intelligence Platforms (TIPs) | Aggregate and disseminate real-time threat intelligence, including IoCs associated with new campaigns. | MITRE ATT&CK CTI Resources |
| Web Application Firewalls (WAFs) | Protect web applications from common attacks, even if not the primary vector, good general defense. | OWASP ModSecurity |
| Secure Web Gateway (SWG) / DNS Filter | Block access to known malicious domains and categories of websites. | Zscaler (Example SWG) |
Conclusion: Adapting to the Evolving Threat Landscape
The “GPUGate” malware campaign underscores a critical shift in the threat landscape: attackers are increasingly sophisticated, leveraging trusted platforms and novel evasion techniques to achieve their objectives. The abuse of Google Ads for initial compromise and GitHub for payload hosting, coupled with innovative GPU-based obfuscation, highlights the need for continuous adaptation in cybersecurity defenses.
For IT professionals, security analysts, and developers, the key takeaways are clear: prioritize robust user education, invest in advanced threat detection capabilities, and remain agile in response to emerging threats. Proactive monitoring, comprehensive tooling, and a deep understanding of evolving attack methodologies are essential to protect organizational assets against campaigns as cunning as GPUGate.





