Hackers Abuse Microsoft Teams to Gain Remote Access With PowerShell-based Malware
The Silent Threat: How Cybercriminals Are Weaponizing Microsoft Teams for Remote Access
In the evolving landscape of cyber threats, attackers constantly adapt their methodologies to exploit trusted platforms and human vulnerabilities. A recent alarming trend reveals cybercriminals are increasingly weaponizing Microsoft Teams, exploiting its integral role in corporate communications to gain unauthorized remote access and deploy sophisticated malware. This marks a dangerous escalation from traditional email-based phishing attacks, demanding immediate attention from IT professionals and security analysts.
The Evolution of Social Engineering: Teams-Based Phishing
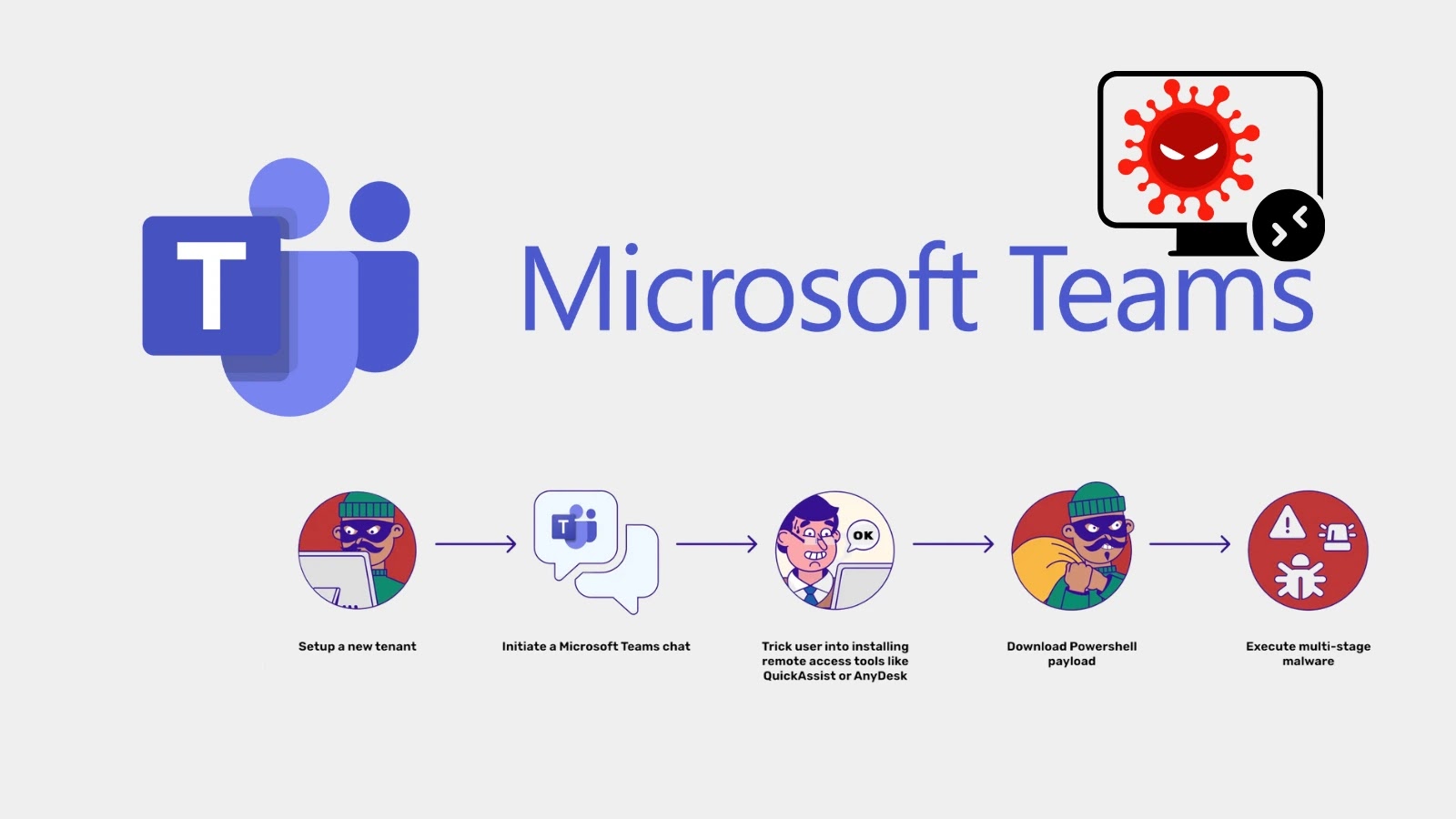
Cybercriminals are leveraging an insidious form of social engineering within Microsoft Teams. Instead of relying on email, threat actors are impersonating IT support staff directly within Teams chats. This approach significantly increases their chances of success, as employees often perceive internal communications as inherently trustworthy. The goal is simple: trick employees into granting remote access to their systems, effectively bypassing established security perimeters.
PowerShell-Based Malware: The Weapon of Choice
Once remote access is established, attackers are deploying PowerShell-based malware. PowerShell, a powerful command-line shell and scripting language, is a built-in component of Windows operating systems. Its legitimate administrative capabilities make it an attractive tool for malicious actors, as its usage can often blend in with normal system activities, making detection challenging. This method allows for the execution of arbitrary code, data exfiltration, and the establishment of persistent backdoors, granting attackers long-term control over compromised systems.
Key Tactics Employed by Threat Actors
- Impersonation: Attackers create fake user profiles within Teams, often with names and profile pictures designed to mimic legitimate IT support personnel.
- Urgency and Pressure: Conversations are typically crafted to instill a sense of urgency, pressuring victims to comply quickly to resolve a supposed “critical issue.”
- Remote Access Tools: Victims are coaxed into installing legitimate remote access software, or unwittingly running scripts that grant attackers control, under the guise of “troubleshooting.”
- Malware Delivery: PowerShell scripts are then executed to download and install various types of malware, including info-stealers, ransomware, or remote access Trojans (RATs).
- Lateral Movement: Once a foothold is established, attackers attempt to move laterally within the network to discover and compromise additional high-value targets.
Remediation Actions and Proactive Defenses
Organizations must adopt a multi-layered approach to mitigate the risks posed by these sophisticated Teams-based attacks. Proactive measures and robust employee training are paramount.
- Implement Strong Authentication: Enforce Multi-Factor Authentication (MFA) for all Microsoft Teams accounts. This adds a critical layer of security even if credentials are compromised.
- Employee Security Awareness Training: Conduct regular, up-to-date training specifically on recognizing social engineering tactics within collaboration platforms like Teams. Emphasize verification procedures for unexpected IT requests.
- Principle of Least Privilege: Ensure users only have the necessary permissions to perform their job functions. Restrict administrative rights.
- Endpoint Detection and Response (EDR): Deploy EDR solutions to monitor endpoints for suspicious activities, including unusual PowerShell script executions and unauthorized remote access attempts.
- Network Segmentation: Segment your network to limit lateral movement in case of a breach on an endpoint.
- Behavioral Analytics: Utilize tools that monitor user behavior for anomalies, such as an IT support account accessing unusual systems or performing non-standard actions.
- Conditional Access Policies: Configure Microsoft 365 Conditional Access policies to restrict access based on device compliance, location, or network.
- Review and Audit Logs: Regularly audit Microsoft Teams activity logs, Azure AD sign-in logs, and endpoint logs for suspicious patterns.
Tools for Detection and Mitigation
| Tool Name | Purpose | Link |
|---|---|---|
| Microsoft 365 Defender | Comprehensive threat protection, EDR, and email/collaboration security. | Microsoft 365 Defender |
| PowerShell Script Block Logging | Logs detailed information about PowerShell script executions, aiding in detection of malicious activity. | Script Block Logging |
| Azure Active Directory Conditional Access | Enforces fine-grained access controls based on user, device, and location context. | Azure AD Conditional Access |
| Endpoint Protection Platforms (EPP) | Preventative security against known malware and suspicious behaviors on endpoints. | (Vendor Specific – e.g., CrowdStrike, SentinelOne) |
Conclusion
The weaponization of Microsoft Teams for remote access and malware distribution represents a significant evolution in cyberattack methodologies. Organizations must recognize the heightened risk associated with these trusted communication platforms and adjust their security strategies accordingly. By combining robust technical controls with comprehensive employee education, businesses can significantly reduce their exposure to these sophisticated, social engineering-driven threats and safeguard their digital assets.





