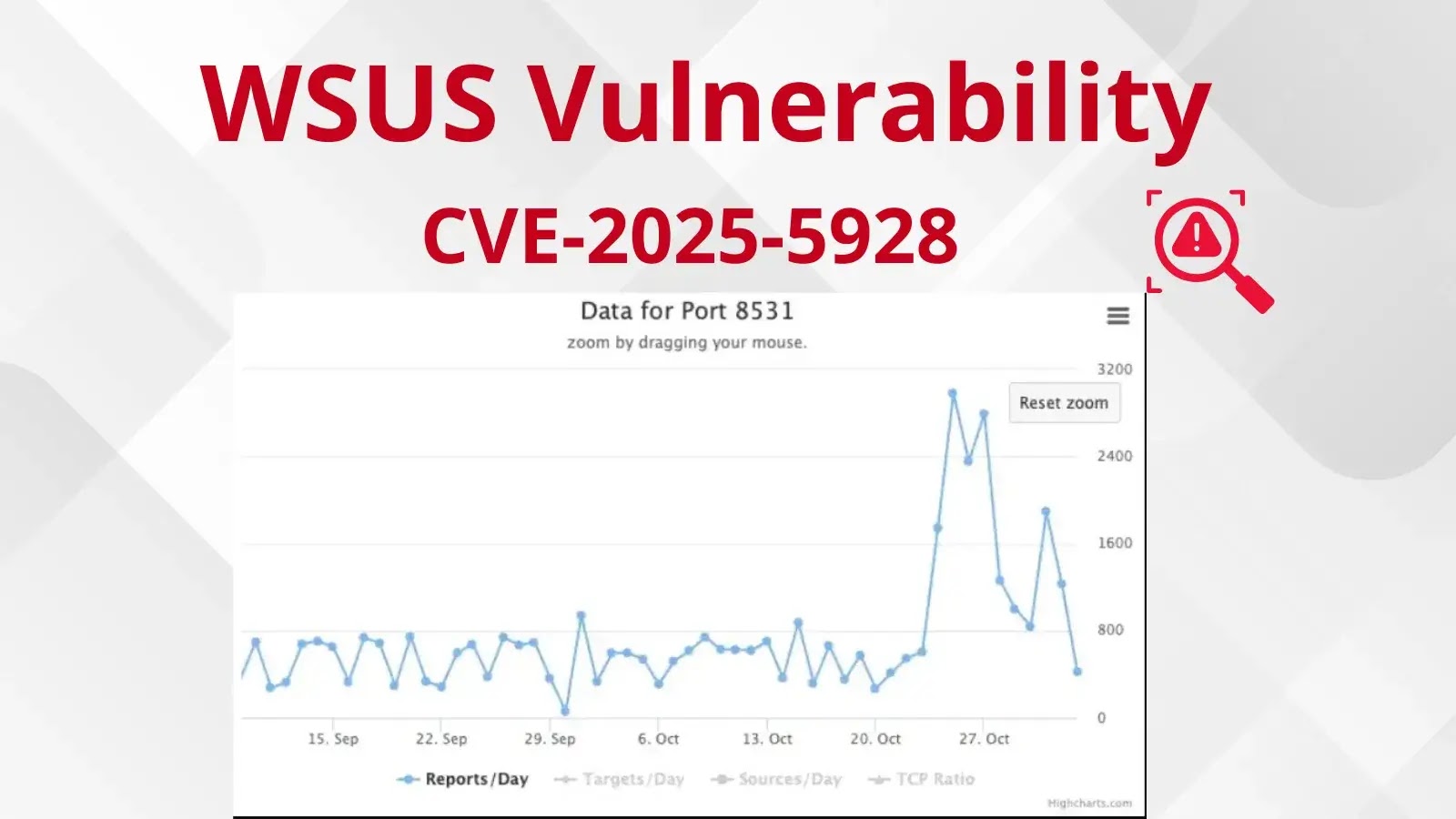
Hackers Actively Scanning for TCP Port 8530/8531 Linked to WSUS Vulnerability CVE-2025-59287
In he relentless landscape of cybersecurity, one constant remains: the proactive hunt by malicious actors for vulnerabilities. Recent intelligence shows a significant uptick in this activity, specifically targeting Windows Server Update Services (WSUS) infrastructure. Cybersecurity researchers and firewall monitoring services have reported a dramatic surge in reconnaissance scans aimed at TCP ports 8530 and 8531. This isn’t random noise; it’s a clear signal that hackers are actively probing for a critical, newly identified vulnerability: CVE-2025-59287.
This heightened scanning activity, confirmed by network sensors from organizations like Shadowserver, is a stark warning for IT professionals and security teams. Understanding this threat and taking immediate action is paramount to safeguarding your network.
The WSUS Vulnerability: CVE-2025-59287
The core of this concern revolves around an as-yet-undisclosed but actively exploited vulnerability, tracked as CVE-2025-59287. While specific details about the exploit mechanism are still emerging, the focus on TCP ports 8530 and 8531 strongly indicates that this vulnerability directly impacts how WSUS communicates and distributes updates. These ports are the standard listeners for WSUS over HTTP (8530) and HTTPS (8531) when not using the default HTTP/HTTPS ports (80/443).
An exploited WSUS server can become a significant pivot point for attackers, potentially leading to:
- Malware Distribution: Attackers could inject malicious updates, distributing malware to all connected client machines.
- System Compromise: Control over the WSUS server itself could grant an attacker high-level access within the network.
- Man-in-the-Middle Attacks: Exploiting weaknesses in update delivery mechanisms could allow attackers to intercept and alter update packages.
- Denial of Service: Causing the WSUS service to crash, disrupting critical update processes.
Understanding Windows Server Update Services (WSUS)
WSUS is a Microsoft service that allows IT administrators to manage the distribution of updates and patches for Microsoft products to computers in an organizational network. It plays a critical role in maintaining the security posture and stability of Windows-based environments. By centralizing update management, WSUS helps ensure that systems are consistently patched against known vulnerabilities. However, the very nature of its update distribution capabilities makes it a high-value target for attackers.
The recent surge in scanning activity suggests that attackers are keenly aware of the critical role WSUS plays and are actively seeking to exploit any weaknesses within its deployment, particularly those associated with CVE-2025-59287.
Detected Scanning Activity: What It Means
The immediate surge in scans on ports 8530 and 8531 is a classic reconnaissance tactic. Threat actors are mapping the internet, searching for exposed WSUS servers that might be vulnerable to CVE-2025-59287. This scanning typically precedes more targeted attacks. Organizations neglecting their WSUS security configurations or those running outdated software are prime targets.
The data from network sensors like Shadowserver provides invaluable real-time threat intelligence, highlighting that this isn’t a theoretical threat but an active, ongoing campaign by malicious entities. This intelligence demands an immediate and proactive response.
Remediation Actions
Given the active scanning and the critical nature of WSUS, immediate action is crucial. While a specific patch for CVE-2025-59287 may not yet be available, several best practices and mitigation strategies can significantly reduce your exposure.
- Isolate WSUS Servers: Ensure your WSUS servers are not directly exposed to the internet. Use firewalls and network segmentation to restrict access only to necessary internal clients and administrative workstations.
- Review Firewall Rules: Scrutinize all inbound and outbound firewall rules pertaining to TCP ports 8530 and 8531. Block external access entirely, if possible, or restrict it to trusted IP ranges.
- Implement Network Intrusion Detection/Prevention Systems (NIDS/NIPS): Configure NIDS/NIPS to monitor traffic on ports 8530/8531 for anomalous patterns, and to block suspicious connections.
- Keep WSUS Updated: While CVE-2025-59287 is new, ensure your WSUS server itself is running the latest stable version and has all previously released security updates applied.
- Use HTTPS for WSUS: If not already implemented, configure WSUS to use HTTPS (port 8531 or 443) with valid SSL certificates. This encrypts the update traffic, making man-in-the-middle attacks harder.
- Principle of Least Privilege: Ensure that the WSUS service runs with the absolute minimum necessary permissions. Review user accounts with access to the WSUS console.
- Regular Backups: Maintain regular, tested backups of your WSUS database and configuration.
- Monitor Logs: Continuously monitor WSUS server logs and network traffic logs for any signs of unusual activity or failed connection attempts to ports 8530/8531.
Relevant Tools for Detection and Mitigation
| Tool Name | Purpose | Link |
|---|---|---|
| Nmap | Network scanning and port enumeration (for internal security audits) | https://nmap.org/ |
| Wireshark | Network protocol analyzer for deep packet inspection | https://www.wireshark.org/ |
| Windows Firewall with Advanced Security | Operating system-level firewall configuration | https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-firewall/windows-firewall-with-advanced-security |
| Security Information and Event Management (SIEM) Systems | Centralized log collection and analysis (e.g., Splunk, Microsoft Sentinel) | (Vendor-specific) |
| Network Intrusion Detection/Prevention Systems (NIDS/NIPS) | Deep packet inspection for threat detection and blocking | (Vendor-specific: Snort, Suricata, commercial appliances) |
Conclusion
The active scanning for TCP ports 8530 and 8531, directly tied to the emerging WSUS vulnerability CVE-2025-59287, represents a clear and present danger to organizations. This isn’t merely background noise on the internet; it’s a precursor to targeted attacks that could severely compromise your network’s integrity and security posture. Proactive monitoring, robust firewall configurations, and a comprehensive understanding of your WSUS deployment are critical to defending against this latest threat.
Prioritize reviewing and hardening your WSUS infrastructure immediately. Staying informed and agile in your defensive strategies remains the most effective deterrent against sophisticated and evolving cyber threats.




