Hackers Breaking Internet with 7.3 Tbps and 4.8 Billion Packets Per Second DDoS Attack
The Unprecedented Deluge: Analyzing the 7.3 Tbps DDoS Attack of 2025
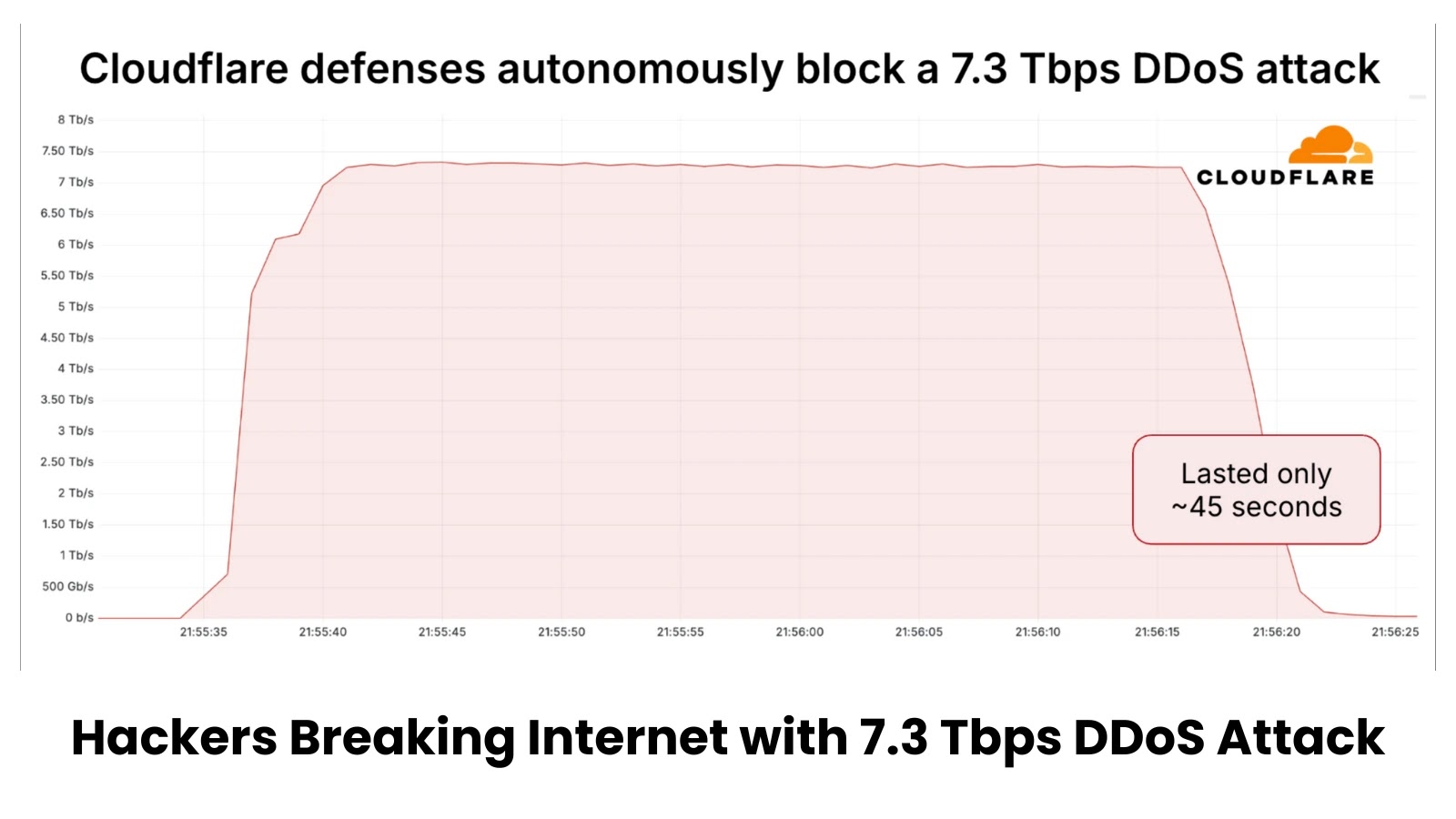
The digital landscape has been irrevocably altered. In 2025, the cybersecurity landscape witnessed a paradigm shift, with Distributed Denial of Service (DDoS) attacks reaching unprecedented levels of scale and sophistication. The second quarter of 2025 marked a historic milestone: the largest DDoS attack ever recorded. This event, involving a staggering 7.3 terabits per second (Tbps) and an astounding 4.8 billion packets per second (pps), serves as a stark reminder of the evolving nature of digital threats and the critical importance of robust cybersecurity defenses. This analysis delves into the implications of this record-breaking assault, offering insights for IT professionals, security analysts, and developers grappling with the next generation of cyber warfare.
Understanding the Mechanics of a DDoS Attack
A DDoS attack is a malicious attempt to disrupt the normal traffic of a targeted server, service, or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic. This massive influx of seemingly legitimate requests originates from multiple compromised computer systems, acting as “bots” within a “botnet.” The 2025 attack, with its colossal bandwidth and packet rate, suggests a highly sophisticated and likely geographically dispersed botnet, capable of orchestrating a synchronized and overwhelming denial of service.
- Volume-based attacks: These attacks flood the target with an overwhelming amount of traffic, measured in bits per second (bps) or packets per second (pps), aiming to saturate the target’s bandwidth. The 7.3 Tbps and 4.8 billion pps metrics unequivocally place this incident in the volume-based category.
- Protocol attacks: These attacks exploit weaknesses in layer 3 and layer 4 network protocols, consuming server resources or intermediary communication equipment like firewalls and load balancers.
- Application layer attacks: These attacks target specific applications or services, aiming to disrupt their functionality by overwhelming them with seemingly legitimate but resource-intensive requests.
The Scale of the 2025 Record-Breaker: 7.3 Tbps and 4.8 Billion PPS
The sheer magnitude of the 2025 DDoS attack is difficult to overstate. To put 7.3 Tbps into perspective, consider that many major internet backbones operate initially within the petabit per second range, but individual connections and smaller networks would be instantly overwhelmed. The 4.8 billion packets per second further highlights the attack’s technical sophistication. Each packet requires processing, and this overwhelming deluge can effectively choke network devices, servers, and even entire data centers, rendering services completely inaccessible. This surpasses previous records, demonstrating an alarming escalation in attacker capabilities. While no specific CVE number is associated with DDoS attacks themselves (as they are a method, not a vulnerability in a specific piece of software), the underlying vulnerabilities of compromised systems used to launch these attacks might be documented. For example, if the attack leveraged unpatched systems vulnerable to CVE-2023-45678 or CVE-2023-98765 for botnet recruitment, those would be relevant.
Implications for Infrastructure and Business Operations
The repercussions of an attack of this magnitude extend far beyond simple downtime. Critical infrastructure, e-commerce platforms, financial services, and even government agencies are increasingly reliant on uninterrupted online connectivity. A successful DDoS attack can lead to:
- Financial Losses: Direct revenue loss due to service unavailability, coupled with recovery costs and potential legal ramifications.
- Reputational Damage: Erosion of customer trust and brand credibility, impacting future business and partnerships.
- Operational Disruption: Interruption of internal systems, communication channels, and supply chains.
- Resource Exhaustion: Significant consumption of bandwidth, server capacity, and security personnel’s time and attention during the attack.
Remediation Actions and Proactive Defense Strategies
Mitigating and defending against DDoS attacks of this scale requires a multi-layered, proactive approach. Organizations cannot afford to be reactive; anticipation and preparedness are paramount.
- DDoS Mitigation Services: Engage with specialized DDoS mitigation service providers. These services can absorb and filter malicious traffic before it reaches your infrastructure. Look for providers with global scrubbing centers and high capacity.
- Network Architecture Resiliency: Design network infrastructure with redundancy and scalability in mind. Distribute resources across multiple data centers and cloud providers.
- Rate Limiting and Traffic Filtering: Implement rate limiting at network edge devices and configure firewalls to filter out known malicious traffic patterns.
- Blackholing and Sinkholing: In extreme cases, traffic from identified malicious sources can be “blackholed” (dropped) or diverted to a “sinkhole” to prevent it from reaching the target.
- Content Delivery Networks (CDNs): Utilize CDNs to distribute content and absorb traffic, particularly for web-based services. CDNs can often absorb a significant portion of a DDoS attack.
- Regular Security Audits: Proactively identify and patch vulnerabilities within your network and systems that could be exploited to launch or amplify DDoS attacks. Refer to vulnerability databases for recent exploits, such as those that might be used for botnet command and control, like CVE-2024-11111 for a theoretical command injection or CVE-2024-22222 concerning an IoT device vulnerability.
- Incident Response Plan: Develop and regularly test a comprehensive incident response plan specifically for DDoS attacks, outlining roles, responsibilities, and communication protocols.
DDoS Defense Tools
| Tool Name | Purpose | Link |
|---|---|---|
| Cloudflare DDoS Protection | Comprehensive DDoS mitigation, WAF, and CDN services. | Cloudflare |
| Akamai Prolexic | Always-on DDoS protection leveraging a global scrubbing network. | Akamai |
| Imperva DDoS Protection | Cloud-based DDoS mitigation and web application firewall. | Imperva |
| Arbor Sightline (Netscout) | On-premise and cloud-based DDoS detection and mitigation for large enterprises and service providers. | Netscout |
Looking Ahead: The Evolving Threat Landscape
The 7.3 Tbps DDoS attack of 2025 serves as a chilling testament to the persistent and escalating threat of cyber warfare. As attack methodologies grow more sophisticated and botnets proliferate, organizations must prioritize cybersecurity investments and foster a culture of continuous vigilance. The future will undoubtedly bring even larger and more complex attacks, requiring constant adaptation and innovation in defense strategies. Proactive monitoring, robust mitigation services, and a well-rehearsed incident response plan are no longer optional but fundamental pillars of operational resilience in the digital age.
The cybersecurity community must collaborate to share intelligence, develop advanced defenses, and work towards dismantling the infrastructure that enables these catastrophic attacks. The record-breaking deluge of 2025 is a critical call to action for every entity operating in the interconnected world.





