Hackers Exploit Critical WordPress Theme Flaw to Hijack Sites via Remote Plugin Install
Urgent Warning: Critical WordPress Theme Flaw Exploited by Hackers
The digital landscape is under constant assault, and a new threat has emerged, targeting a popular WordPress theme. Reports indicate active exploitation of a critical vulnerability in the “Alone – Charity Multipurpose Non-profit WordPress Theme.” This flaw allows threat actors to compromise susceptible websites, posing a significant risk to data integrity and operational continuity. For cybersecurity professionals, site administrators, and developers, immediate action is paramount.
Understanding the Vulnerability: CVE-2025-5394 Explained
The security flaw, officially tracked as CVE-2025-5394, has been assigned a severity score of 9.8 out of 10.0 on the CVSS (Common Vulnerability Scoring System) scale. This critical rating underscores the potential for severe impact, including complete site takeover. Security researcher Thái An is credited with the diligent discovery and responsible disclosure of this vulnerability.
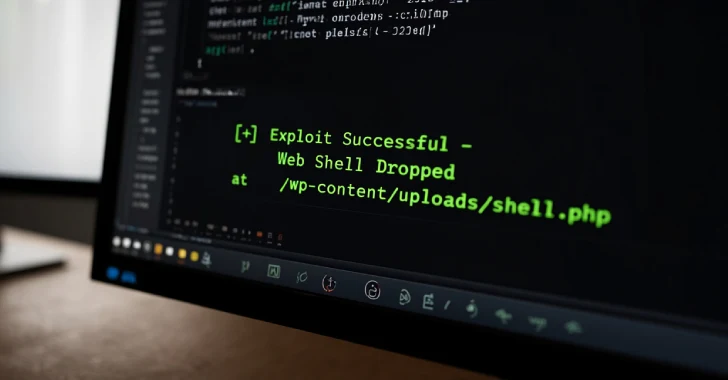
According to analysis by Wordfence, a leading authority in WordPress security, the root cause of CVE-2025-5394 is an arbitrary file upload vulnerability. This means that an attacker can upload malicious files, such as PHP scripts, to the web server without proper validation. Once a malicious file is uploaded, an attacker can execute code on the server, leading to a remote code execution (RCE) scenario. Such an exploit typically results in the attacker gaining full control over the compromised WordPress site, enabling them to:
- Deface the website.
- Inject malicious content, including malware or phishing pages.
- Steal sensitive data, such as user credentials or customer information.
- Use the compromised site as a platform for further attacks.
- Install backdoors for persistent access.
The Exploitation Vector: Remote Plugin Installation
The specific attack vector leveraged by hackers involves abusing the theme’s functionalities to facilitate a remote plugin installation. While the precise details of the exploit chain are still emerging, the arbitrary file upload vulnerability likely enables attackers to plant a malicious plugin or a component that then triggers a legitimate, albeit unauthorized, plugin installation process. This technique allows them to gain persistent control and execute arbitrary commands under the guise of legitimate WordPress operations. Organizations using the “Alone – Charity Multipurpose Non-profit WordPress Theme” are particularly at risk and should assume their sites are targets.
Remediation Actions: Protecting Your WordPress Site
Given the active exploitation of CVE-2025-5394, immediate and decisive action is crucial for all administrators utilizing the “Alone – Charity Multipurpose Non-profit WordPress Theme.”
- Update Immediately: Check for and apply the latest available patch or update for the “Alone – Charity Multipurpose Non-profit WordPress Theme.” Prioritize this action. If no official patch is yet released, consider temporarily disabling or replacing the theme until a secure version is available.
- Isolate and Scan: If your site uses this theme, assume compromise. Isolate the affected installation from other systems on your network. Perform a thorough security scan using reputable WordPress security plugins (see table below) and server-side antivirus/malware scanners.
- Backup and Restore: Ensure you have recent, uncompromised backups of your website. If a breach is confirmed, prepare to restore from a clean backup after the vulnerability has been addressed.
- Implement Web Application Firewall (WAF): Deploy a robust WAF to filter and block malicious traffic targeting your WordPress installation. Configure WAF rules to specifically block arbitrary file uploads and suspicious POST requests.
- Review User Accounts and Permissions: Audit all WordPress user accounts, especially administrative ones. Remove any unfamiliar accounts and enforce strong, unique passwords with multi-factor authentication (MFA).
- Monitor Logs: Continuously monitor WordPress and server access logs for unusual activity, such as suspicious file uploads, unauthorized login attempts, or unexpected plugin installations.
- Educate Users: Inform all site administrators and content creators about supply chain risks associated with themes and plugins.
Essential Tools for Detection and Mitigation
Leveraging the right tools is essential for effectively identifying and mitigating threats like CVE-2025-5394.
| Tool Name | Purpose | Link |
|---|---|---|
| Wordfence Security | Comprehensive WordPress security, including malware scanning, firewall, and login security. | https://www.wordfence.com/ |
| Sucuri Security | Website security platform with malware removal, WAF, and integrity monitoring. | https://sucuri.net/ |
| WPScan | WordPress vulnerability scanner (CLI tool). Useful for identifying known vulnerabilities in themes and plugins. | https://wpscan.com/ |
| Cloudflare WAF | Enterprise-grade Web Application Firewall to protect against common web exploits. | https://www.cloudflare.com/waf/ |
| Malwarebytes | Endpoint detection and response (EDR) solution for server-side scanning if malware is suspected. | https://www.malwarebytes.com/ |
Conclusion
The active exploitation of CVE-2025-5394 in the “Alone – Charity Multipurpose Non-profit WordPress Theme” serves as a stark reminder of the persistent threats facing the open-source ecosystem. Vigilance, rapid patching, and proactive security measures are your best defense. Site administrators must prioritize updating vulnerable themes, implement robust security practices, and continuously monitor their web assets to prevent compromise and safeguard digital operations.





