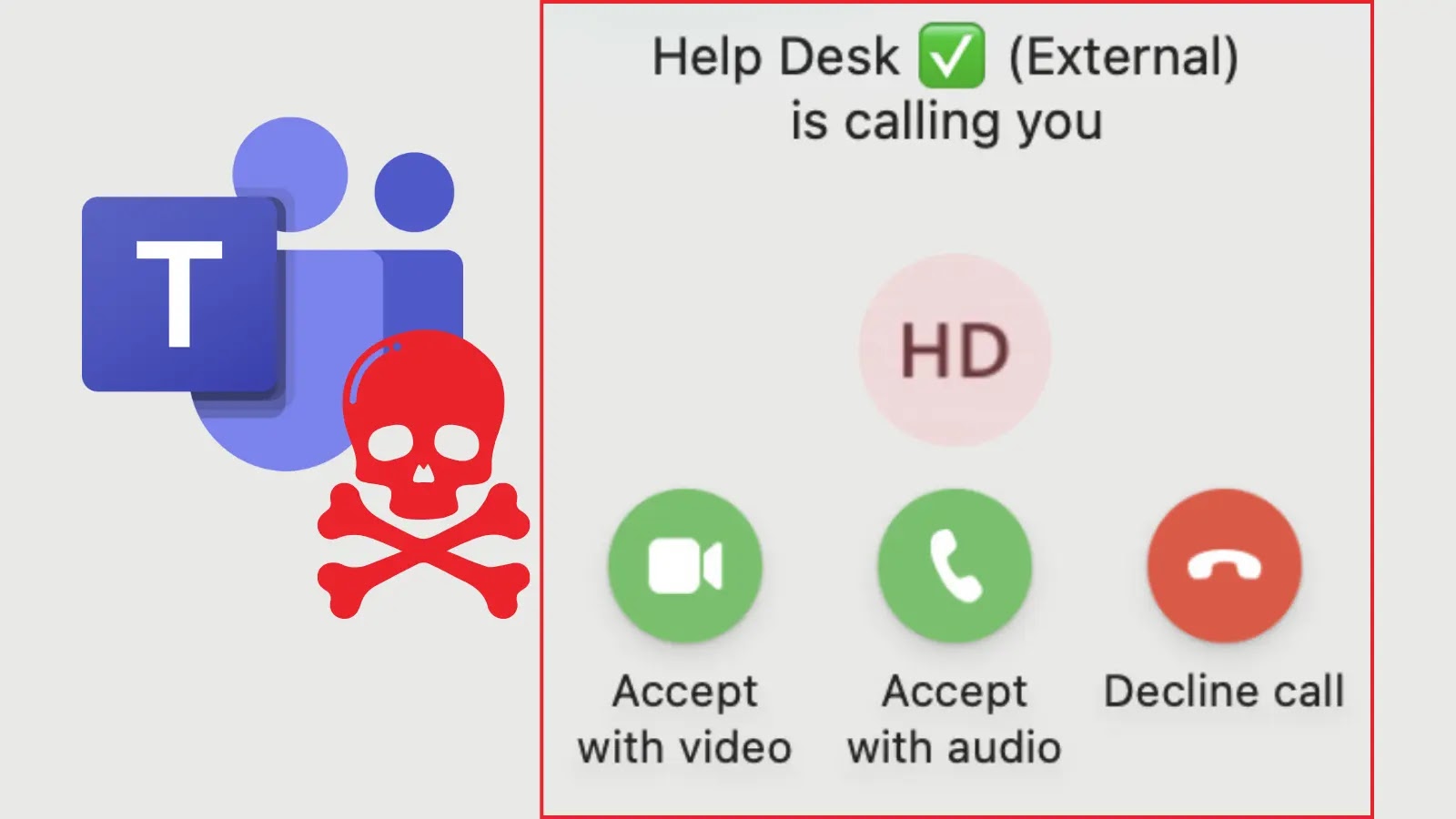
Hackers Exploit Microsoft Teams, Posing as IT Help Desk for Screen Sharing and Remote Access
The Silent Threat: How Microsoft Teams Becomes a Beachhead for Remote Access Attacks
Infiltrating an organization often begins with a meticulously crafted deception. Recent intelligence uncovers a sophisticated phishing campaign leveraging Microsoft Teams’ robust communication features to bypass traditional security perimeters. Threat actors are impersonating IT helpdesk personnel, exploiting default configurations within Teams to initiate screen sharing and gain unauthorized remote access, effectively turning a collaboration tool into an attack vector.
The Anatomy of a Teams-Based Phishing Campaign
This campaign meticulously preys on trust and urgency. Attackers initiate contact through Teams’ external communication capabilities, which are often enabled by default in Microsoft 365 tenants. This circumvents typical email security gateways, as the communication originates directly within a trusted platform. The impersonation is highly convincing, with threat actors posing as legitimate IT support responding to a fabricated “issue” that requires immediate attention.
- Initial Contact: Threat actors use Teams’ external communication feature to message targets, often claiming a critical system issue or security alert.
- Bypassing Controls: By communicating within Teams, they sidestep email security defenses (e.g., DMARC, SPF, DKIM, advanced threat protection filters) designed to flag suspicious emails.
- Social Engineering: The urgency of the fake IT support request pressures users into complying with instructions, often under the guise of “resolving” the non-existent problem.
- Exploiting Collaboration Features: The core of the attack lies in leveraging Teams’ inherent functionalities:
- Screen Sharing: Attackers request screen sharing to “diagnose” the issue, gaining immediate visual access to the victim’s desktop.
- Remote Control: The ultimate goal is to persuade the user to grant remote control, giving the attacker direct command over the compromised workstation.
Why Microsoft Teams is a Prime Target
The ubiquity of Microsoft Teams in corporate environments makes it an attractive target. Its default settings, designed for seamless collaboration, inadvertently create vulnerabilities when misconfigured or when user awareness is low. The external collaboration feature, while beneficial for inter-organizational communication, becomes a significant risk if not adequately managed and monitored. This bypasses many traditional perimeter defenses, as the attack unfolds within an authenticated and trusted application.
Understanding the Impact: Beyond Simple Phishing
Unlike typical phishing that aims for credential theft, this campaign directly leads to unauthorized system access. Once remote control is established, the potential for damage is extensive:
- Data Exfiltration: Sensitive company data can be copied and exfiltrated.
- Malware Deployment: Ransomware, spyware, or other malicious payloads can be deployed directly onto the endpoint.
- Lateral Movement: The compromised workstation serves as a beachhead for moving deeper into the corporate network.
- Account Compromise: Access to the user’s system can lead to the compromise of other accounts or applications they are logged into.
Remediation Actions and Proactive Defense
Defending against these sophisticated Teams-based attacks requires a multi-layered approach focusing on platform configuration, user education, and continuous monitoring.
- Restrict External Access:
- Review and restrict external access capabilities in Microsoft Teams. Navigate to Microsoft 365 admin center > Teams admin center > Org-wide settings > External access. Limit external domains to only those explicitly required for business operations.
- Consider disabling guest access if not strictly necessary, or implement strict guest access policies.
- Enforce Conditional Access Policies:
- Implement Azure AD Conditional Access policies requiring multi-factor authentication (MFA) for all access to Microsoft Teams, especially for external or guest users.
- Require compliant devices for accessing Teams resources.
- User Education and Awareness Training:
- Train employees to scrutinize all unsolicited requests, even those appearing to come from internal IT. Emphasize that legitimate IT personnel will rarely ask for remote control without prior notification or established protocols.
- Educate users on how to verify the identity of IT support and the appropriate channels for seeking assistance.
- Conduct simulated phishing exercises that include Teams-based scenarios.
- Monitor Teams Activity Logs:
- Regularly review Microsoft Teams audit logs for unusual activities, such as unusual external communications, large file transfers initiated by external users, or unexpected screen-sharing sessions.
- Integrate Teams logs with your Security Information and Event Management (SIEM) system for centralized monitoring and alerting.
- Disable Unnecessary Permissions:
- Configure Teams meeting policies to restrict who can present and share content, especially for external participants.
- Review and limit screen sharing and remote control permissions within your Teams environment.
- Endpoint Detection and Response (EDR):
- Ensure EDR solutions are deployed and actively monitoring all endpoints for suspicious process activity, unauthorized software installations, and C2 communication attempts that might follow remote access.
Tools for Detection and Mitigation
Leveraging the right tools is critical for enhancing your organization’s security posture against such sophisticated attacks.
| Tool Name | Purpose | Link |
|---|---|---|
| Microsoft 365 Defender | Comprehensive XDR (Extended Detection and Response) for endpoint, email, identity, and cloud apps, including Teams monitoring. | https://learn.microsoft.com/en-us/microsoft-365/security/defender/ |
| Azure AD Conditional Access | Enforce access policies based on user, location, device compliance, and application. Critical for MFA and device trust. | https://learn.microsoft.com/en-us/azure/active-directory/conditional-access/ |
| Cloud App Security (MCAS / Defender for Cloud Apps) | Monitor and control activities across cloud applications, including Teams, detecting anomalous behavior and enforcing policies. | https://learn.microsoft.com/en-us/defender-cloud-apps/ |
| Darktrace | AI-powered cyber AI platform for autonomous threat detection, responding to novel attacks like sophisticated phishing. | https://www.darktrace.com/ |
| KnowBe4 | Security awareness training and simulated phishing platform to educate users on social engineering tactics. | https://www.knowbe4.com/ |
Key Takeaways for Enterprise Security
The evolving threat landscape demands constant vigilance. This campaign targeting Microsoft Teams underscores that attackers will exploit any available vector, even trusted collaboration platforms, by leveraging human psychology and default configurations. Enterprises must move beyond perimeter-centric security, focusing on endpoint protection, identity verification, and robust user education. Proactive configuration reviews of collaboration tools like Teams are essential to prevent them from becoming an unwitting accomplice in sophisticated attacks.





