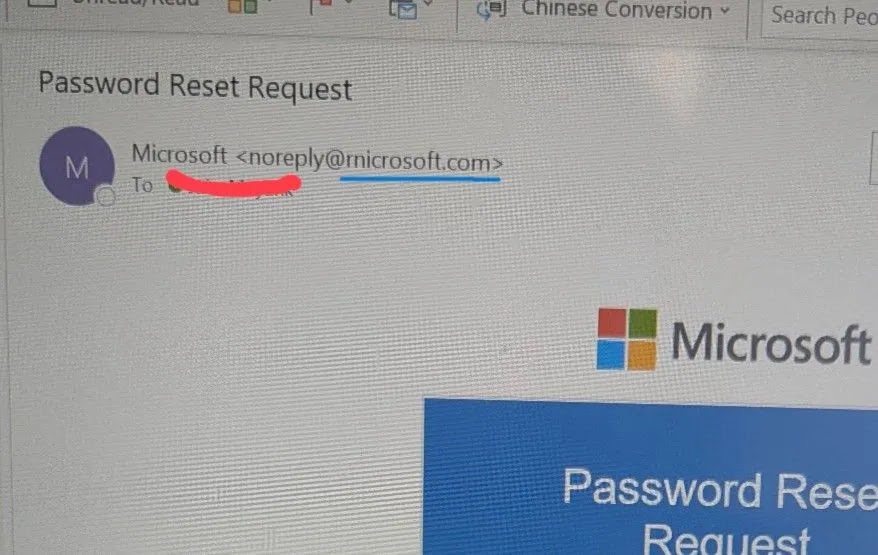
Hackers Replace ‘m’ with ‘rn’ in Microsoft(.)com to Steal Users’ Login Credentials
The Deceptive Typo: How ‘rnicrosoft.com’ Steals Credentials
In the intricate landscape of cyber threats, attackers continuously evolve their tactics to bypass even the most vigilant users. A recent and particularly insidious phishing campaign has come to light, exploiting a subtle typographical trick that transforms the familiar into a dangerous impostor. This campaign leverages the domain “rnicrosoft.com” to masquerade as the legitimate Microsoft website, meticulously designed to harvest user login credentials.
By simply replacing the letter ‘m’ with the visually similar combination of ‘r’ and ‘n’, fraudsters create a convincing visual doppelganger. This manipulation is a prime example of homograph attacks and demonstrates the persistent ingenuity of threat actors in leveraging human perception and trust against us. This isn’t a vulnerability in Microsoft’s systems directly, but rather a social engineering exploit that preys on how we quickly scan and interpret URLs.
Understanding the ‘rnicrosof.com’ Phishing Tactic
The core of this attack lies in its simplicity and effectiveness. When quickly glancing at a URL, especially in a busy digital environment, the human eye often interprets “rn” as “m.” This visual ambiguity is precisely what the attackers are banking on. Users, accustomed to seeing legitimate Microsoft login pages, might not scrutinize the URL bar closely enough to spot the substitution.
Once a user lands on the fake “rnicrosoft.com” page, they are presented with a meticulously crafted replica of the official Microsoft login portal. Unsuspecting individuals, believing they are entering their credentials into a legitimate site, unwittingly hand over their usernames and passwords directly to the attackers. This stolen information can then be used for a myriad of malicious activities, including accessing other accounts, corporate networks, and financial data.
The Mechanics of Homograph Phishing
This particular technique falls under the umbrella of homograph phishing, a method where attackers use characters that look identical or highly similar to legitimate characters in a domain name. While Unicode characters (like those from different alphabets) are often used in more complex homograph attacks, this campaign demonstrates that even simple ASCII character substitutions can be incredibly effective.
The impact of successful credential theft through such campaigns can be severe:
- Account Takeover: Attackers gain full control over the compromised Microsoft account.
- Data Breaches: Access to sensitive personal or corporate data stored within the account.
- Further Phishing: The compromised account can be used to send further phishing emails to contacts, expanding the attack surface.
- Financial Fraud: If linked to financial services, direct monetary losses.
While no specific CVE number is associated with this social engineering tactic itself (as it exploits user behavior rather than a software flaw), the consequences of falling victim can lead to vulnerabilities that would otherwise be cataloged, such as unauthorized access to systems that might be protected by multi-factor authentication if not for initial credential compromise.
Remediation Actions and Prevention
Protecting against sophisticated phishing campaigns like the “rnicrosoft.com” trick requires a multi-layered approach, combining user education with robust technical controls. Here are critical remediation actions and preventive measures:
- Verify URLs Meticulously: Always take an extra second to inspect the URL in your browser’s address bar. Look for subtle misspellings, extra characters, or unfamiliar top-level domains. For Microsoft services, ensure the domain is genuinely microsoft.com or an official subdomain.
- Use Bookmarks: Access frequently used login pages, especially for critical services, via bookmarks you’ve created yourself, rather than clicking on links in emails or external websites.
- Implement Multi-Factor Authentication (MFA): Even if credentials are stolen, MFA acts as a critical second line of defense, significantly hindering unauthorized access.
- Hover Before Clicking: Before clicking any link in an email or on a website, hover your mouse over it (without clicking) to reveal the actual destination URL. If it looks suspicious, do not click.
- Regular Security Awareness Training: Educate users about common phishing tactics, including homograph attacks and other social engineering techniques. Regular training reinforces good security practices.
- Deploy Advanced Email Security Solutions: Utilize email gateways that can detect and quarantine phishing emails, including those leveraging tricky domain names.
- Browser Security Features: Ensure your web browsers are updated and their built-in phishing and malicious site detection features are enabled.
- Report Suspicious Activity: If you encounter a suspicious website or email, report it to your IT security team or the appropriate authorities.
Tools for Detection and Mitigation
While direct detection of this specific “rnicrosoft.com” variant is primarily about user vigilance, several tools can aid in a broader phishing defense strategy:
| Tool Name | Purpose | Link |
|---|---|---|
| PhishTank | Community-based phishing URL verification | https://www.phishtank.com/ |
| Google Safe Browsing | API for checking URLs against known phishing/malware lists | https://developers.google.com/safe-browsing |
| Email Security Gateways (e.g., Proofpoint, Mimecast) | Advanced email threat protection, URL rewriting, sandboxing | (Provider specific, e.g., https://www.proofpoint.com/) |
| Web Application Firewalls (WAFs) | Protect web applications from common attacks, though less direct for client-side URL spoofing. | (Provider specific, e.g., https://aws.amazon.com/waf/) |
Final Thoughts
The “rnicrosoft.com” phishing campaign serves as a stark reminder that even the simplest of deceptive tactics can be highly effective against an unwary public. Cybersecurity is not solely about complex technical defenses; it’s also about fostering a culture of vigilance and critical thinking among users. By understanding the methods employed by attackers and embracing proactive security measures, both individuals and organizations can significantly reduce their risk of falling victim to such credential theft schemes.





