How Businesses Stop Complex Social Engineering Attacks Early – An SOC Team Guide
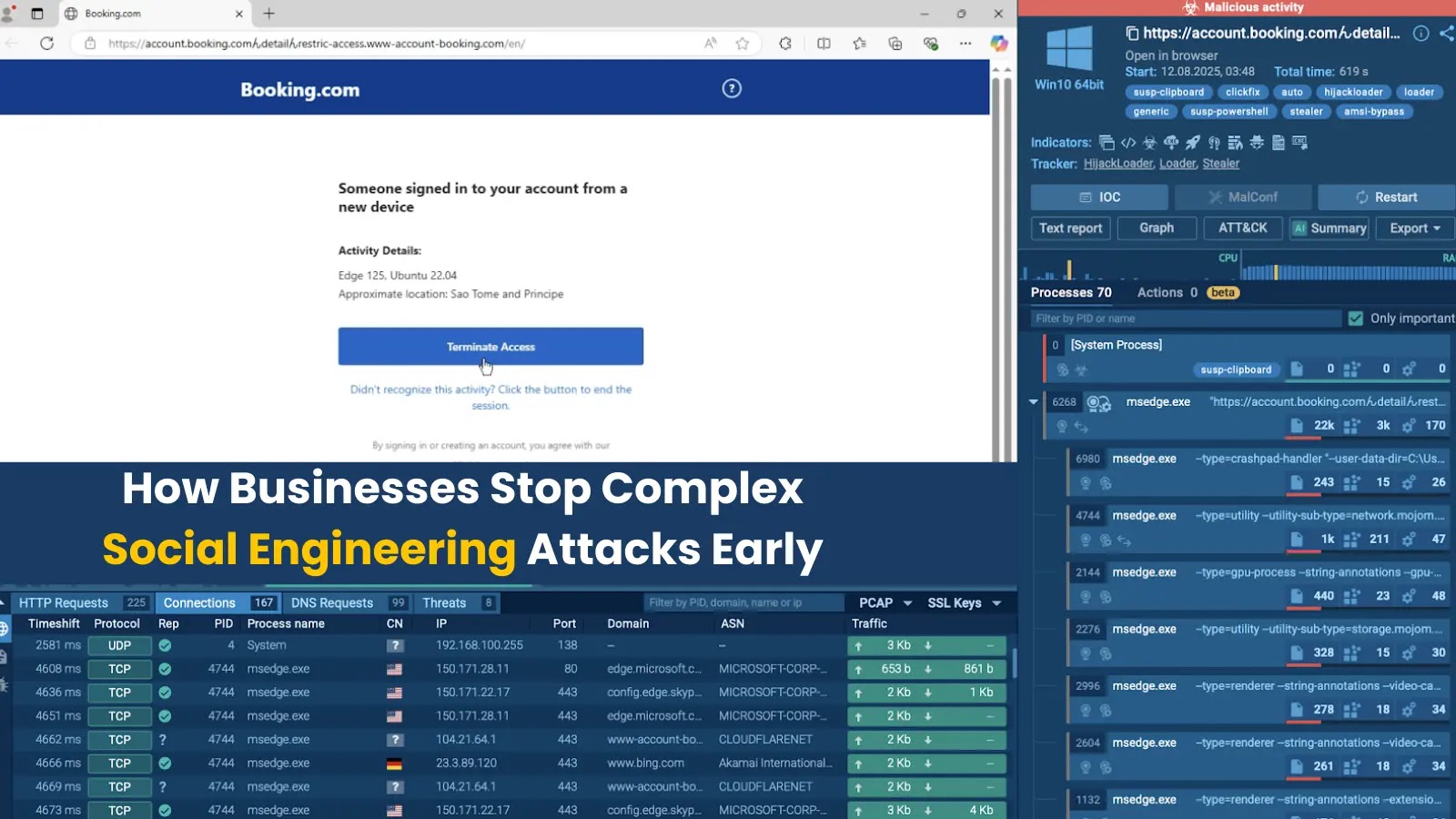
The landscape of cyber threats has transformed dramatically. Gone are the days when phishing attempts were easily spotted by glaring grammatical errors or suspicious sender addresses. Today’s social engineering attacks, often supercharged by advanced AI and accessible professional-grade toolkits, are becoming almost indistinguishable from legitimate communications. This evolution poses a significant challenge for modern security teams: these sophisticated threats frequently bypass automated defenses, revealing their true nature only after a user has taken an action – clicking a malicious link, solving a deceptive CAPTCHA, or following a “verification” step. For Security Operations Center (SOC) teams, the imperative is clear: how do we detect and neutralize these complex social engineering attacks before they impact the business? This guide delves into proactive strategies for early detection and prevention.
The Evolving Threat of AI-Powered Social Engineering
Attackers are leveraging artificial intelligence to craft highly convincing and personalized social engineering campaigns. AI can analyze vast amounts of public data to create incredibly targeted spear phishing emails, deepfake voice replicas for vishing attacks, and even generate realistic rogue websites. This sophistication makes traditional user awareness training, while still vital, insufficient on its own. The volume and realism of these attacks mean that even vigilant employees can be deceived. For instance, a recent surge in business email compromise (BEC) schemes involves AI-generated impersonations, making ‘from’ address verification inadequate. The real challenge lies in the subversion of trust indicators that users have been trained to rely on.
The User as the Early Warning System (and Target)
The fundamental issue with modern social engineering is that the attack vector *is* the user. Unlike malware that might trigger network anomalies or exploit system vulnerabilities (e.g., CVE-2023-23397 for Outlook privilege escalation), social engineering directly manipulates human behavior. This means the earliest signs of compromise often manifest at the user level: a sudden request for unusual financial transactions, an employee clicking on a login page for a legitimate service that turns out to be a cleverly crafted replica, or following instructions embedded within a seemingly innocuous document. The critical window of opportunity for defense materializes between the user’s initial interaction and the attacker’s ultimate goal.
Proactive SOC Strategies for Early Detection
Detecting complex social engineering attacks early requires a multifaceted approach that combines technological vigilance with enhanced human intuition and rapid response capabilities. SOC teams need to pivot from purely reactive incident response to proactive threat hunting and preventative measures.
- Enhanced Endpoint Telemetry & Behavioral Analytics: Beyond standard antivirus, strong Endpoint Detection and Response (EDR) solutions are crucial. These tools monitor user behavior and system processes for anomalous activities. For example, an EDR might flag an executable launched from a web browser’s download folder immediately after clicking a link that circumvented email security, even if the executable itself isn’t recognized as malicious by signature-based tools yet.
- Advanced Email Security Gateways (SEG) with AI/ML: While some attacks slip through, next-generation SEGs that incorporate machine learning and AI for anomaly detection are more effective. They can analyze subtle header manipulations, domain spoofing variations, and even the sentiment and urgency of email content that might indicate a social engineering attempt.
- User Sandboxing and Isolation: Implementing browser isolation or URL sandboxing protects users from directly interacting with potentially malicious web content. If a user clicks a suspicious link, the page is rendered in an isolated environment, preventing malware delivery or credential harvesting from impacting the enterprise network.
- Security Information and Event Management (SIEM) with User and Entity Behavior Analytics (UEBA): A robust SIEM with UEBA capabilities can baseline normal user behavior. Deviations – such as an employee logging in from an unusual location, accessing sensitive data outside of normal working hours, or performing an uncharacteristic number of file transfers – can trigger alerts, indicating potential account compromise via social engineering.
- Continuous Security Awareness Training (beyond “click here”): Training must evolve to address the new sophistication. Focus on critical thinking, recognizing subtle psychological manipulation tactics, and establishing robust internal verification protocols for high-value requests (e.g., funds transfers, credential changes). Simulating advanced phishing and vishing attacks can also help harden user defenses.
- Threat Intelligence Integration: Subscribing to and actively integrating high-fidelity threat intelligence feeds specific to social engineering tactics, techniques, and procedures (TTPs) helps SOC teams anticipate new attack methods and develop targeted detection rules.
- Rapid Incident Response Playbooks for Social Engineering: Develop clear, concise playbooks for common social engineering scenarios. These should outline immediate steps for containment, investigation, and recovery, focusing on rapid user account compromise remediation and data loss prevention.
Remediation Actions and Long-Term Resilience
Once a social engineering attempt is detected, rapid and decisive action is paramount to minimize impact. Long-term, building organizational resilience against these attacks requires continuous improvement and adaptation.
- Immediate User Account Compromise Response: If a user’s credentials are suspected of being compromised, immediately force a password reset, revoke active sessions, and multi-factor authentication (MFA) tokens. Investigate lateral movement within the network.
- Communication and Awareness Reinforcement: If an attack successfully reached users, communicate the details (anonymously if necessary) across the organization. This reinforces training and raises collective vigilance.
- Phishing Campaign Analysis: Analyze the vector, content, and targeting of the attack. Use this intelligence to refine email filters, create new SIEM rules, and update training materials.
- Tabletop Exercises: Regularly conduct tabletop exercises simulating complex social engineering incidents. This tests the effectiveness of playbooks and identifies gaps in procedures and communication.
- Zero Trust Architecture (ZTA): Implementing ZTA reduces the blast radius of any successful social engineering attack. By verifying every user, device, and application before granting access, and by applying least privilege principles, even compromised credentials have limited utility.
Essential Tools for SOC Teams in the Fight Against Social Engineering
Effective defense against sophisticated social engineering relies on a robust security stack. Here are some categories of tools crucial for modern SOC operations:
| Tool Category | Purpose | Link Examples (Vendor Agnostic) |
|---|---|---|
| Endpoint Detection & Response (EDR) | Monitors endpoints for malicious activities, behavioral anomalies, and provides rapid response capabilities. | CrowdStrike Falcon, Microsoft Defender for Endpoint, SentinelOne |
| Security Information & Event Management (SIEM) / UEBA | Aggregates security logs, correlates events, and analyzes user behavior for suspicious patterns. | Splunk Enterprise Security, Microsoft Sentinel, Exabeam |
| Advanced Email Security Gateway (SEG) | Filters malicious emails using AI, machine learning, sandboxing, and threat intelligence. | Proofpoint, Mimecast, Abnormal Security |
| Security Awareness Training Platforms | Provides simulated phishing campaigns and educational modules to harden users against social engineering. | KnowBe4, Cofense, SANS Security Awareness |
| Threat Intelligence Platforms (TIP) | Aggregates, normalizes, and contextualizes threat data to inform detection and prevention strategies. | Recorded Future, Anomali, Mandiant Threat Intelligence |
| Browser Isolation / URL Sandboxing | Renders untrusted web content in an isolated environment, preventing direct interaction with malicious sites. | Menlo Security Cloud Platform, Zscaler Cloud Browser Isolation |
Conclusion
The battle against complex social engineering attacks is ongoing and demands a proactive, adaptable stance from SOC teams. The days of relying solely on automated defenses are over; the human element, both as the primary target and a critical component of the defense, must be central to any strategy. By integrating advanced technological solutions, fostering a culture of continuous security awareness, and developing agile incident response capabilities, businesses can significantly reduce their susceptibility to these increasingly sophisticated threats, detecting and stopping them long before they escalate into major breaches.





