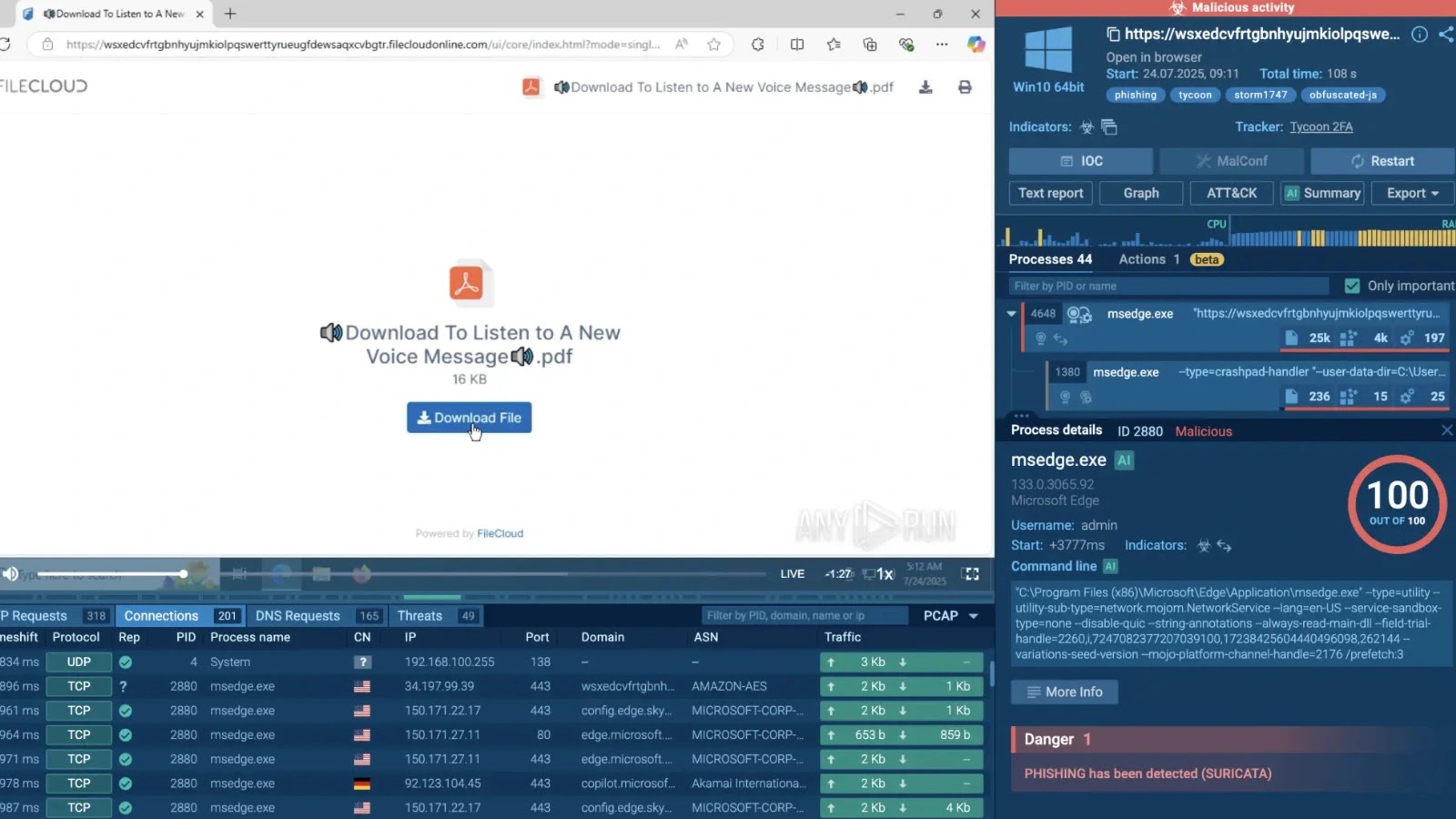
How ClickFix and Multi-Stage Phishing Frameworks Are Breaking Enterprise Defenses
The cybersecurity landscape has undergone a profound shift, with August 2025 marking a critical inflection point. Threat actors are no longer relying on rudimentary phishing attempts; instead, they are deploying sophisticated multi-stage phishing frameworks and advanced social engineering tactics that consistently bypass traditional enterprise security defenses. This evolution necessitates a fundamental re-evaluation of established security paradigms. This post delves into how these advanced frameworks, particularly highlighted by the emergence of “ClickFix” campaigns, are systematically breaking enterprise defenses and what actions organizations must take to counter them.
The Evolution of Phishing: Beyond Simple Lures
For years, enterprises focused on filtering out single-stage phishing emails. However, the game has changed. Cybersecurity researchers confirm that cybercriminals have embraced multi-stage approaches, creating intricate attack chains. These campaigns often involve an initial, seemingly benign compromise that paves the way for further, more damaging payload delivery or credential harvesting. This layered approach significantly increases the difficulty of detection and strengthens the attack’s resilience against conventional security tools.
ClickFix and Multi-Stage Frameworks: A New Threat Paradigm
ANY.RUN security researchers have identified three major campaign families that epitomize this shift. While the specific names of all three families aren’t always disclosed publicly for security reasons, the overarching methodology points to a significant departure from previous tactics. These frameworks are designed to be stealthy, adaptive, and highly effective at bypassing common security controls like multi-factor authentication (MFA) and email gateways. The term “ClickFix” itself signifies a campaign designed to “fix” or overcome security obstacles, guiding victims through a series of steps that incrementally compromise their defenses.
Understanding the Multi-Stage Modus Operandi
- Initial Foothold: Unlike direct payload delivery, the initial contact might be an innocuous-looking email or a link to a seemingly legitimate, but compromised, site. This stage often focuses on gathering preliminary information or planting a small, undetectable beacon.
- Credential Theft Orchestration: Once the initial foothold is secured, threat actors employ sophisticated techniques to trick users into divulging credentials. This might involve highly personalized phishing pages, deceptive login prompts, or even voice phishing (vishing) initiated after email contact.
- Bypassing MFA: Contemporary multi-stage frameworks are increasingly adept at circumventing MFA. Techniques include real-time phishing proxy services that sit between the user and the legitimate login page, capturing and relaying MFA codes as they are entered, or manipulating session tokens.
- Persistence and Lateral Movement: Post-compromise, these frameworks aim for persistence within the network. This could involve establishing backdoors, deploying remote access tools, or exploiting vulnerabilities to move laterally across systems, escalating privileges and exfiltrating sensitive data.
Remediation Actions: Fortifying Enterprise Defenses
Countering these advanced multi-stage phishing frameworks requires a multi-layered and proactive defense strategy. Relying solely on perimeter defenses is no longer sufficient.
- Strengthen Email Gateway Defenses: Implement advanced threat protection (ATP) solutions for email that include sandboxing, URL rewriting, and AI-driven anomaly detection to identify and block sophisticated phishing attempts before they reach end-users.
- Enhance Endpoint Detection and Response (EDR)/Extended Detection and Response (XDR): Deploy robust EDR/XDR solutions capable of detecting suspicious activities, process injections, and unauthorized network connections, even if the initial phishing attempt slips through.
- Implement User Training and Awareness: Conduct continuous and interactive security awareness training that focuses on identifying social engineering tactics, recognizing phishing indicators (even subtle ones), and understanding the risks of suspicious links and attachments. Emphasize the importance of reporting suspicious activity.
- Adopt Phishing-Resistant MFA: Move beyond SMS or TOTP-based MFA where possible. Implement FIDO2-compliant security keys (e.g., YubiKey, Google Titan Security Key) or certificate-based authentication, which are significantly harder for threat actors to bypass via phishing.
- Regularly Patch and Update Systems: Maintain a rigorous patching schedule for all operating systems, applications, and network devices to close known vulnerabilities that threat actors might exploit. While not directly related to phishing, CVEs such as CVE-2023-23397 (a Microsoft Outlook elevation of privilege vulnerability) illustrate how software flaws can be chained with social engineering.
- Implement Zero Trust Principles: Adopt a “never trust, always verify” approach. Micro-segment networks, enforce least privilege access, and continuously verify user and device identities regardless of their location on the network.
- Threat Intelligence Integration: Subscribe to and actively leverage threat intelligence feeds. Understanding known indicators of compromise (IoCs) and tactics, techniques, and procedures (TTPs) associated with new frameworks like ClickFix allows organizations to proactively adjust their defenses.
Tools for Detection and Mitigation
Deploying the right tools is crucial for effective defense against multi-stage phishing frameworks.
| Tool Name | Purpose | Link |
|---|---|---|
| Proofpoint Email Protection | Advanced email threat protection, spam, phishing, and malware defense. | proofpoint.com |
| Microsoft Defender for Endpoint | Endpoint detection and response (EDR), vulnerability management. | microsoft.com |
| CrowdStrike Falcon Insight XDR | Extended detection and response across endpoints, cloud, identity, and data. | crowdstrike.com |
| KnowBe4 Security Awareness Training | User training, simulated phishing, and security culture-building platform. | knowbe4.com |
| YubiKey (FIDO2) | Hardware security keys for phishing-resistant multi-factor authentication. | yubico.com |
Conclusion
The rise of ClickFix and other multi-stage phishing frameworks represents a significant escalation in the cyberthreat landscape. Traditional, siloed security approaches are proving inadequate against these highly sophisticated and adaptive attacks. Organizations must recognize the gravity of this shift and adopt a holistic, defense-in-depth strategy that prioritizes robust email security, advanced endpoint protection, continuous user education, and the adoption of strong, phishing-resistant authentication methods. Proactive threat intelligence integration and a commitment to zero-trust principles are no longer optional; they are essential for protecting enterprise defenses against credential theft and system compromise in this evolving threat environment.





