How SOC Teams Detect Can Detect Cyber Threats Quickly Using Threat Intelligence Feeds
Accelerating Cyber Threat Detection: The Power of Threat Intelligence Feeds for SOC Teams
Security Operations Centers (SOCs) are the front lines of defense for organizations, tasked with safeguarding critical digital assets against a relentless barrage of cyber threats. Their effectiveness is often measured by key performance indicators (KPIs) such as Mean Time to Detect (MTTD) and False Positive Rate (FPR). While these metrics might seem distinct, they are deeply interconnected; improvements in one invariably enhance the other. A crucial enabler for this synergy, and for truly rapid threat detection, is the strategic integration of robust threat intelligence feeds.
The Interplay of MTTD and FPR in Threat Detection
Understanding the relationship between MTTD and FPR is fundamental for any high-performing SOC. A low MTTD signifies that threats are identified quickly, minimizing potential damage. However, achieving a low MTTD at the expense of a high FPR means SOC analysts are constantly sifting through a deluge of benign alerts, leading to alert fatigue and potentially missing legitimate threats. Conversely, a low FPR is desirable, ensuring that only actual threats warrant attention. Yet, if achieving this low FPR results in a high MTTD because detection rules are too conservative, real threats could linger undetected for extended periods.
The goal is to optimize both: reduce the time it takes to identify a genuine threat while simultaneously minimizing the noise of false alarms. This is where high-quality threat intelligence becomes invaluable.
What Are Threat Intelligence Feeds?
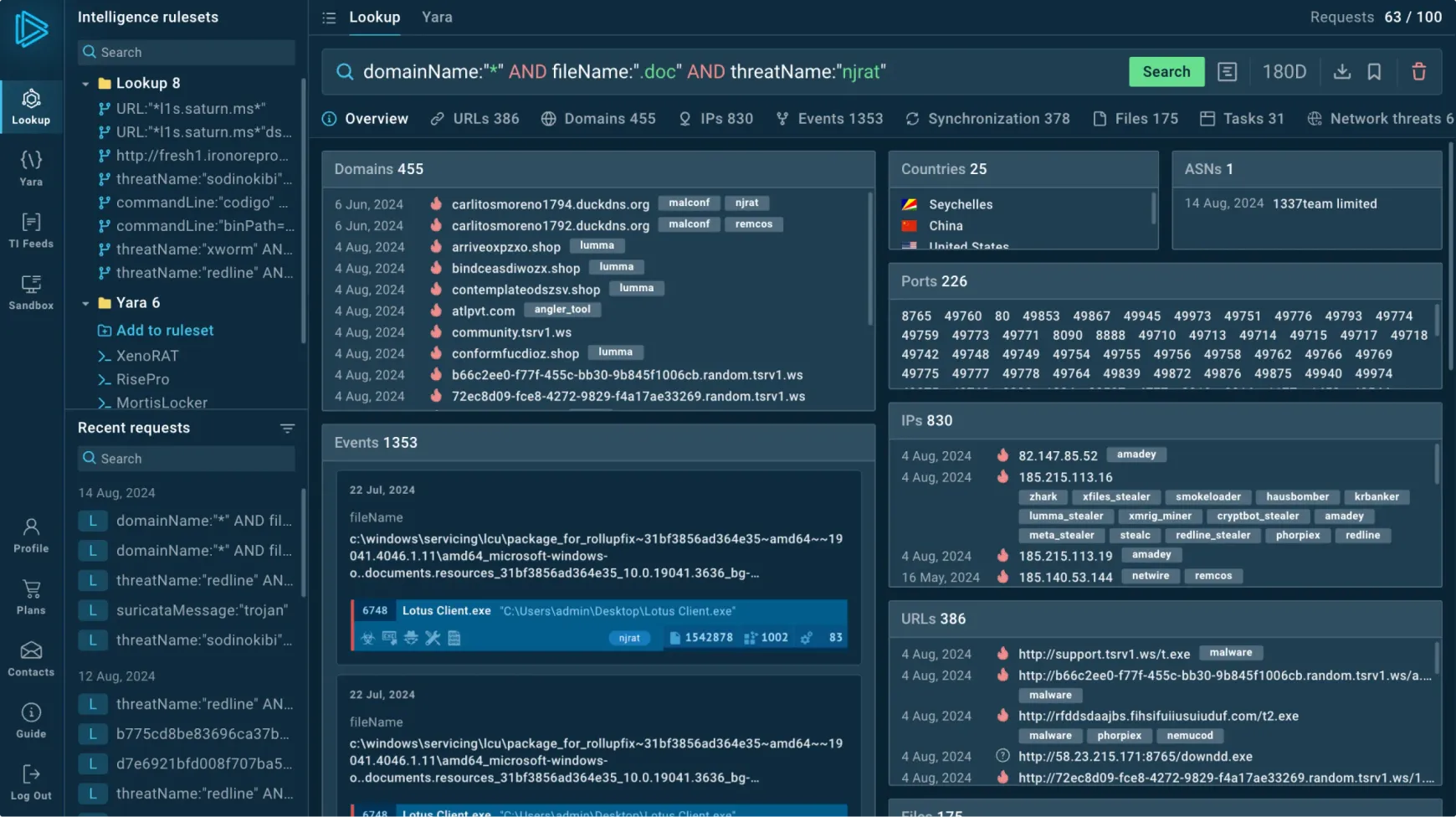
Threat intelligence feeds are continuously updated streams of information about known and emerging cyber threats. They provide actionable context about:
- Indicators of Compromise (IoCs): Malware hashes, malicious IP addresses, domain names, and URLs associated with known attacks.
- Tactics, Techniques, and Procedures (TTPs): Descriptions of how threat actors carry out attacks, including their methodologies and tools.
- Actor Profiles: Information about specific threat groups, their motivations, and past campaigns.
- Vulnerability Information: Details on newly discovered vulnerabilities, often before public disclosure. For instance, awareness of a critical vulnerability like CVE-2023-45678 from a threat feed allows proactive patching or detection rule creation.
These feeds are aggregated from various sources, including security research firms, government agencies, honeypots, and open-source intelligence (OSINT).
How Threat Intelligence Feeds Enhance SOC Operations
Integrating threat intelligence feeds into a SOC’s security ecosystem offers several critical benefits for accelerating threat detection and reducing FPR:
- Proactive Detection: Instead of waiting for an attack to manifest, SOCs can proactively scan their networks and logs for IoCs present in threat feeds. This “hunting” approach can detect early-stage compromise.
- Contextual Enrichment: When an alert is triggered by a Security Information and Event Management (SIEM) system or Endpoint Detection and Response (EDR) solution, threat intelligence can immediately provide context. Is the source IP address known to be malicious? Is the observed malware signature associated with a specific threat actor targeting your industry? This enrichment helps analysts quickly differentiate between genuine threats and benign anomalies, significantly reducing FPR.
- Faster Incident Response: With enriched alerts, analysts spend less time researching threats and more time on containment and remediation. Knowing the TTPs of an attacker allows for more focused incident response strategies.
- Prioritization of Alerts: Not all alerts are created equal. Threat intelligence can help assign a severity score or confidence level to alerts based on the reputation of the IoC or the observed TTPs, allowing SOC analysts to prioritize their efforts effectively.
- Predictive Capabilities: By analyzing trends in threat intelligence, SOCs can anticipate future attack vectors and strengthen their defenses before a new campaign even targets them. For example, if a specific ransomware group is increasingly using a particular exploit (e.g., related to CVE-2023-12345 as its initial access vector), the SOC can specifically monitor for indicators related to that exploit.
Integrating Threat Intelligence into Your SOC Workflows
Effective integration is paramount. Simply subscribing to feeds isn’t enough; the intelligence must be actionable. This typically involves:
- Automated Ingestion: Feeds should be automatically ingested into SIEMs, SOAR (Security Orchestration, Automation, and Response) platforms, firewalls, and EDR solutions.
- Correlation and Analysis: Security tools should be configured to correlate internal telemetry with external threat intelligence. This correlation generates enriched alerts.
- Custom Rule Creation: Threat intelligence can inform the creation of custom detection rules in SIEMs, tailored to the specific threats relevant to the organization’s industry and risk profile.
- Regular Validation: Threat intelligence providers and their feeds should be regularly evaluated for accuracy and relevance to minimize the ingestion of stale or low-quality data that could increase FPR.
Key Takeaways: Empowering Rapid Threat Detection
For SOC teams striving to achieve optimal MTTD and FPR, high-quality threat intelligence feeds are not an optional extra but a foundational requirement. By providing timely, contextual, and actionable information about cyber threats, these feeds enable proactive defense, accelerate incident response, and empower analysts to focus on genuine security incidents. The result is a more efficient, effective, and resilient security operation capable of detecting and mitigating cyber threats with precision and speed.





