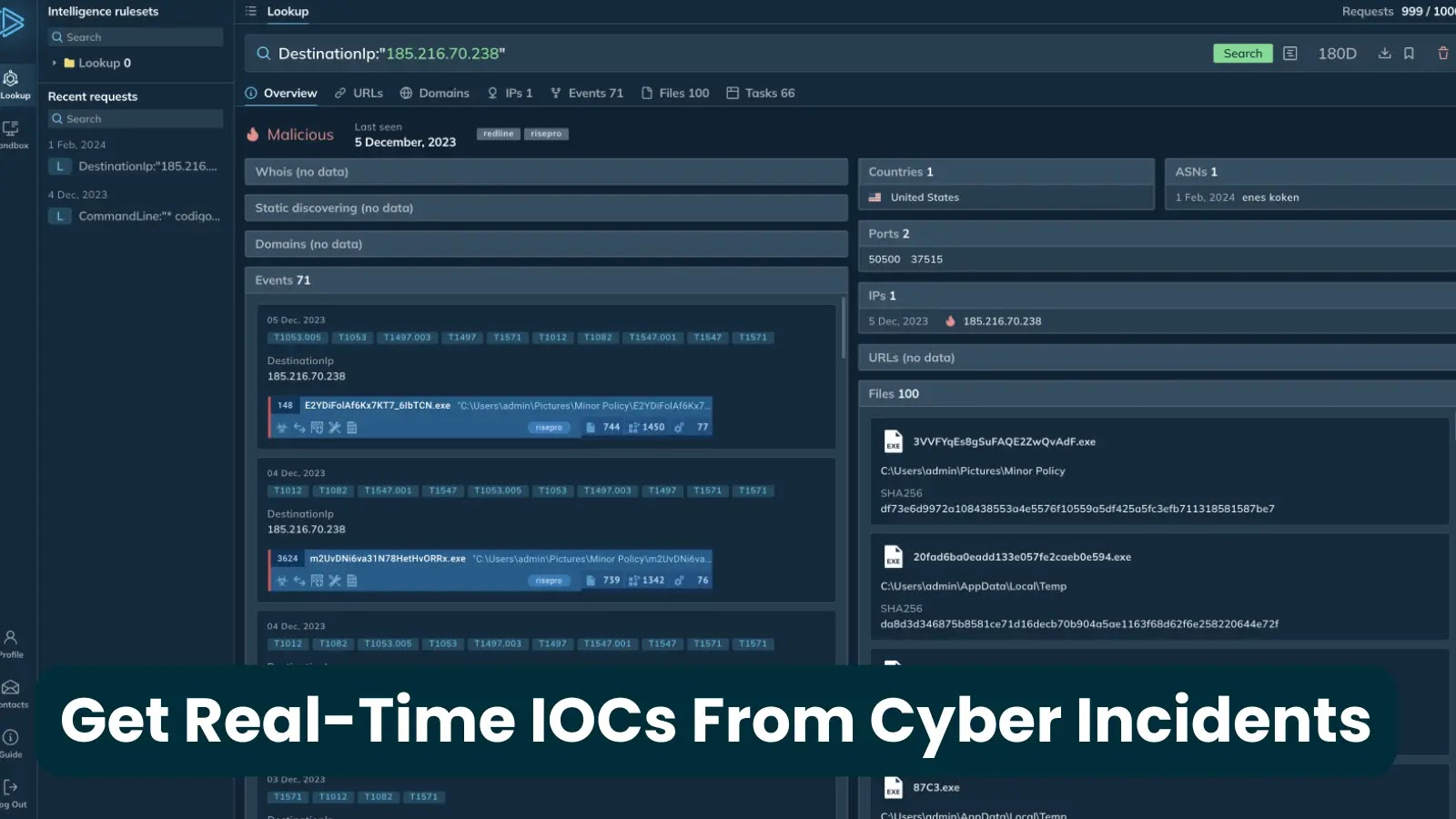
How To Get Real-Time IOCs From Incidents Across 15K SOCs
In the relentless battle against cyber threats, mere reactivity is a losing strategy. Proactive defense hinges on immediate access to critical intelligence. For security operations centers (SOCs) tasked with safeguarding an organization’s crown jewels, time is always of the essence. The challenge isn’t just about identifying an attack; it’s about anticipating the next move, understanding the adversary’s tactics, and leveraging fresh indicators of compromise (IOCs) before they widely propagate. But how does an organization gain real-time insights from incidents unfolding across thousands of other SOCs, transforming disparate data points into actionable intelligence?
The Imperative of Real-Time Threat Data
Cybersecurity is a dynamic landscape where the efficacy of defenses is directly proportional to the quality and timeliness of threat intelligence. Every component of a robust security posture—from network monitoring and intrusion detection systems to incident response playbooks and sophisticated analytics platforms—relies fundamentally on continuous, high-fidelity data feeds. Stale IOCs are a liability; real-time IOCs are a strategic advantage.
The foundation of effective cybersecurity isn’t just about having systems in place; it’s about the data that fuels them. Consider the rapid spread of a zero-day exploit, or a new phishing campaign employing novel evasion techniques. If one SOC detects an IOC, sharing that information instantaneously with others could prevent widespread compromise across countless enterprises. This concept underpins the critical need for a collaborative, real-time intelligence exchange.
The Challenge: Siloed Information and Delayed Dissemination
Despite the interconnected nature of the internet, threat intelligence often remains siloed. An incident detected in one organization may take hours, days, or even weeks to be analyzed, attributed, and then disseminated as actionable IOCs, by which point the threat actor may have already moved on or evolved their attack. This delay creates a significant window of vulnerability that adversaries readily exploit.
- Manual Correlation: Many SOCs rely on manual processes or disparate systems to correlate incident data, leading to delays.
- Proprietary Feeds: While commercial threat intelligence feeds offer valuable data, they don’t always provide the granularity or real-time insights derived from active incidents in thousands of diverse environments.
- Trust Boundaries: Sharing sensitive incident data across organizations requires robust trust frameworks and secure exchange mechanisms.
Unlocking Collective Intelligence: IOCs from 15K SOCs
The vision of obtaining real-time IOCs from a vast network of 15,000 (or more) SOCs represents a paradigm shift in collective defense. It moves beyond traditional threat intelligence to a model of immediate, crowd-sourced insight. While the reference article alludes to this capability without detailing a specific solution, the underlying principles involve advanced data aggregation, anonymization, and rapid dissemination technologies. This could be facilitated by:
- Centralized Threat Intelligence Platforms (TIPs): Specialized platforms designed to ingest, process, and distribute threat intelligence at scale.
- Automated Indicator Sharing: Utilizing industry standards like STIX (Structured Threat Information eXpression) and TAXII (Trusted Automated eXchange of Indicator Information) to automate the exchange of IOCs.
- Federated Learning/Analytics: Applying machine learning techniques across distributed datasets (from multiple SOCs) without directly sharing sensitive raw data. This allows for the discovery of patterns and anomalies indicative of new threats.
- Real-Time Anomaly Detection: Systems that can rapidly identify unusual activity patterns that deviate from baselines, signaling potential compromise.
The Value Proposition: Proactive Defense at Scale
Access to real-time IOCs from a massive network of active incidents provides unparalleled proactive defense capabilities:
- Early Warning System: Detect and block emerging threats before they reach your network, based on observations from other compromised environments.
- Reduced Mean Time To Detect (MTTD): Significantly decrease the time it takes to identify a new threat within your own infrastructure.
- Enhanced Incident Response: Arm incident response teams with immediate, actionable intelligence, streamlining investigation and remediation.
- Improved Threat Hunting: Provide security analysts with fresh leads and indicators to proactively hunt for threats that may have bypassed initial defenses.
- Predictive Capabilities: Identify nascent attack campaigns and adversary tactics, techniques, and procedures (TTPs) as they evolve.
Remediation Actions and Strategic Implementation
While the goal of accessing real-time IOCs from a vast network of SOCs is aspirational and often facilitated by commercial or collaborative initiatives, organizations can take concrete steps to prepare and leverage such capabilities:
- Standardize Data Formats: Ensure your internal security tools and processes can ingest and export threat intelligence using open standards like STIX/TAXII. This facilitates interoperability.
- Invest in Automated Orchestration: Implement Security Orchestration, Automation, and Response (SOAR) platforms that can automatically ingest IOCs and trigger defensive actions (e.g., blocking IPs, quarantining files).
- Participate in Information Sharing Groups: Join industry-specific Information Sharing and Analysis Centers (ISACs) or participate in broader threat intelligence sharing communities.
- Adopt a “Data-First” Security Mindset: Prioritize the quality, velocity, and breadth of security data collected from all endpoints, networks, and applications.
- Regularly Validate IOCs: Not all IOCs are created equal. Implement processes to validate the efficacy and relevance of incoming indicators to avoid alert fatigue.
The Future is Collaborative
The future of cybersecurity is intrinsically linked to collaboration and the rapid, efficient exchange of high-quality threat intelligence. Moving towards a model where real-time IOCs from thousands of SOCs can be aggregated, analyzed, and disseminated represents the next frontier in collective defense. It’s about leveraging the collective experience of the security community to stay not just one, but many steps ahead of adversaries. Organizations that embrace this collaborative, data-driven approach will be best positioned to protect their assets in an increasingly hostile digital environment.





