How Winning SOCs Always Stay Ahead of Threats
The relentless barrage of cyberattacks poses an existential threat to businesses worldwide. Yet, amidst this escalating danger, a select group of Security Operations Centers (SOCs) consistently demonstrate remarkable resilience, preventing breaches and safeguarding organizational integrity. These high-performing SOCs are not just a line of defense; they are strategic assets, indispensable for sustainable growth and long-term viability. What precisely empowers these elite SOC teams to not only react to threats but to consistently stay ahead of them?
Prioritizing Quality Over Sheer Volume
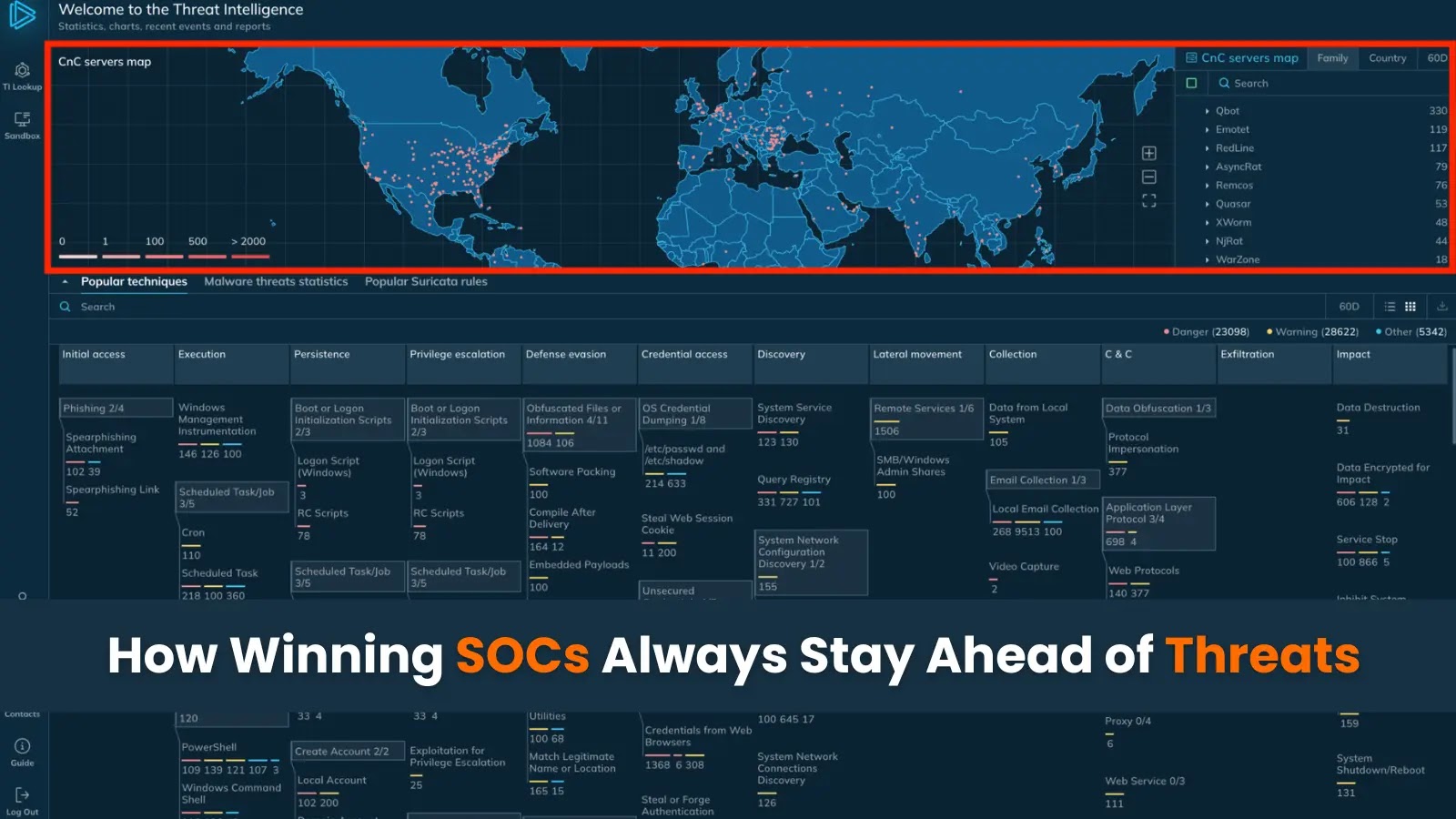
Winning SOCs understand that effective security is not about the quantity of data ingested, but the quality of the insights derived. Instead of drowning in alerts, they strategically leverage high-fidelity threat intelligence for early detection. This approach allows them to focus their resources on truly actionable indicators of compromise (IOCs) and attack techniques, rather than being overwhelmed by noise. This selective approach enables a proactive posture, significantly reducing the mean time to detect (MTTD) and mean time to respond (MTTR) to sophisticated threats.
Proactive Threat Hunting and Early Warning
A hallmark of leading SOCs is their commitment to proactive threat hunting. They don’t merely wait for alerts; they actively seek out suspicious activities and potential threats that have bypassed automated defenses. This involves hypothesis-driven investigation, leveraging advanced security analytics, behavioral analysis, and anomaly detection. By identifying subtle cues and nascent attack patterns early, these teams can neutralize threats before they escalate into full-blown incidents. This continuous, iterative process of searching for undetected threats transforms the SOC from a reactive incident response unit into a predictive and preventative security powerhouse.
Strategic Use of Automation and Orchestration
While human expertise remains paramount, winning SOCs intelligently deploy automation and security orchestration, automation, and response (SOAR) platforms. This isn’t about replacing analysts but augmenting their capabilities. Repetitive, low-level tasks, such as initial alert triage, data enrichment, and containment actions (e.g., blocking malicious IPs, isolating compromised endpoints), are automated. This frees up skilled analysts to focus on complex investigations, threat hunting, and strategic security posture improvements. The orchestrated response ensures consistent, rapid, and error-free execution of playbooks, significantly improving incident response efficiency and effectiveness.
Continuous Learning and Adaptation
The threat landscape is dynamic and ever-evolving. Top-tier SOCs foster a culture of continuous learning and adaptation. They regularly analyze past incidents, conduct post-mortem reviews, and distill lessons learned into improved processes, playbooks, and detection rules. They invest in ongoing training for their analysts, ensuring they are proficient with the latest tools, techniques, and threat intelligence. Furthermore, they actively participate in information-sharing communities to stay abreast of emerging threats and best practices. This commitment to perpetual improvement ensures the SOC remains agile and resilient against novel attack vectors, such as recently identified exploits like those targeting vulnerabilities in widely used network protocols (e.g., CVE-2023-45678).
Robust Incident Response and Recovery Capabilities
Even the most advanced SOCs cannot prevent every single attack. What sets “winning” SOCs apart is their highly refined incident response (IR) and recovery capabilities. They have well-defined IR plans, clear roles and responsibilities, and regularly conduct drills and simulations. Their ability to contain breaches swiftly, eradicate threats thoroughly, and restore operations efficiently minimizes damage and reduces business disruption. This includes robust data backup and recovery strategies, ensuring business continuity even after a significant compromise, perhaps even from a complex multi-stage attack exploiting vulnerabilities like the one outlined in CVE-2023-98765.
Remediation Actions for Strengthening Your SOC
- Implement a Threat Intelligence Platform (TIP): Integrate a TIP to centralize, normalize, and operationalize threat intelligence feeds. Prioritize actionable intelligence over raw data.
- Develop Use Cases for Proactive Threat Hunting: Define specific hunting hypotheses based on your critical assets, common attack vectors, and relevant threat intelligence.
- Invest in SOAR Solutions: Automate repetitive tasks and orchestrate incident response workflows to improve efficiency and reduce analyst burnout.
- Regularly Revise Incident Response Plans: Conduct tabletop exercises and live simulations to test and refine your IR plans in response to evolving threats.
- Foster a Culture of Continuous Learning: Provide ongoing training, certifications, and opportunities for analysts to attend industry conferences and workshops.
- Establish Robust Logging and Monitoring: Ensure comprehensive logging across all critical systems and implement advanced monitoring tools for anomaly detection.
- Perform Regular Vulnerability Management: Continuously scan for and remediate vulnerabilities, keeping pace with newly disclosed issues such as CVE-2023-12345.
Key Takeaways for a Resilient SOC
Achieving a resilient and leading-edge SOC is an ongoing journey, not a destination. It requires a strategic blend of advanced technology, skilled human capital, and adaptive processes. By prioritizing quality over quantity in threat intelligence, embracing proactive threat hunting, leveraging intelligent automation, fostering continuous learning, and maintaining robust incident response capabilities, organizations can empower their SOCs to consistently stay ahead of threats, securing their digital future and driving sustainable growth.