InvisibleJS Tool Hides Executable ES Modules in Empty Files Using Zero-Width Steganography
InvisibleJS: How Invisible Code Hides Dangerous Payloads in Plain Sight
The digital landscape is constantly evolving, with new threats emerging that challenge conventional cybersecurity defenses. One such innovative, yet alarming, development is InvisibleJS, an open-source tool that employs zero-width steganography to conceal executable ES modules within seemingly empty JavaScript files. This technique presents a significant challenge for traditional security tools and human analysis, raising serious concerns about its potential misuse in sophisticated malware campaigns.
This blog post delves into the mechanics of InvisibleJS, its implications for cybersecurity, and crucial remediation strategies for IT professionals, security analysts, and developers.
Understanding InvisibleJS: Zero-Width Steganography Explained
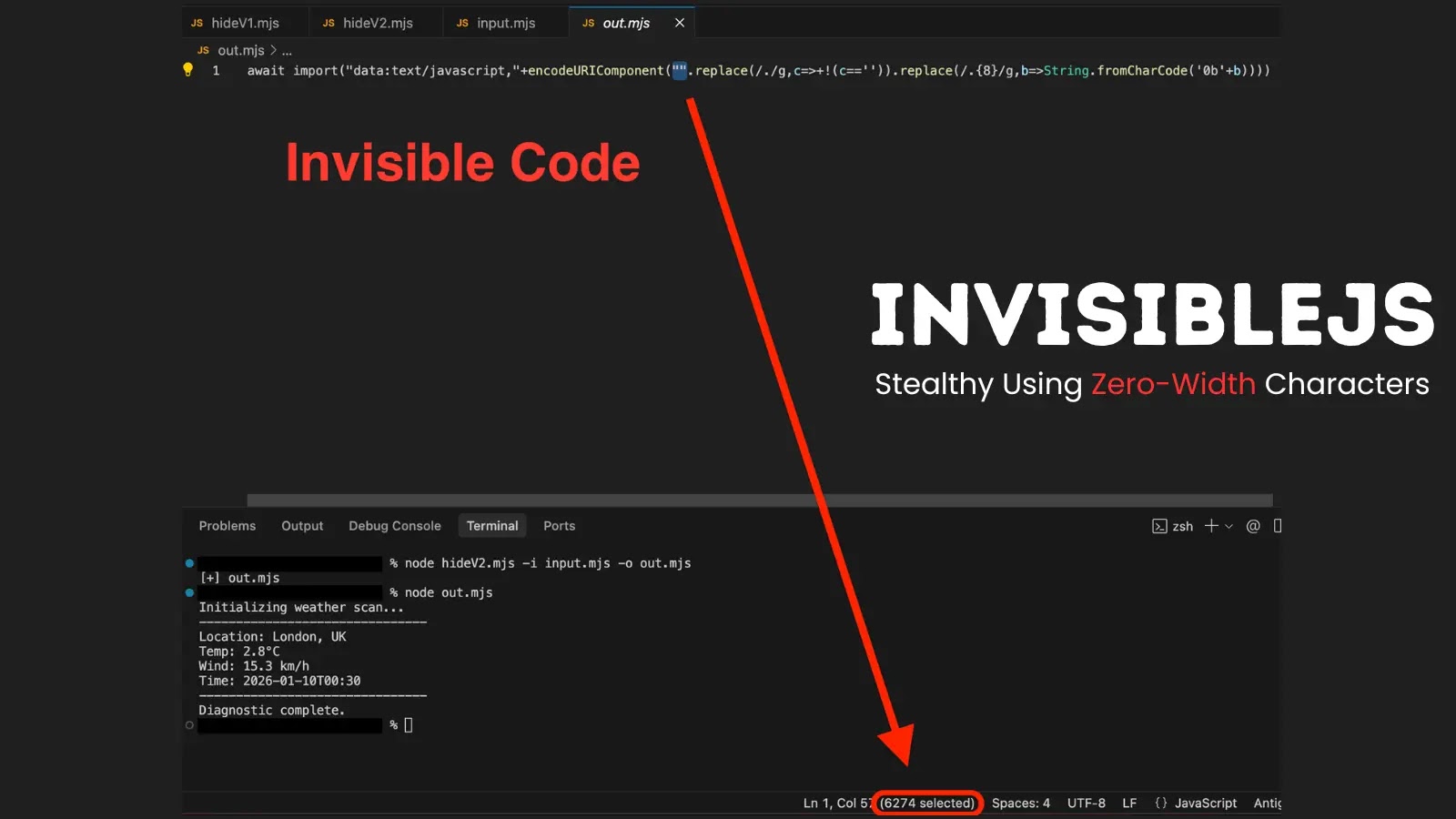
InvisibleJS, developed by the individual known as “oscarmine” and hosted on GitHub, leverages a clever application of steganography. Traditionally, steganography involves hiding information within innocuous carriers like images or audio files. InvisibleJS applies this principle to JavaScript code itself, utilizing zero-width Unicode characters to make the hidden code virtually undetectable without specialized tools.
The core mechanism involves converting legitimate JavaScript code into binary strings. Each ‘0’ in the binary string is then mapped to a specific zero-width Unicode character: a Zero Width Space (U+200B). These characters are non-printing; they occupy no discernible space and are invisible to the naked eye in most text editors and development environments. The result is a JavaScript file that appears blank or contains only innocuous whitespace, yet secretly harbors executable code.
For a deeper dive into the tool, you can explore the original source material at Cybersecurity News’s report on InvisibleJS.
The Stealthy Threat: How InvisibleJS Bypasses Detection
The danger posed by InvisibleJS lies in its ability to evade conventional security measures. Here’s why this technique is particularly insidious:
- Visual Obfuscation: As the name suggests, the hidden code is invisible. Developers and security analysts inspecting files will see seemingly empty or whitespace-filled lines, completely unaware of the embedded payload.
- Signature-Based Evasion: Traditional antivirus and intrusion detection systems (IDS) often rely on signature matching to identify known malware. Since InvisibleJS doesn’t directly alter the visible syntax of the JavaScript, it can bypass these signature-based detections. The visible file might appear benign.
- Behavioral Analysis Challenges: While advanced behavioral analysis tools might eventually detect malicious execution, the initial infection vector and code injection remain hidden, making attribution and prevention more difficult.
- Supply Chain Attacks: InvisibleJS could be leveraged in supply chain attacks, where seemingly harmless dependencies or open-source libraries could secretly contain malicious code, activated only under specific conditions.
Potential Misuse and Real-World Scenarios
The capabilities of InvisibleJS open the door to various malicious applications:
- Malware Delivery: Attackers could embed malicious JavaScript into legitimate-looking files, delivering payloads that execute silently on user systems. This could range from keyloggers to ransomware or remote access Trojans (RATs).
- Web Skimming: Malicious scripts used for web skimming (credit card theft) could be hidden within website code, making them harder to detect by website administrators and security scanners.
- Backdoors: Threat actors might embed backdoor access code into compromised systems, maintaining persistent access without leaving obvious traces in code files.
- Social Engineering: Phishing campaigns could distribute seemingly empty JavaScript files, purporting to be innocuous scripts, which in reality contain hidden malicious code.
Remediation Actions and Detection Strategies
Given the stealthy nature of InvisibleJS, a multi-layered approach is essential for detection and mitigation. Proactive measures are critical to protect against this sophisticated form of code obfuscation.
- Employ Static Application Security Testing (SAST) with Unicode Awareness: Utilize SAST tools that can specifically identify and analyze zero-width Unicode characters. These tools should be capable of de-obfuscating such characters to reveal hidden code.
- Enhanced Code Review Practices: Implement stringent code review processes. While manual review might struggle with zero-width characters, integrating automated tools that highlight non-standard Unicode or suspicious whitespace patterns can significantly help.
- Dynamic Application Security Testing (DAST): Leverage DAST tools to analyze the runtime behavior of JavaScript code. Even if code is hidden, its execution will likely reveal suspicious activities.
- Regular Dependency Scanning: For developers, regularly scan all project dependencies for vulnerabilities and unexpected code. Tools that check for changes in file hashes or unexpected character encodings can be beneficial.
- Endpoint Detection and Response (EDR) Systems: Ensure robust EDR systems are in place to monitor process execution, file modifications, and network communications on endpoints. Anomalous activity after a script execution could indicate a hidden payload.
- Content Security Policy (CSP): Implement strict Content Security Policies on web applications to limit the sources from which scripts can be loaded and executed, reducing the attack surface.
- Developer Education: Educate developers about the risks of zero-width steganography and best practices for secure coding, including vigilance against unusual whitespace or non-standard characters in codebases.
Tools for Detection and Analysis
Several types of tools can assist in detecting hidden code utilizing zero-width characters:
| Tool Name | Purpose | Link |
|---|---|---|
| Unicode Inspectors/Viewers | Identifies and displays all Unicode characters, including zero-width ones. | Graphemica |
| Advanced SAST Solutions | Scans source code for potential vulnerabilities, including obfuscation techniques and unusual character usage. | (Varies by vendor – inquire about zero-width character detection) |
| Hex Editors | Allows raw viewing of file contents, which can reveal bytes representing zero-width characters. | HexEd.it |
| Custom Scripting | Scripts (e.g., Python) can be written to scan files for specific Unicode ranges associated with zero-width characters. | (Refer to Python’s unicodedata module documentation) |
Conclusion: Staying Ahead of Invisible Threats
InvisibleJS represents a sophisticated evolution in code obfuscation, underscoring the constant need for vigilance and adaptation in cybersecurity. The ability to hide executable code within seemingly benign files bypasses many conventional security assumptions. For IT professionals, security analysts, and developers, recognizing this technique and implementing robust detection and prevention strategies is paramount. By combining advanced static and dynamic analysis, diligent code review, and comprehensive endpoint security, organizations can bolster their defenses against these increasingly invisible threats and secure their digital assets.





