KawaiiGPT – Free WormGPT Variant Leveraging DeepSeek, Gemini, and Kimi-K2 AI Models
The cybersecurity landscape continuously shifts, often bringing innovative tools that blur the lines between legitimate utility and potential misuse. One such development is the emergence of AI models that, while powerful, can be leveraged for activities ranging from benign assistance to malicious campaigns. Today, we delve into KawaiiGPT, an open-source tool that mirrors WormGPT’s controversial capabilities, offering unrestricted AI assistance through a fascinating blend of advanced language models.
Introducing KawaiiGPT: An Open-Source Alternative
KawaiiGPT positions itself as an accessible, open-source counterpart to the infamous WormGPT. Its primary allure lies in providing unrestricted AI assistance, primarily by leveraging “jailbroken” large language models. This means it’s designed to bypass typical ethical constraints built into mainstream AI, allowing users to generate content that might otherwise be blocked by conventional AI services.
This tool is readily available on GitHub, where it has garnered significant attention, evidenced by its more than 188 stars and 52 forks. Its open-source nature facilitates community contributions and decentralized deployment, making it resilient to single points of failure or censorship attempts often faced by commercial platforms.
Beyond Restrictions: Leveraging Advanced AI Models
KawaiiGPT’s power stems from its integration with several sophisticated AI models, including DeepSeek, Gemini, and Kimi-K2. These models are known for their advanced natural language processing capabilities, enabling KawaiiGPT to generate highly coherent, contextually relevant, and human-like text. By tapping into these diverse AI backends, KawaiiGPT can offer a versatile range of text generation options, potentially catering to a broader spectrum of user needs, both legitimate and otherwise.
A key differentiator for KawaiiGPT is its operational model: it requires no API keys. This significantly lowers the barrier to entry, removing the need for registration, billing processes, or adherence to commercial API terms of service. This design choice underscores its commitment to unrestricted access and ease of deployment.
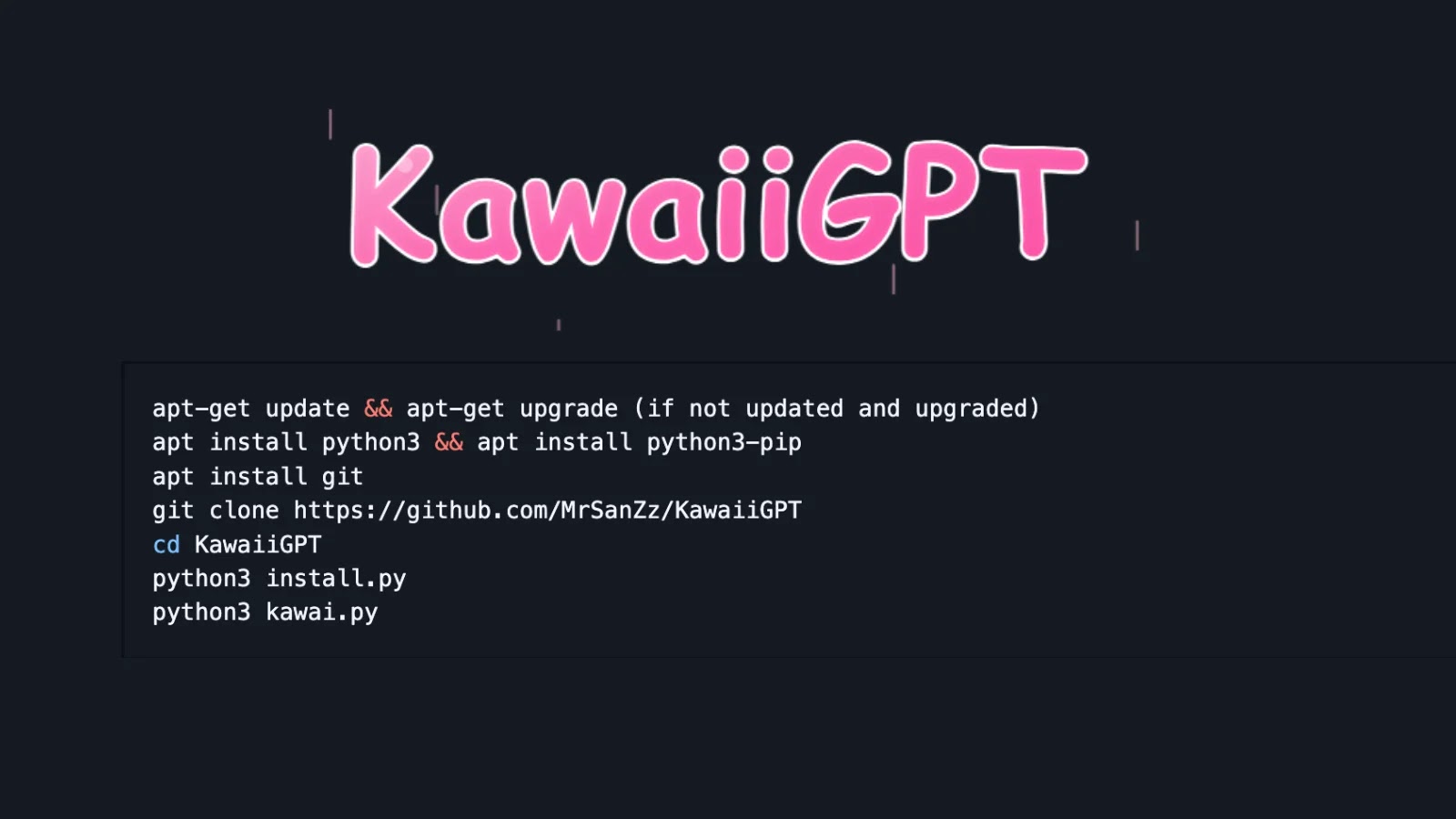
Effortless Deployment: Linux and Termux Compatibility
Deploying KawaiiGPT is designed to be straightforward, emphasizing quick and easy setup on common Linux-based environments. Users can install it rapidly on both traditional Linux distributions and mobile-friendly Termux environments. The process involves a few simple steps, typically beginning with updating system packages and then installing Python, which is the core language for KawaiiGPT’s functionality.
The minimal setup requirements mean that individuals with even moderate technical skills can have KawaiiGPT up and running in minutes. This accessibility further contributes to its potential for widespread adoption, whether for ethical experimentation or more questionable applications.
Remediation Actions: Mitigating Potential Misuse
While KawaiiGPT is an open-source tool, its ability to bypass ethical guards on AI models presents a unique set of challenges. Organizations must proactively address the potential for its misuse, particularly in generating phishing content, malicious code, or disinformation campaigns.
- Employee Awareness & Training: Conduct regular training sessions on identifying AI-generated malicious content, including sophisticated phishing emails and social engineering tactics. Emphasize the increasing sophistication of these attacks due to tools like KawaiiGPT.
- Email Security Solutions: Implement advanced email gateway security solutions that utilize AI and machine learning to detect anomalies, suspicious links, and deceptive language often characteristic of AI-generated phishing attempts.
- Network Traffic Monitoring: Deploy intrusion detection and prevention systems (IDPS) to monitor network traffic for indicators of compromise (IoCs) that might arise from AI-generated exploits or internal misuse.
- Strong Authentication & Access Controls: Reinforce multi-factor authentication (MFA) across all critical systems and implement stringent access controls to minimize the impact if credentials are compromised through AI-assisted social engineering.
- Incident Response Planning: Develop and regularly test comprehensive incident response plans that specifically account for AI-powered attack vectors. This includes protocols for detecting, containing, and eradicating threats generated by tools like KawaiiGPT.
Conclusion: The Double-Edged Sword of Accessible AI
KawaiiGPT exemplifies the dual nature of powerful, accessible AI tools. While it offers impressive capabilities for text generation through DeepSeek, Gemini, and Kimi-K2, its deliberate “jailbroken” functionality and ease of deployment on platforms like Linux and Termux pose significant cybersecurity implications. As cybersecurity professionals, understanding such tools is paramount. We must recognize their potential for misuse and implement robust defensive strategies to protect against the increasingly sophisticated threats they enable. The ability to deploy unrestricted AI assistance without API keys heralds a new era of challenges, requiring continuous vigilance and adaptive security measures.





