Lessons Learned From Massive npm Supply Chain Attack Using “Shai-Hulud” Self-Replicating Malware
Unveiling Shai-Hulud: The npm Supply Chain Nightmare of 2025
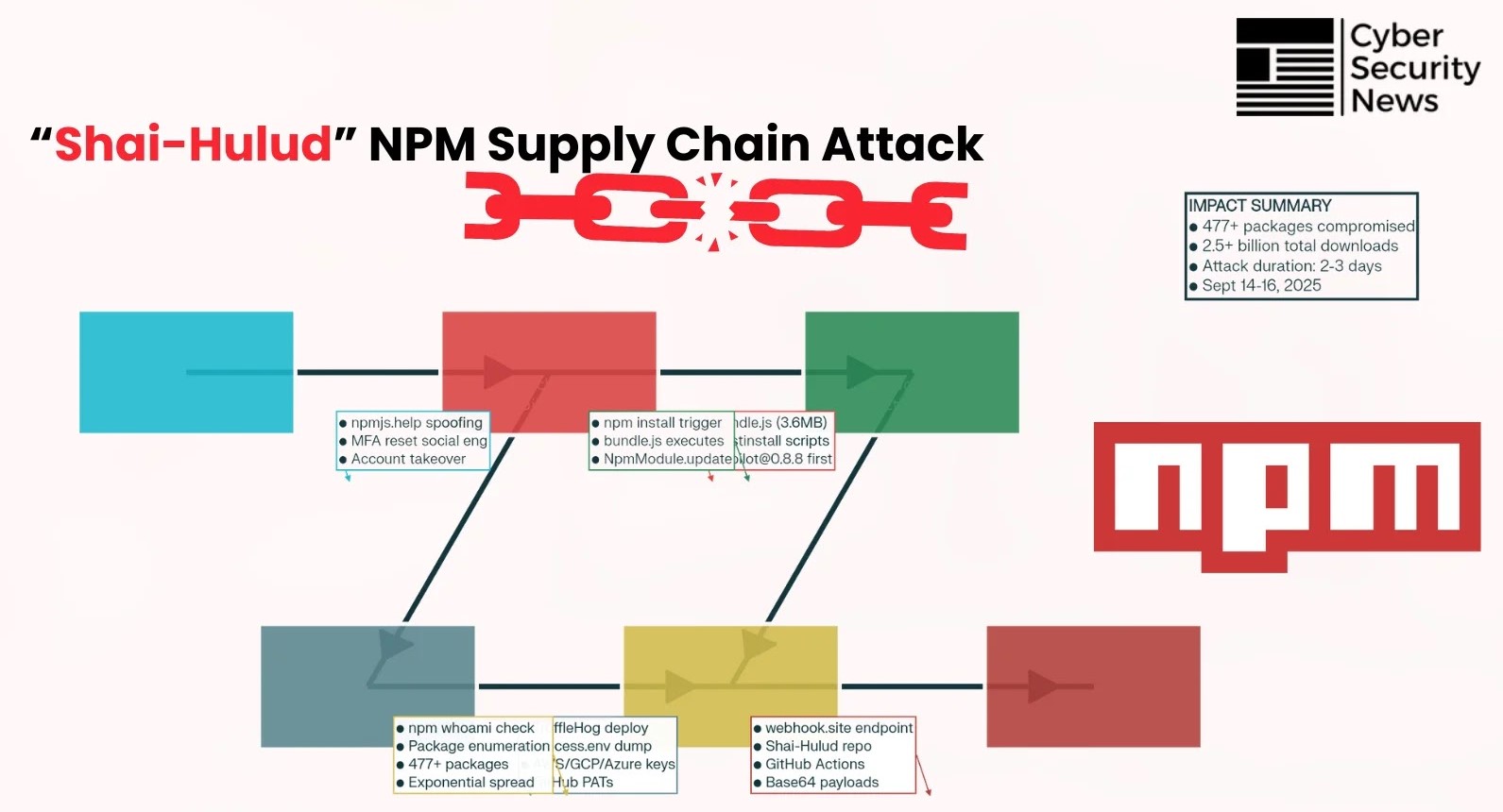
The digital landscape witnessed a seismic shift in September 2025, as the JavaScript ecosystem was rocked by an unprecedented supply chain attack. A novel, self-replicating worm, ominously dubbed “Shai-Hulud,” breached over 477 npm packages, marking a grim first: the successful automated propagation of malware within the npm registry. This wasn’t merely another vulnerability; it represented a sophisticated evolution in supply chain threats, blending cunning social engineering with advanced automation. For developers, security analysts, and IT professionals, understanding the mechanics and implications of Shai-Hulud is no longer a choice—it’s an imperative for safeguarding our technological infrastructure.
The Anatomy of an Evolving Threat: How Shai-Hulud Operated
Shai-Hulud distinguished itself by its self-replicating nature, a capability previously unseen at this scale within the npm registry. The attack wasn’t a static compromise but a living, breathing entity that evolved and spread autonomously. While specific technical details of its propagation mechanism are still being fully dissected, initial reports suggest a multi-pronged approach that likely included:
- Automated Credential Harvesting: Compromised developer accounts likely served as initial entry points, with Shai-Hulud potentially leveraging stolen credentials to publish malicious updates or new packages.
- Ingenious Social Engineering: Human element exploitation almost certainly played a role in gaining initial access or distributing early, seemingly innocuous malicious packages. This could range from phishing campaigns targeting developers to subtle trickery embedded within package documentation.
- Exploiting npm’s Interdependencies: The worm’s effectiveness stemmed from its ability to exploit the intricate web of dependencies within the npm ecosystem. Once a package was infected, its dependents would, in turn, become vulnerable upon updating or new installations.
- Self-Replication Mechanism: The core innovation was Shai-Hulud’s ability to automatically identify, infect, and publish malicious code to new packages within the npm registry, without direct human intervention after the initial seeding. This automation magnified its destructive potential exponentially.
Why Shai-Hulud Represents a New Era in Supply Chain Attacks
The Shai-Hulud incident transcends typical supply chain compromises. Its automated propagation sets a dangerous precedent, demonstrating a shift from targeted attacks to expansive, self-sustaining malware campaigns. This elevates the risk profile significantly because:
- Speed of Propagation: Automated replication means malware can spread far faster than manual detection and mitigation efforts can keep pace.
- Scale of Impact: Hundreds of packages were compromised, indicating the potential for a single sophisticated actor to impact a vast segment of the software supply chain.
- Detection Challenges: Self-replicating malware can adapt and mutate, making signature-based detection less effective over time. Behavioral analysis becomes paramount.
- Erosion of Trust: Such attacks fundamentally undermine trust in public package registries, forcing a re-evaluation of current security models and trust assumptions.
Remediation Actions: Fortifying Your Defenses Against Future Threats
Preventing another Shai-Hulud requires a multi-layered, proactive defense strategy. Organizations and individual developers must adopt a rigorous approach to software supply chain security.
- Implement Strict Access Controls and MFA: Enforce multi-factor authentication (MFA) for all developer accounts on npm and other package registries. Regularly review and revoke unnecessary access permissions.
- Automated Dependency Scanning: Integrate tools that continuously scan for known and unknown vulnerabilities in your project dependencies. This includes software composition analysis (SCA) tools that can detect malicious packages or compromised versions.
- Supply Chain Trust Verification: Move towards verifying the integrity and authenticity of packages directly. Consider using package signing where available and implement robust artifact verification processes.
- Security-Focused Development Practices: Foster a security-first culture. Educate developers on social engineering tactics, secure coding practices, and the risks associated with blindly trusting third-party packages.
- Principle of Least Privilege: Ensure that build systems and deployment pipelines operate with the absolute minimum necessary permissions.
- Regular Audits and Monitoring: Continuously monitor your dependencies for unusual activity, new vulnerabilities, or unexpected changes. Implement logging and alerting for critical supply chain events.
Tools for Enhanced Supply Chain Security
| Tool Name | Purpose | Link |
|---|---|---|
| Snyk | SCA and SAST, dependency vulnerability scanning | https://snyk.io/ |
| OWASP Dependency-Check | Identifies project dependencies and checks for known vulnerabilities | https://owasp.org/www-project-dependency-check/ |
| GitHub Dependabot | Automated dependency updates and vulnerability alerts | https://github.com/features/security/dependabot |
| Veracode SCA | Software Composition Analysis for third-party libraries | https://www.veracode.com/products/software-composition-analysis |
| JFrog Xray | Universal software supply chain security and dependency analysis | https://jfrog.com/xray/ |
Key Takeaways from the Shai-Hulud npm Attack
The Shai-Hulud incident in September 2025 serves as a stark reminder that the battle for cybersecurity is constantly evolving. The advent of self-replicating malware within a public package registry signals a critical inflection point. Organizations must move beyond reactionary security measures and embrace a proactive, comprehensive approach to supply chain integrity. This means stringent access controls, continuous vulnerability scanning, and fostering a deep understanding among development teams of the inherent risks associated with third-party dependencies. The lessons learned from Shai-Hulud are clear: vigilance, automation, and a strong security posture are non-negotiable for anyone operating in the modern software development landscape.





