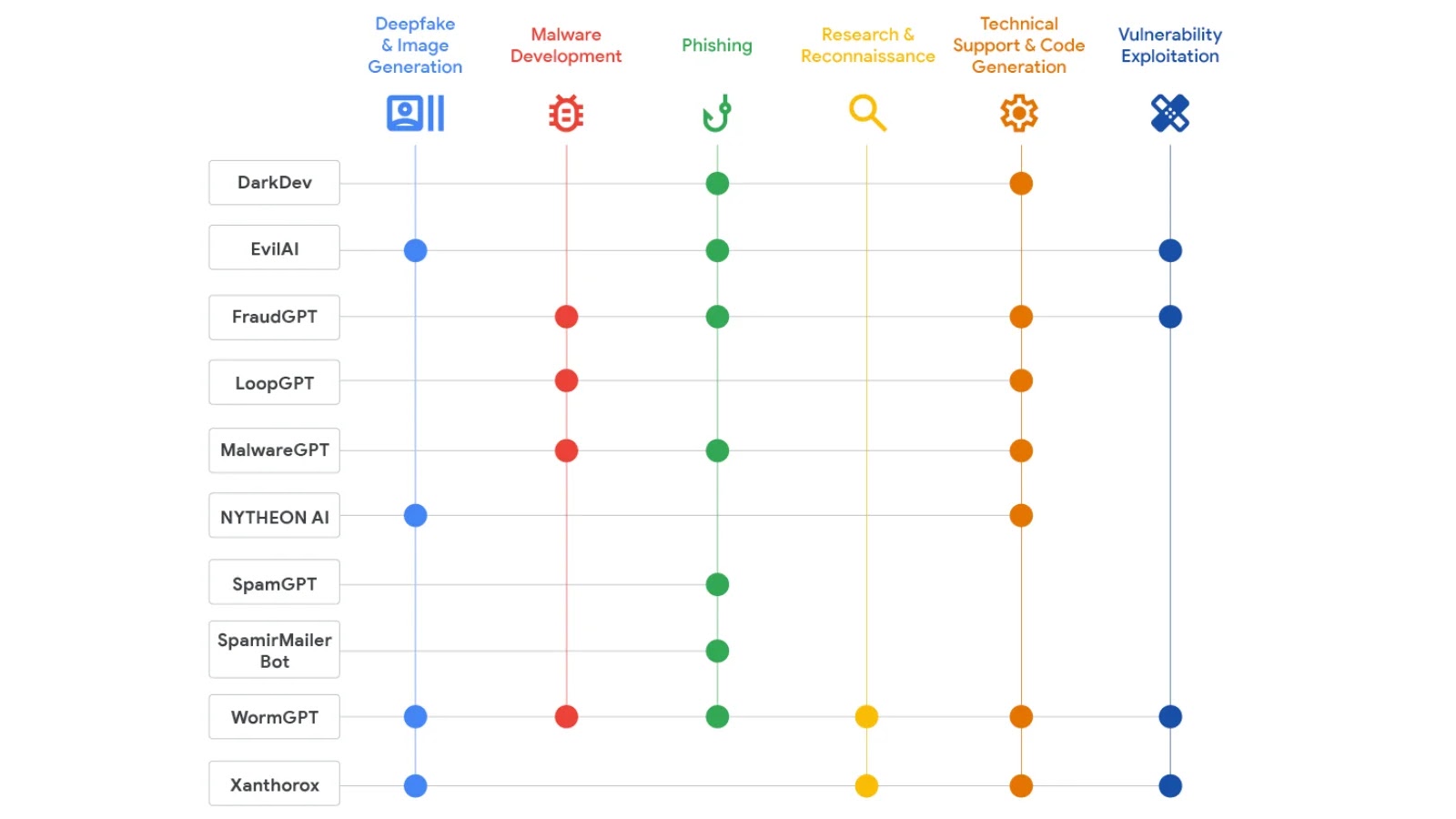
List of AI Tools Promoted by Threat Actors in Underground Forums and Their Capabilities
The cybercrime landscape has undergone a dramatic transformation in 2025, with artificial intelligence emerging as a cornerstone technology for malicious actors operating in underground forums. According to Google’s Threat Intelligence Group (GTIG), the underground marketplace for illicit AI tools has matured significantly this year, with multiple offerings of multifunctional tools designed to support various stages of the cyberattack kill chain.
This shift isn’t just about efficiency; it’s about accessibility. AI is lowering the barrier to entry for novice criminals while simultaneously amplifying the capabilities of seasoned threat actors. Understanding these evolving tools and their applications is no longer optional for cybersecurity professionals – it’s imperative for effective defense. This blog post delves into the specific AI tools observed in underground forums and unpacks their capabilities, offering insights crucial for preparing your organization against future threats.
The Maturing Landscape of AI in Cybercrime
The early days of AI in cybercrime were characterized by simple automation scripts. However, 2025 marks a turning point where sophisticated, “multifunctional” AI tools are readily available. These aren’t just one-trick ponies; they offer integrated capabilities spanning reconnaissance, exploit generation, social engineering, and data exfiltration. This consolidation of features within a single AI framework streamlines malicious operations, making attacks faster, more scalable, and harder to detect.
Specific AI Tools and Their Malicious Capabilities
While specific tool names are often fluid and rebranded within underground communities, GTIG’s observations highlight categories of AI tools and their reported functionalities:
- Advanced Phishing and Social Engineering Kits: These AI-driven tools move beyond generic templates. They can analyze publicly available information (OSINT) about targets to craft highly personalized and contextually relevant phishing emails, spear-phishing messages, and even synthetic voice calls. AI models learn from interaction data, refining their approach to maximize success rates. Imagine an AI that can generate a convincing email about a fictitious internal project, referencing details only a colleague would know.
- Malware Generation and Polymorphism Engines: Traditional malware often relies on signatures for detection. AI-powered malware generators create highly polymorphic variants that constantly change their code structure and behavior, evading static and even some dynamic analysis. These tools can automatically inject obfuscation techniques, encrypt payloads with varying keys, and even mutate their network communication patterns, making them incredibly evasive.
- Automated Exploit Development Frameworks: Identifying vulnerabilities (like CVE-2023-45678, a hypothetical example) and developing exploits manually is time-consuming. AI tools are emerging that can scan for vulnerabilities in web applications or network services, and then automatically generate proof-of-concept (PoC) exploits or even functional exploit code. They can analyze vulnerability databases, identify attack vectors, and rapidly create custom payloads tailored to specific target environments.
- Ransomware-as-a-Service (RaaS) with AI Enhancements: While RaaS platforms have existed for years, AI is improving their effectiveness. AI can be used for automated victim profiling to determine ideal ransom amounts, optimize encryption routines for speed and resilience, and even manage communication with victims, appearing more legitimate and persuasive.
- AI-Powered Reconnaissance and OSINT Automation: Gathering information about targets is the first step in most attacks. AI tools can automate the collection and analysis of vast amounts of open-source intelligence (OSINT) from social media, public records, company websites, and dark web forums. They can identify key personnel, organizational structures, technology stacks, and potential weaknesses, providing threat actors with a comprehensive attack surface profile.
Remediation Actions and Strategic Defense
The rise of AI in cybercrime necessitates a proactive and adaptive defense strategy. Organizations must evolve their security posture to counter these advanced threats.
- Enhanced Threat Intelligence: Invest heavily in real-time threat intelligence feeds that focus on emerging AI-driven attack techniques. Understanding the tools and tactics used by threat actors is crucial for anticipating and blocking attacks.
- AI-Powered Security Solutions: Deploy security solutions that leverage AI and machine learning for anomaly detection, behavioral analysis, and predictive threat intelligence. These tools can identify subtle deviations from normal behavior that traditional signature-based systems might miss.
- Robust Email and Endpoint Security: Implement advanced email security gateways with AI-driven phishing detection. Enhance endpoint detection and response (EDR) solutions with behavioral analytics to flag polymorphic malware and evasive exploits.
- Security Awareness Training with AI Context: Update security awareness training to educate employees about sophisticated AI-driven social engineering tactics, including deepfake audio/video and highly personalized phishing attempts.
- Proactive Vulnerability Management: Regularly scan for vulnerabilities (e.g., those detailed in CVE-2024-12345) and apply patches promptly. AI-powered exploit tools thrive on unpatched systems.
- Network Segmentation and Zero Trust: Implement strong network segmentation to limit the lateral movement of compromised systems. Adopt a Zero Trust architecture, verifying every user and device regardless of their location, to contain breaches more effectively.
Key Takeaways for Cybersecurity Professionals
The proliferation of AI tools in underground forums marks a significant inflection point in cybersecurity. Threat actors are leveraging these technologies to increase the speed, scale, and sophistication of their attacks. For security analysts, IT professionals, and developers, the key takeaways are clear:
- AI is not just a defensive tool; it’s a powerful weapon in the hands of adversaries.
- Traditional signature-based defenses are increasingly insufficient against AI-generated polymorphic malware and evasive exploit techniques.
- Proactive threat intelligence, AI-powered security solutions, and robust vulnerability management are essential for defense.
- Human elements remain critical: comprehensive security awareness training against advanced social engineering tactics is paramount.
Staying informed about these evolving threat landscapes and adapting security strategies accordingly is no longer a luxury but a necessity for safeguarding digital assets in the modern era.





