Malicious Go Packages Mimic as Google’s UUID Library to Exfiltrate Sensitive Data
The Silent Threat: Malicious Go Packages Mimicking Google’s UUID Library
In the vast landscape of software development, the efficiency and reusability offered by open-source libraries are invaluable. However, this convenience comes with inherent risks, particularly when malicious actors exploit trust for nefarious purposes. Recently, security researchers uncovered a cunning supply chain attack directly targeting the Go programming community. This long-running scheme leveraged sophisticated typosquatting to distribute malicious Go packages, silently exfiltrating sensitive data from unsuspecting developers for years. This article delves into the details of this insidious threat, how it operates, and crucial steps to mitigate such risks.
Understanding the Typosquatting Attack on Go Developers
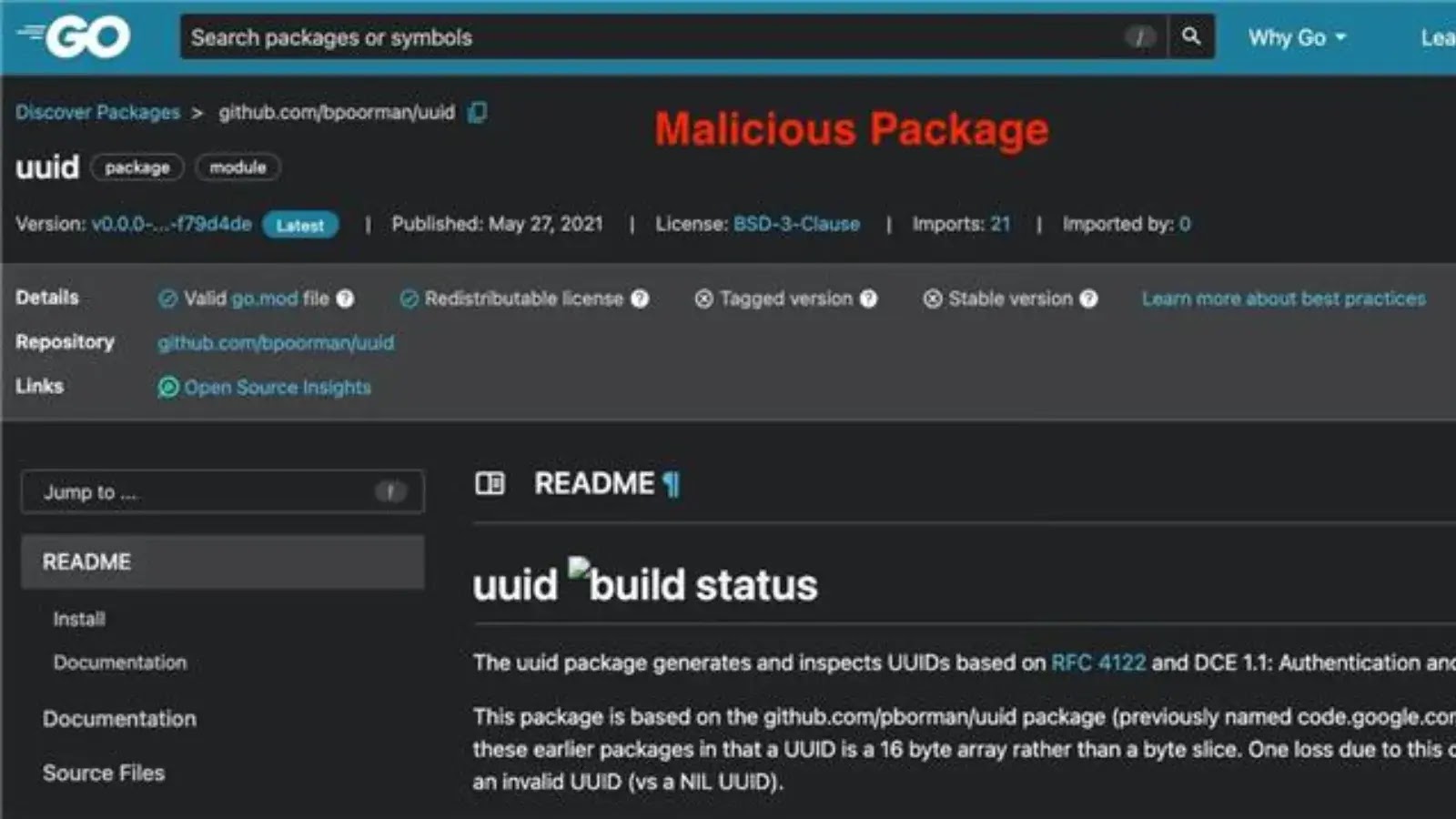
The Socket Threat Research Team brought to light two deceptive Go packages: github.com/bpoorman/uuid and github.com/bpoorman/uid. These packages were meticulously crafted to mimic the legitimate and widely used Google UUID library, a common component for generating universally unique identifiers. The malicious actors relied on a classic but effective technique known as typosquatting, where they registered package names that are visually similar to their legitimate counterparts. Developers, often working under pressure or making minor typographical errors, could easily integrate these fake packages into their projects without realizing the underlying danger.
The sophistication of this attack lies in its subtlety and persistence. For years, these malicious packages remained undetected, integrated into various projects, acting as silent conduits for data theft. This highlights a critical vulnerability in software supply chains where the distinction between a trusted and a malicious component can be as thin as a single character in a package name.
How Malicious Go Packages Exfiltrate Data
While the specific details of the data exfiltration mechanism were not fully elaborated in the initial report, the primary goal of such attacks is typically to harvest sensitive information. This could include:
- API Keys and Credentials: Access tokens, API keys, and other authentication details vital for accessing services and data.
- Source Code: Proprietary or sensitive source code from private repositories.
- Environment Variables: Configuration settings and sensitive data stored as environment variables.
- Build Artifacts: Information about the build environment, dependencies, and deployed systems.
- Private Data: Any other potentially valuable information residing in the developer’s environment or accessible through the compromised application.
The malicious code embedded within these fake UUID packages would likely be designed to identify and extract this sensitive data and transmit it to an attacker-controlled server. This often occurs subtly in the background, making it extremely difficult for developers to notice the breach without specialized tooling or vigilant security practices.
The Broader Impact of Supply Chain Attacks
This incident serves as a stark reminder of the escalating threat of supply chain attacks. When developers inadvertently incorporate compromised libraries, the malicious code propagates through their projects, ultimately impacting end-users or target systems. The implications are far-reaching, encompassing:
- Data Breaches: Exposure of sensitive personal or organizational data.
- Financial Losses: Costs associated with incident response, reputational damage, and regulatory fines.
- System Compromise: Backdoors or other vulnerabilities introduced into production systems.
- Intellectual Property Theft: Loss of proprietary algorithms, designs, or business logic.
Remediation Actions and Best Practices for Go Developers
Protecting against sophisticated typosquatting and other supply chain attacks requires a multi-layered approach. Go developers and organizations must adopt stringent security measures:
- Verify Package Sources: Always verify the authenticity of Go packages before integration. Prioritize official repositories and well-known, trusted maintainers. Look for canonical links and strong community support.
- Examine Package Names Carefully: Pay close attention to package names, especially when performing a
go getor importing libraries. Even a single character difference can indicate a malicious imitation. - Use Dependency Management Tools: Leverage tools that provide dependency analysis, such as pkg.go.dev for Go packages, to check for known vulnerabilities and ensure the use of legitimate versions.
- Implement Software Composition Analysis (SCA): Integrate SCA tools into your CI/CD pipeline. These tools can automatically scan dependencies for known security flaws (CVEs) and suspicious patterns. For example, a tool might flag a UUID library attempting network communication, which would be highly unusual behavior. While specific CVEs for these packages are not yet widely published, ongoing monitoring by SCA tools is crucial for identifying new threats.
- Principle of Least Privilege: Ensure that build environments and development machines operate with the minimum necessary permissions to reduce the impact of a potential compromise.
- Regular Security Audits: Conduct periodic security audits of your codebase and build processes to identify and rectify vulnerabilities proactively.
- Stay Informed: Keep abreast of the latest cybersecurity threats and best practices. Follow security news outlets, maintain subscriptions to relevant security bulletins, and participate in developer security communities.
Recommended Tools for Supply Chain Security
To aid in detecting and mitigating such threats, a robust set of tools can be invaluable:
| Tool Name | Purpose | Link |
|---|---|---|
| Socket Security | Detects supply chain attacks by analyzing package behavior. | https://socket.dev/ |
| OWASP Dependency-Track | Software Composition Analysis (SCA) platform for identifying and managing vulnerabilities in open-source dependencies. | https://dependencytrack.org/ |
| Snyk | Developer-first security platform for finding and fixing vulnerabilities in dependencies, code, and containers. | https://snyk.io/ |
| Go Vulnerability Database (govulncheck) |
Official Go tool for checking your dependencies for known vulnerabilities. | https://pkg.go.dev/golang.org/x/vuln/cmd/govulncheck |
| Sourcegraph Code Intelligence | Provides code navigation and understanding, which can help in examining imported packages. | https://sourcegraph.com/ |
Conclusion
The discovery of malicious Go packages masquerading as Google’s UUID library underscores a persistent challenge in software development: maintaining trust in the open-source ecosystem. The silent exfiltration of sensitive data through typosquatting highlights the need for developers to adopt meticulous verification practices and robust security tooling. By prioritizing supply chain security, validating package sources, and integrating automated scanning, the Go community can collectively build a more secure foundation for innovation.





