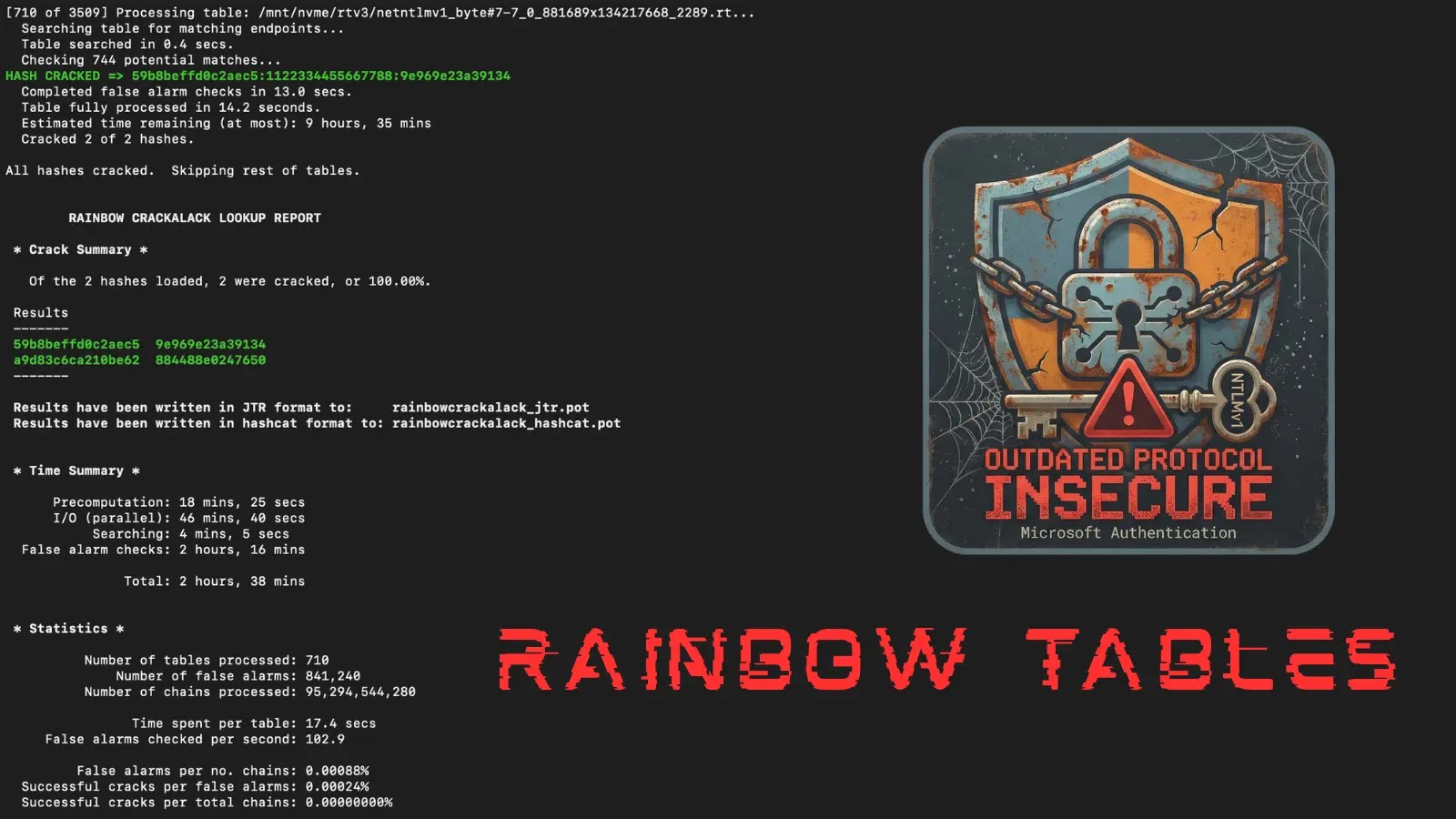
Mandiant Releases Rainbow Tables Enabling NTLMv1 Admin Password Hacking
The cybersecurity landscape has just received a stark reminder of the persistent dangers posed by legacy protocols. Google-owned Mandiant, a titan in the threat intelligence sphere, has just made a significant move that amplifies this concern: the public release of a comprehensive dataset of Net-NTLMv1 rainbow tables. This isn’t merely an academic exercise; it’s a dramatic demonstration of how readily outdated authentication mechanisms can be exploited, putting countless organizations at heightened risk.
For security professionals, this development serves as an urgent call to action, demanding immediate attention to systems still reliant on Net-NTLMv1. The message is clear: migrate away from this deeply flawed protocol now, or face potentially catastrophic consequences.
Understanding Net-NTLMv1 and its Cryptographic Weakness
Net-NTLMv1 is an authentication protocol that has been cryptographically broken for well over two decades. Its fundamental design flaws make it highly susceptible to offline brute-force attacks, particularly when using pre-computed rainbow tables. Instead of transmitting a user’s password directly, NTLMv1 sends a hash of the password across the network. However, the way this hash is constructed and challenged allows attackers to capture it and then use tools, like rainbow tables, to reverse-engineer the original password.
The key issue lies in its weak cryptographic properties. Specifically, it uses a relatively simple challenge-response mechanism that, when combined with weak hashing algorithms (like LM hash and NTLMv1 hash), makes it trivial to crack with sufficient computational resources and, crucially, pre-computed tables.
The Impact of Mandiant’s Rainbow Table Release
Mandiant’s release changes the game by democratizing access to the tools needed for exploitation. While the cryptographic weaknesses of Net-NTLMv1 have been known since 1999, the practical barrier to entry for attackers often involved significant computational effort to generate these rainbow tables. By making a comprehensive dataset publicly available, Mandiant has effectively lowered that barrier to near zero.
This means that:
- Less sophisticated attackers can now leverage these tables to crack Net-NTLMv1 hashes more easily and quickly.
- The time required for an attacker to compromise a system using this protocol has been drastically reduced.
- Organizations still running Net-NTLMv1 are now at an elevated and immediate risk of having administrative credentials compromised.
The intention behind Mandiant’s release is not to aid malicious actors, but rather to forcefully underscore the urgency of migrating away from this protocol. It’s a calculated move to push organizations that have perhaps procrastinated on this issue into immediate action.
Remediation Actions: Phasing Out Net-NTLMv1
The time for deliberation is over; immediate action is required to mitigate the risks associated with Net-NTLMv1. Here are critical steps organizations must take:
- Disable Net-NTLMv1 Immediately: Configure all systems, especially domain controllers and critical servers, to disable Net-NTLMv1. Prioritize NTLMv2 or, ideally, Kerberos for all authentication. This can often be done via Group Policy settings in Windows environments (e.g., “Network security: LAN Manager authentication level”).
- Audit Authentication Protocols: Conduct a thorough audit of your network to identify any systems or applications still relying on Net-NTLMv1. Tools and logs can help pinpoint where this legacy protocol is still in use.
- Implement Stronger Authentication: Migrate to more secure authentication protocols like NTLMv2 (a significant improvement over v1, though still not as robust as Kerberos) or, preferably, Kerberos. For cloud services and external access, leverage modern authentication standards like OAuth 2.0 and OpenID Connect.
- Enforce Multi-Factor Authentication (MFA): Even with stronger protocols, MFA adds a crucial layer of security, making it exponentially harder for attackers to leverage compromised credentials.
- Educate and Train: Ensure IT staff and security teams are aware of the risks associated with legacy protocols and the importance of secure configuration practices.
- Monitor for Exploitation Attempts: Keep a close eye on authentication logs for suspicious activity, repeated failed login attempts, or unusual access patterns.
Relevant Tools for Detection and Mitigation
Effectively addressing the Net-NTLMv1 vulnerability requires the right tools for discovery, analysis, and enforcement. Here’s a selection of useful utilities:
| Tool Name | Purpose | Link |
|---|---|---|
| Nmap | Network discovery and security auditing tool. Can be used with Nmap scripts (NSE) to detect NTLMv1 services. | https://nmap.org/ |
| Responder | LLMNR, NBT-NS, and mDNS poisoner. It will also act as an HTTP/SMB/MSSQL/FTP/LDAP rogue authentication server, returning NTLMv1/NTLMv2 challenges. Useful for detecting vulnerable clients. | https://github.com/lgandx/Responder |
| Kerberoasting tools (e.g., Rubeus, Impacket) | While primarily for Kerberos attacks, they can help identify weaker service principal names (SPNs) that might implicitly hint at older authentication configurations. | https://github.com/GhostPack/Rubeus https://github.com/SecureAuthCorp/impacket |
| PolicyPak | Group Policy and endpoint management software that can enforce security policies, including NTLM restrictions. | https://www.policypak.com/ |
| Windows Event Viewer / Security Logs | Built-in Windows tool for monitoring security events, including authentication failures and NTLM usage. | (Standard Windows utility) |
What This Means for Cybersecurity Best Practices
Mandiant’s action is a powerful reinforcement of fundamental cybersecurity principles:
- The relentless pursuit of legacy technology: Attackers will always target the weakest link. Old, deprecated protocols are prime targets.
- The power of public disclosure: Sometimes, a strong, public demonstration of a vulnerability is the most effective way to compel widespread action.
- Proactive defense is paramount: Don’t wait for a public disclosure or an attack to address known vulnerabilities. Regularly audit and update your security posture.
The release of these Net-NTLMv1 rainbow tables is a critical moment. It underscores the profound security risks associated with clinging to outdated technology. Organizations must act decisively to disable Net-NTLMv1, transition to modern authentication protocols, and strengthen their overall security posture. Failure to do so exposes them to an increasingly straightforward method of credential compromise, with potentially devastating implications for data integrity and system security.





