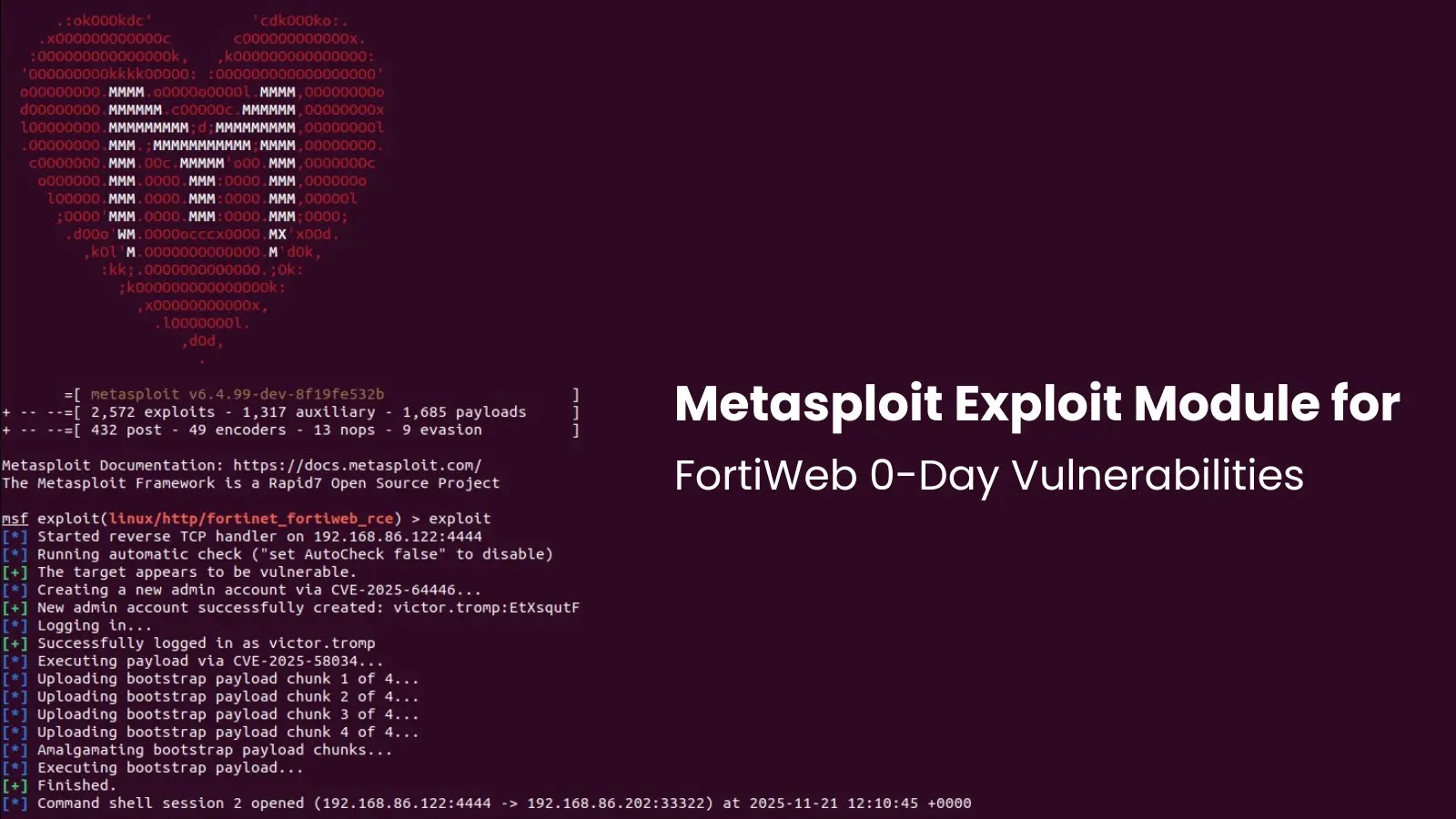
Metasploit Adds Exploit Module for Recently Disclosed FortiWeb 0-Day Vulnerabilities
The cybersecurity landscape is in constant flux, with new threats emerging at an alarming pace. One of the most critical developments for security professionals is the rapid weaponization of newly discovered vulnerabilities. A prime example has just surfaced, with the Metasploit Framework1 integrating an exploit module for recently disclosed FortiWeb 0-Day vulnerabilities. This development significantly escalates the risk for organizations utilizing Fortinet’s FortiWeb Web Application Firewall (WAF), demanding immediate attention and action.
The FortiWeb 0-Day Vulnerabilities: A Dangerous Combination
This new Metasploit module doesn’t target a single flaw but rather chains two distinct vulnerabilities in Fortinet’s FortiWeb WAF to achieve a devastating outcome: unauthenticated Remote Code Execution (RCE) with root privileges. These vulnerabilities are:
- CVE-2025-64446: Further details are pending, but its inclusion in the exploit chain highlights its critical role.
- CVE-2025-58034: Similar to its counterpart, this vulnerability is instrumental in achieving the elevated access.
The combination of these flaws allows an attacker, without any prior authentication, to execute arbitrary code on the affected FortiWeb device with the highest level of system privileges. This means an attacker could completely compromise the WAF, potentially bypassing security controls, gaining access to protected web applications, or even establishing a persistent foothold within the network perimeter.
From Discovery to Weaponization: The Silent Patch Saga
The timeline surrounding these FortiWeb vulnerabilities is particularly concerning. Reports suggest that these flaws were being actively exploited in the wild even before public disclosure. This often indicates a sophisticated actor or group with advanced capabilities. What makes this situation even more complex are reports of “silent patches” – updates released by vendors that address vulnerabilities without explicit acknowledgment or detailed disclosure. While silent patching can sometimes prevent widespread exploitation by malicious actors, it leaves legitimate users in the dark. In this case, attackers reportedly bypassed these silent patches, demonstrating their persistence and deep understanding of the vulnerabilities. The subsequent release of a public Metasploit module democratizes this exploitation capability, making it accessible to a wider range of threat actors.
Impact of a Metasploit Module Release
The moment a widely-used exploitation framework like Metasploit integrates a module for a critical vulnerability, the threat level sky-rockets. Here’s why:
- Ease of Exploitation: Metasploit simplifies complex attack techniques into easy-to-use modules. Even less-skilled attackers can now leverage these 0-day flaws.
- Increased Attack Volume: The lowered barrier to entry inevitably leads to a surge in scanning and exploitation attempts against vulnerable FortiWeb installations.
- Proof of Concept (PoC) Validation: The inclusion in Metasploit serves as a strong validation of the exploit’s reliability and effectiveness.
- Urgent Need for Remediation: Organizations can no longer afford to delay patching or mitigation efforts; the window of opportunity for attackers dramatically widens.
Remediation Actions for FortiWeb Users
Given the severity of these FortiWeb 0-day vulnerabilities and the active exploitation, immediate action is paramount. IT and security teams should prioritize the following:
- Immediate Patching: Apply all available security updates and patches from Fortinet for your FortiWeb appliances without delay. Ensure you are on the absolute latest firmware version.
- Vulnerability Scanning: Conduct thorough vulnerability scans of your external and internal network infrastructure, specifically targeting FortiWeb devices, to identify any unpatched systems.
- Network Segmentation: Implement or review existing network segmentation to limit the blast radius if a FortiWeb device is compromised. Isolate WAFs where possible.
- Logging and Monitoring: Enhance logging on FortiWeb devices and integrated security tools. Monitor logs for suspicious activity, unusual traffic patterns, or unauthorized access attempts. Look for indications of RCE, such as unusual process execution or file modifications.
- Incident Response Plan Review: Review and update your incident response plan to account for potential WAF compromises. Ensure teams are prepared to detect, contain, and eradicate threats.
- Web Application Firewall (WAF) Rule Review: While the WAF itself is vulnerable, ensure that any other WAFs or security controls protecting your web applications have robust rules to detect and prevent common attack vectors, even if not specifically tailored for these FortiWeb flaws.
Relevant Security Tools for Detection and Mitigation
Here’s a table of tools that can assist in detecting or mitigating the risks associated with these types of vulnerabilities:
| Tool Name | Purpose | Link |
|---|---|---|
| Nessus | Vulnerability scanning and assessment. | https://www.tenable.com/products/nessus |
| OpenVAS | Open-source vulnerability scanner. | https://www.greenbone.net/en/community-edition/ |
| Metasploit Framework | Penetration testing and exploit development (can be used defensively to test for vulnerabilities). | https://www.metasploit.com/ |
| SIEM Solutions (e.g., Splunk, Elastic Stack) | Security Information and Event Management for log aggregation, correlation, and alerting. | https://www.splunk.com/, https://www.elastic.co/elastic-stack |
| IDS/IPS (e.g., Snort, Suricata) | Intrusion Detection/Prevention Systems for network traffic analysis and threat blocking. | https://www.snort.org/, https://suricata.io/ |
Conclusion
The addition of an exploit module for FortiWeb 0-day vulnerabilities to Metasploit signals a critical juncture for organizations relying on these WAFs. The ability to achieve unauthenticated RCE with root privileges, especially following reports of active exploitation and bypassed “silent patches,” necessitates an extremely proactive and urgent response. Security teams must prioritize applying all available patches, conducting thorough vulnerability assessments, and enhancing their monitoring capabilities to protect their vital web assets from imminent threats. Staying informed and acting swiftly are your best defenses against these evolving cyber risks.





