Microsoft Copilot Agent Policy Let Any Users Access AI Agents
In the rapidly evolving landscape of enterprise technology, the promise of artificial intelligence offers unprecedented efficiency and innovation. Yet, integration of powerful AI capabilities, such as Microsoft Copilot, necessitates stringent security oversight. Recent findings, however, reveal a critical policy bypass within Microsoft 365 tenants concerning Copilot Agent access. This poses a significant challenge for organizations aiming to maintain granular control over their AI deployments and data security.
The Unintended Accessibility of Copilot Agents
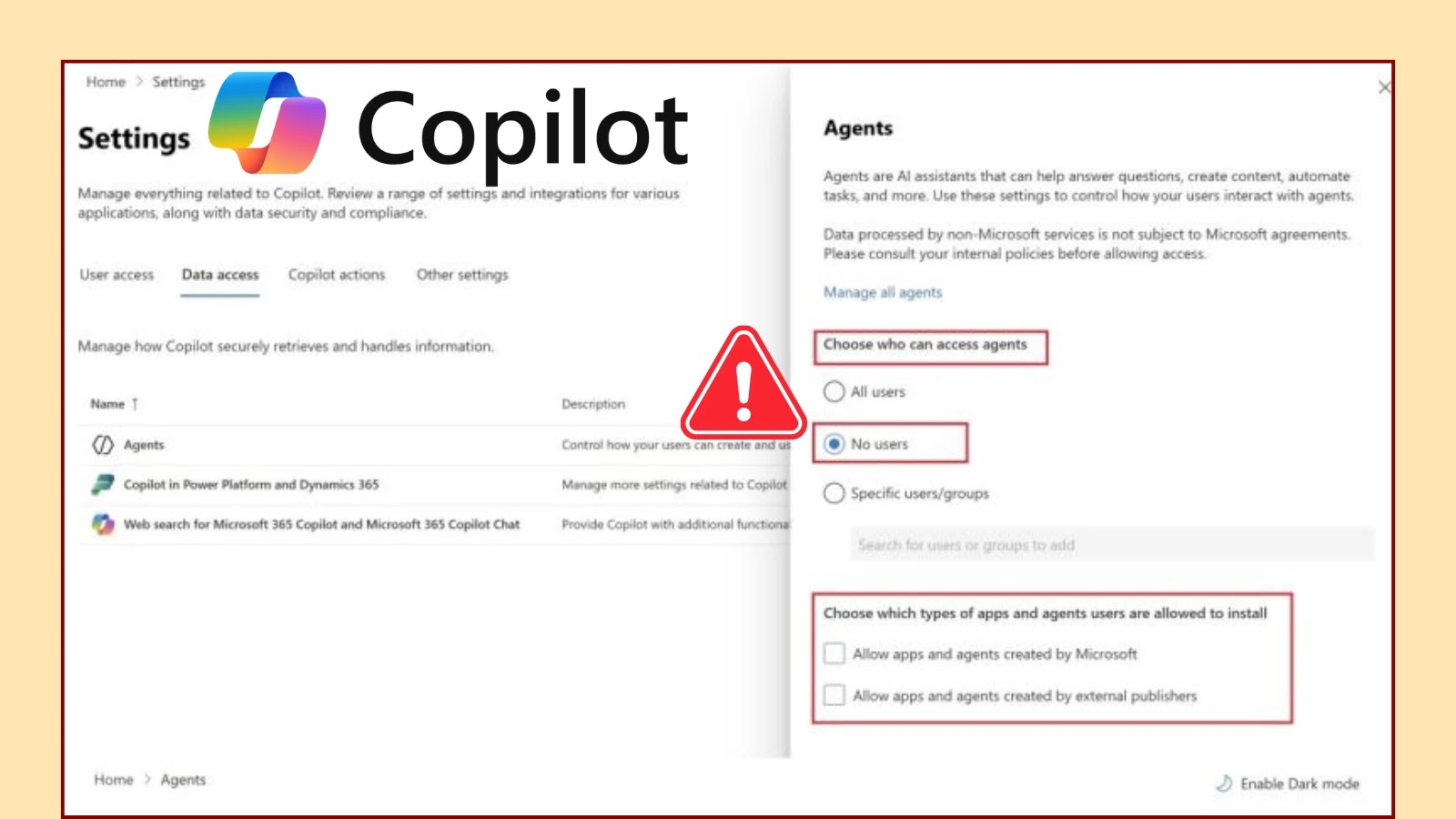
Shortly after the May 2025 rollout, introducing 107 Copilot Agents into Microsoft 365 environments, security specialists identified a concerning flaw. The “Data Access” restriction, specifically designed to prevent unauthorized users from accessing certain Copilot Agents, is being circumvented. This directly contradicts the intended security posture, allowing users who should be restricted from installing or utilizing specific agents to do so without proper authorization.
The core issue lies with the “NoUsersCanAccessAgent” policy. Despite its explicit purpose, this policy is failing to adequately block the availability of several Copilot Agents. This bypass means that even when an administrator intends to limit agent exposure, these agents remain installable and potentially usable by a broader user base than sanctioned.
Operational Overhead and Risk Amplification
The immediate consequence of this policy bypass is a substantial increase in operational overhead for IT and security teams. To mitigate unauthorized access, organizations are currently forced to perform manual revocations on a per-agent basis. This is typically achieved through PowerShell commands, a process that is not only labor-intensive but also prone to human error. Such a fragmented and reactive approach introduces significant risk, as any missed agent or misconfigured command could leave a vulnerability unaddressed.
Furthermore, the uncontrolled distribution of Copilot Agents can lead to data exposure risks. If an agent designed for sensitive data handling is accessible to users without appropriate clearance, it opens pathways for unauthorized information access or manipulation. This undermines compliance efforts and increases the potential for data breaches, underscoring the critical need for robust access controls in AI deployments.
Remediation Actions
Addressing this policy bypass requires a multi-faceted approach, blending proactive auditing with precise technical interventions. Organizations must act swiftly to regain control over their Copilot Agent ecosystem.
- Comprehensive Inventory and Auditing: Begin by performing a thorough audit of all deployed Copilot Agents within your Microsoft 365 tenant. Identify which agents are active, which users have access, and compare this against your intended access policies. Utilize Microsoft 365 admin centers and PowerShell cmdlets to gain a complete picture of your current state.
- Per-Agent PowerShell Revocation: Until a permanent fix is provided by Microsoft, leverage PowerShell to manually revoke access for specific agents where the “NoUsersCanAccessAgent” policy has failed. This is a crucial, albeit temporary, measure. Ensure meticulous documentation of all revocations to maintain configuration consistency.
- Enforce Principle of Least Privilege (PoLP): Reinforce the principle of least privilege across all user accounts. Ensure that users only have access to the Copilot Agents and data necessary for their roles. This foundational security practice minimizes the blast radius should an agent become unintentionally accessible.
- Monitor Microsoft Communications: Stay vigilant for official communications from Microsoft regarding this issue. A patch or updated guidance is likely to be released. Organizations should be prepared to deploy such updates promptly to restore intended policy enforcement.
- User Training and Awareness: Educate users about the proper use of Copilot Agents and the importance of reporting any unusual access or functionality. A well-informed user base can act as an additional layer of defense.
Tools for Management and Monitoring
Effective management and monitoring of Copilot Agent access within Microsoft 365 require specific tools. While direct remediation via a single product might be limited due to the nature of the policy flaw, these tools can aid in detection, auditing, and enforcing overall security posture.
| Tool Name | Purpose | Link |
|---|---|---|
| Microsoft 365 Admin Center | General management, user administration, and initial policy review for Microsoft 365 services. | https://admin.microsoft.com/ |
| PowerShell for Microsoft 365 | Advanced configuration, scripting for bulk actions, and detailed auditing of policies and agent access. | https://learn.microsoft.com/en-us/microsoft-365/enterprise/connect-to-microsoft-365-powershell?view=o365-worldwide |
| Microsoft Purview (formerly Compliance Center) | Data governance, compliance monitoring, and identifying sensitive data exposure related to agent activities. | https://compliance.microsoft.com/ |
| Microsoft Defender for Cloud Apps (MDCA) | Shadow IT discovery, app governance, and anomaly detection which could indicate misuse of agents. | https://learn.microsoft.com/en-us/cloud-app-security/ |
Summary and Outlook
The discovery of the Microsoft Copilot Agent policy bypass is a stark reminder that even sophisticated security controls can have hidden vulnerabilities. The “NoUsersCanAccessAgent” policy’s failure to prevent some Copilot Agents from being installed by unauthorized users mandates immediate attention from IT security professionals. While manual per-agent PowerShell revocations provide a temporary workaround, the long-term solution requires a robust fix from Microsoft and a renewed emphasis on comprehensive auditing and the principle of least privilege within organizational AI deployments. Proactive engagement, diligent monitoring, and adherence to security best practices remain paramount in securing the intelligent enterprise.





