Microsoft OneDrive Auto-Sync Exposes Enterprise Secrets in SharePoint Online
The ubiquity of cloud collaboration tools brings unparalleled efficiency to enterprises. However, this convenience often masks underlying security vulnerabilities. A recent discovery regarding Microsoft OneDrive’s auto-sync feature highlights a critical risk: the unintentional exposure of enterprise secrets within SharePoint Online. This isn’t just a theoretical concern; research indicates this mechanism is a significant contributor to sensitive data breaches across organizations.
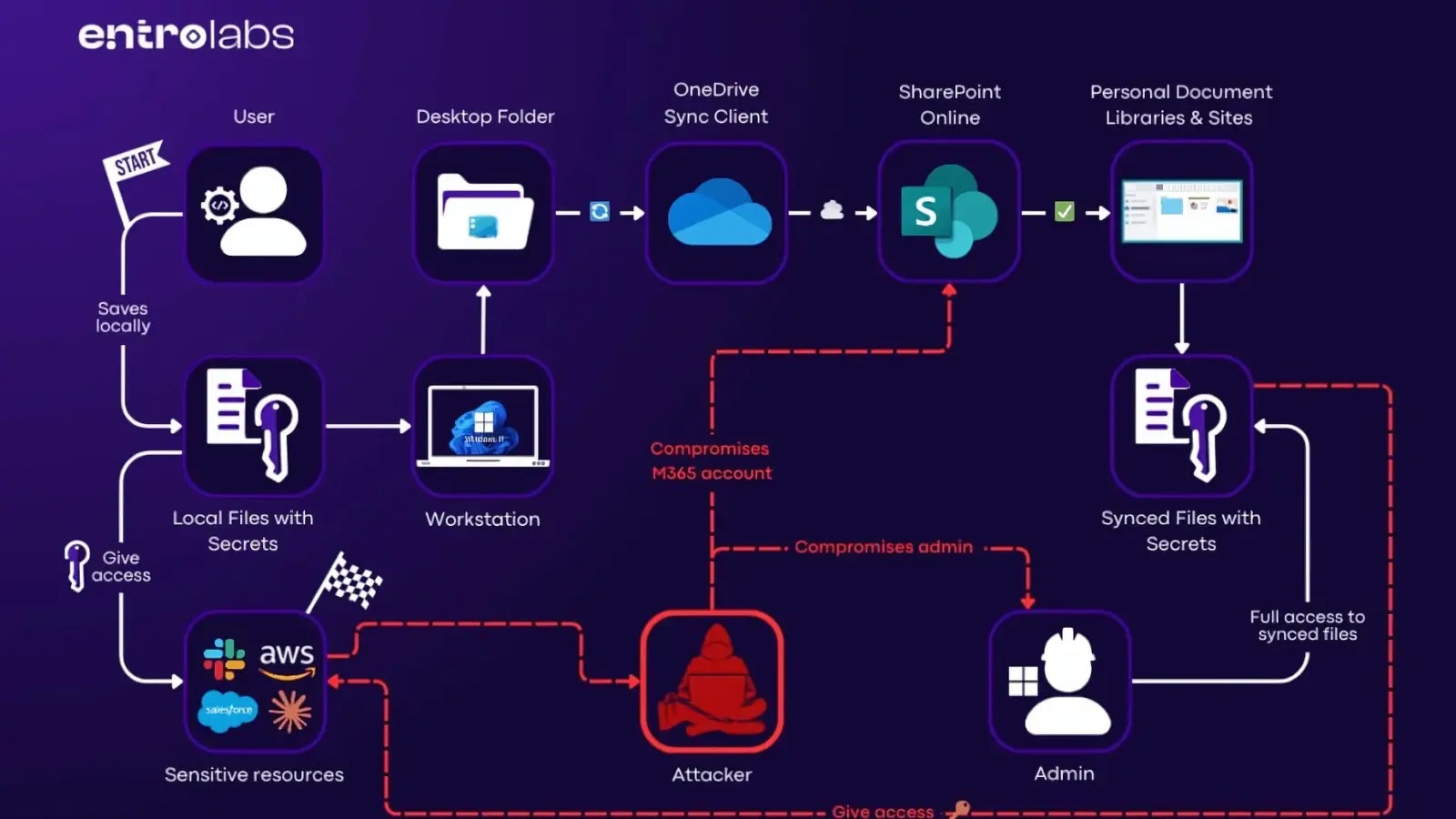
The Unseen Threat: OneDrive’s Auto-Sync and SharePoint Exposure
Microsoft OneDrive, a core component of many enterprise ecosystems, includes a default auto-sync capability designed to simplify file management. While seemingly innocuous, this feature automatically moves local files to SharePoint. The convenience it offers often overshadows a critical security oversight: this automatic transfer can inadvertently publish sensitive data, including critical enterprise secrets, to an accessible SharePoint environment.
Research from Entro Security, as reported by CybersecurityNews.com, casts a stark light on the severity of this issue. Their findings reveal that a staggering one in five exposed secrets within an enterprise can be traced back to files synced to SharePoint. This statistic underscores the profound impact of this often-overlooked default setting. The implications range from compromised API keys and database credentials to sensitive intellectual property and proprietary code, all unknowingly made accessible due to an automated process.
Understanding the Mechanism of Exposure
The core of this vulnerability lies in the default configuration of OneDrive auto-sync. When a user saves or updates a file locally, the auto-sync feature immediately pushes that file to the designated SharePoint location. If the user’s local machine contains files with embedded secrets – perhaps in configuration files, scripts, or project documentation – those secrets are then replicated directly into SharePoint.
The risk escalates depending on the SharePoint site’s permissions and accessibility. If the SharePoint site or library has broader access permissions than intended for files containing secrets, these sensitive elements become exposed to a wider audience, including internal users who shouldn’t have access, or even external parties if misconfigurations extend to public sharing. This inadvertent publication creates a massive attack surface for threat actors seeking to exploit exposed credentials or proprietary information.
Remediation Actions: Securing Your Enterprise Secrets
Addressing this vulnerability requires a multi-faceted approach, combining policy enforcement, technical controls, and user education.
- Implement Strict Data Loss Prevention (DLP) Policies: Configure and enforce robust DLP policies within Microsoft 365. These policies should be designed to detect and prevent the uploading of sensitive patterns (e.g., API keys, credential formats, social security numbers) to SharePoint and OneDrive.
- Review and Restrict SharePoint Permissions: Conduct a comprehensive audit of all SharePoint sites and libraries. Ensure that permissions are granted on a “least privilege” basis. Regularly review external sharing settings and disable them unless absolutely necessary for specific, approved use cases.
- Educate Users on Secure File Handling: Develop and deploy mandatory training programs for all employees regarding the risks of embedding secrets in files and the implications of OneDrive auto-sync. Emphasize best practices for storing and managing sensitive information, advocating for dedicated secure vaults or secrets management solutions.
- Utilize Secrets Management Solutions: Integrate dedicated secrets management platforms (e.g., HashiCorp Vault, Azure Key Vault, AWS Secrets Manager) for storing and retrieving sensitive credentials and API keys. This centralizes secrets and prevents their proliferation in local files that could be auto-synced.
- Perform Regular Security Audits and Scans: Implement continuous scanning solutions that can detect exposed secrets within your Microsoft 365 environment, including SharePoint and OneDrive. Tools designed for cloud security posture management (CSPM) and data security posture management (DSPM) can be invaluable here.
- Disable or Configure Auto-Sync Carefully: Where feasible and appropriate for the business context, consider disabling the auto-sync feature for specific folders or entirely, or ensure that synchronized folders are strictly controlled and monitored for sensitive content.
Tools for Detection and Mitigation
Securing against inadvertently exposed secrets in SharePoint and OneDrive requires specialized tools for scanning, detection, and ongoing monitoring.
| Tool Name | Purpose | Link |
|---|---|---|
| Microsoft 365 Defender (DLP) | Data Loss Prevention (DLP) for identifying and protecting sensitive information across Microsoft 365 services. | Microsoft Learn |
| Microsoft Purview Information Protection | Classifies, labels, and protects sensitive data, integrating with DLP for enhanced control. | Microsoft Learn |
| Cloud Security Posture Management (CSPM) Platforms | Identifies misconfigurations and compliance risks in cloud environments, including SharePoint permissions. (e.g., Wiz, Orca Security, Lacework) | Gartner Peer Insights (Example) |
| Secrets Scanning Tools (e.g., GitGuardian, SpectralOps) | Scans various data sources (code repositories, cloud storage, documents) for exposed secrets. | GitGuardian / SpectralOps |
| HashiCorp Vault | Centralized secrets management for dynamic generation and secure storage of credentials. | Vault |
| Azure Key Vault | Cloud-based service for managing encryption keys, secrets, and certificates. | Azure Key Vault |
Key Takeaways
The convenience of Microsoft OneDrive’s auto-sync feature, while beneficial for productivity, has a demonstrated dark side: the large-scale exposure of enterprise secrets within SharePoint Online. This isn’t a speculative threat but a proven vulnerability contributing significantly to data breaches. Organizations must move beyond the assumption of inherent security in cloud services and actively implement robust cybersecurity practices. This includes stringent DLP, meticulous permission management, rigorous security awareness training for employees, and the adoption of dedicated secrets management solutions. Proactive detection and continuous monitoring are essential to prevent sensitive information from being inadvertently exposed and exploited.





