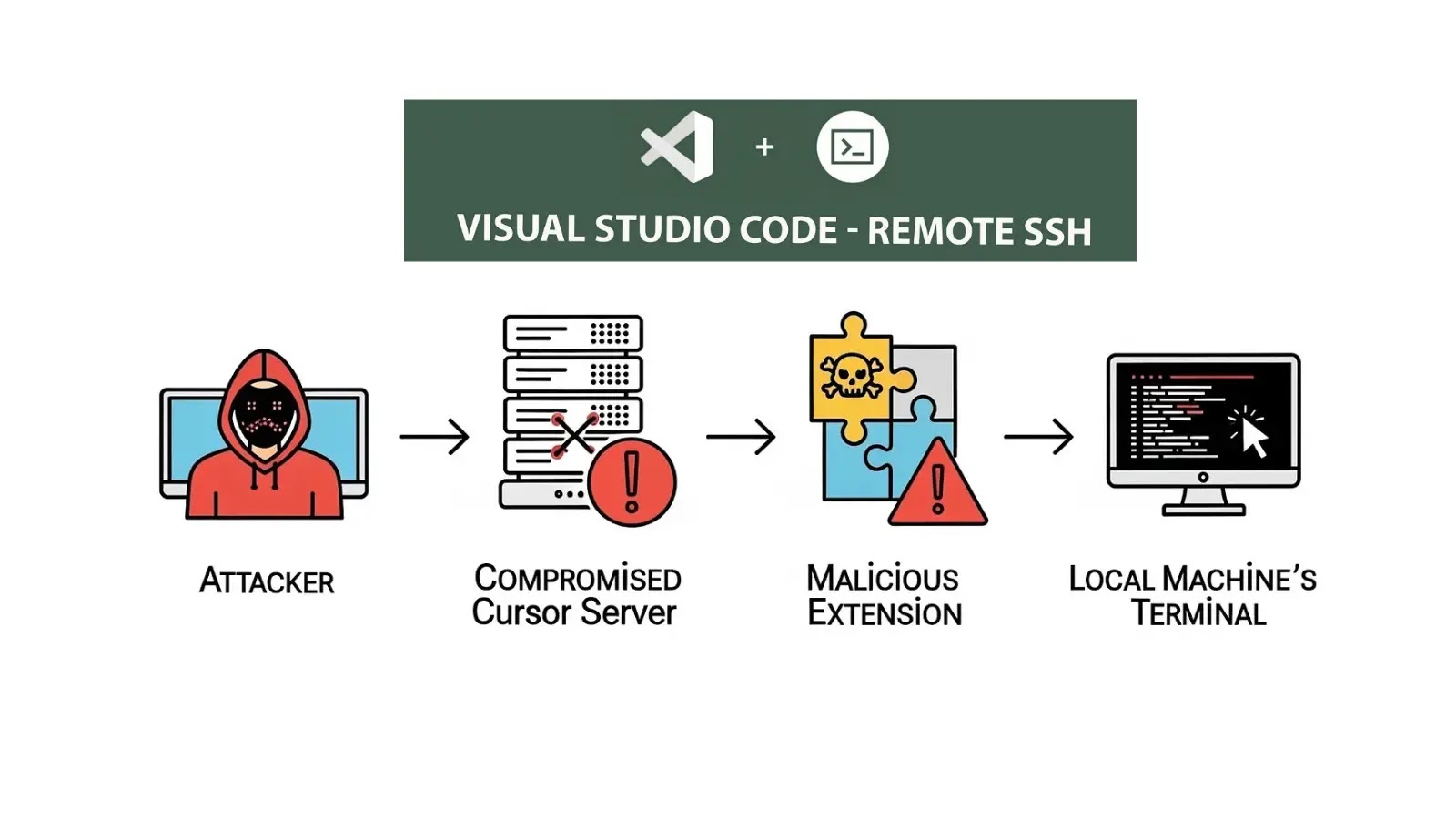
Microsoft VS Code Remote-SSH Extension Hacked to Execute Malicious Code on Developer’s Machine
For many developers and IT professionals, the Microsoft VS Code Remote-SSH extension is an indispensable tool, seamlessly bridging the gap between local development environments and remote servers. It fosters incredible productivity, allowing teams to collaborate on projects hosted anywhere. However, this very convenience, rooted in a fundamental trust relationship, has been exploited. A critical security vulnerability has emerged, demonstrating how a compromised remote server can leverage the Remote-SSH extension to execute malicious code directly on a developer’s local machine. This isn’t just a hypothetical threat; it’s a stark reminder that even our most trusted development tools can become vectors for attack.
The Vibe Hacking Attack: A Deeper Dive into the Vulnerability
Security researchers have unveiled an attack, aptly dubbed “Vibe Hacking,” that weaponizes the inherent trust between a developer’s local machine and their remote development environment. This attack targets a critical flaw within the Microsoft VS Code Remote-SSH extension, allowing attackers to execute arbitrary code on the developer’s local system. The core of “Vibe Hacking” lies in the way the Remote-SSH extension handles certain aspects of the remote connection. While specific technical details are still emerging, the essence of the vulnerability is that a malicious actor, having gained control of a remote server a developer connects to via Remote-SSH, can then introduce specially crafted payloads that are misinterpreted or mishandled by the local VS Code client. This misinterpretation leads to the unintended execution of the attacker’s code on the developer’s machine.
This vulnerability affects more than just VS Code; the underlying principle could potentially impact other remote development environments that share similar trust models. The immediate concern, however, is the widespread adoption of VS Code and its Remote-SSH extension, making a vast number of developer machines potential targets.
Understanding the Threat: Why Developers are Prime Targets
The impact of this vulnerability extends far beyond inconvenience. Developers’ machines often hold a treasure trove of sensitive information: source code, API keys, credentials for various services, and intellectual property. A successful attack through the VS Code Remote-SSH extension could lead to:
- Intellectual Property Theft: Attackers could exfiltrate proprietary source code, design documents, and confidential project data.
- Supply Chain Attacks: Compromised developer machines could be used as a stepping stone to inject malicious code into software projects, leading to widespread supply chain compromises.
- Credential Harvesting: Malicious code could be designed to steal login credentials for internal systems, cloud platforms, and code repositories.
- Ransomware Deployment: An attacker could deploy ransomware on the developer’s machine, encrypting critical files and demanding payment.
- Lateral Movement: A foothold on a developer’s machine often provides an attacker with a beachhead to move laterally within an organization’s network.
The insidious nature of “Vibe Hacking” is that it leverages a tool designed for convenience and productivity, turning it into a conduit for compromise. Developers, accustomed to working in trusted environments, might not immediately suspect their VS Code extension as the source of a breach.
Remediation Actions for Developers and Organizations
Addressing this security vulnerability requires immediate and decisive action. Both individual developers and organizations need to implement a multi-layered defense strategy.
- Update VS Code and Extensions Immediately: Microsoft has likely or will release patches for the VS Code Remote-SSH extension. Ensure your VS Code client and all installed extensions are up to date. Regularly check for and apply updates.
- Principle of Least Privilege for Remote Servers: When setting up or connecting to remote development environments, ensure that the user account used has the absolute minimum necessary permissions. Avoid using root or highly privileged accounts for routine development tasks.
- Regular Security Audits of Remote Servers: Implement regular security audits and penetration testing of your remote development servers. Ensure they are free of known vulnerabilities and are configured securely.
- Use SSH Key Best Practices: Always use strong, passphrase-protected SSH keys. Avoid password-based authentication for SSH. Regularly rotate SSH keys and revoke access for any keys that may have been compromised.
- Implement Endpoint Detection and Response (EDR): Deploy EDR solutions on developer workstations. These tools can help detect and respond to suspicious activity, even if it originates from a seemingly legitimate process like a VS Code extension.
- Network Segmentation: Isolate development environments from production networks where possible. This can limit the blast radius of a successful attack.
- Developer Security Awareness Training: Educate developers about the risks of connecting to untrusted or potentially compromised remote environments. Emphasize the importance of verifying server integrity.
- Consider Air-Gapped or Sandboxed Environments: For highly sensitive projects, consider using air-gapped development machines or highly sandboxed environments that limit network access and potential for lateral movement.
Relevant Tools for Detection, Scanning, and Mitigation
Utilizing the right tools is crucial for both preventing and responding to such vulnerabilities. Here’s a selection of tools that can enhance your security posture:
| Tool Name | Purpose | Link |
|---|---|---|
| VS Code Marketplace | Updating VS Code and Extensions | https://marketplace.visualstudio.com/vscode |
| OpenSSH | Secure Shell Utilities (Key Management) | https://www.openssh.com/ |
| OWASP ZAP | Web Application Security Scanner (for remote web services) | https://www.zaproxy.org/ |
| Nessus | Vulnerability Scanner (for remote servers) | https://www.tenable.com/products/nessus |
| CrowdStrike Falcon Insight | Endpoint Detection and Response (EDR) | https://www.crowdstrike.com/products/endpoint-security/falcon-insight-xdr/ |
| Microsoft Defender for Endpoint | Endpoint Detection and Response (EDR) | https://www.microsoft.com/en-us/security/business/threat-protection/microsoft-defender-for-endpoint |
Looking Ahead: Securing the Development Pipeline
The “Vibe Hacking” vulnerability affecting the Microsoft VS Code Remote-SSH extension underscores a critical principle: trust, while essential for productivity, must always be verified. As development environments become increasingly distributed and cloud-native, the attack surface expands. Organizations and developers must evolve their security strategies to encompass not just code security, but also the security of the tools and infrastructure used to create that code.
Regular updates, adhering to the principle of least privilege, robust security monitoring, and continuous developer education are no longer optional. They are foundational elements of a secure software development lifecycle. By proactively addressing these challenges, we can continue to leverage powerful tools like VS Code Remote-SSH while safeguarding our systems and intellectual property from sophisticated threats. The digital landscape demands vigilance, and this incident serves as a potent reminder of that enduring truth.





