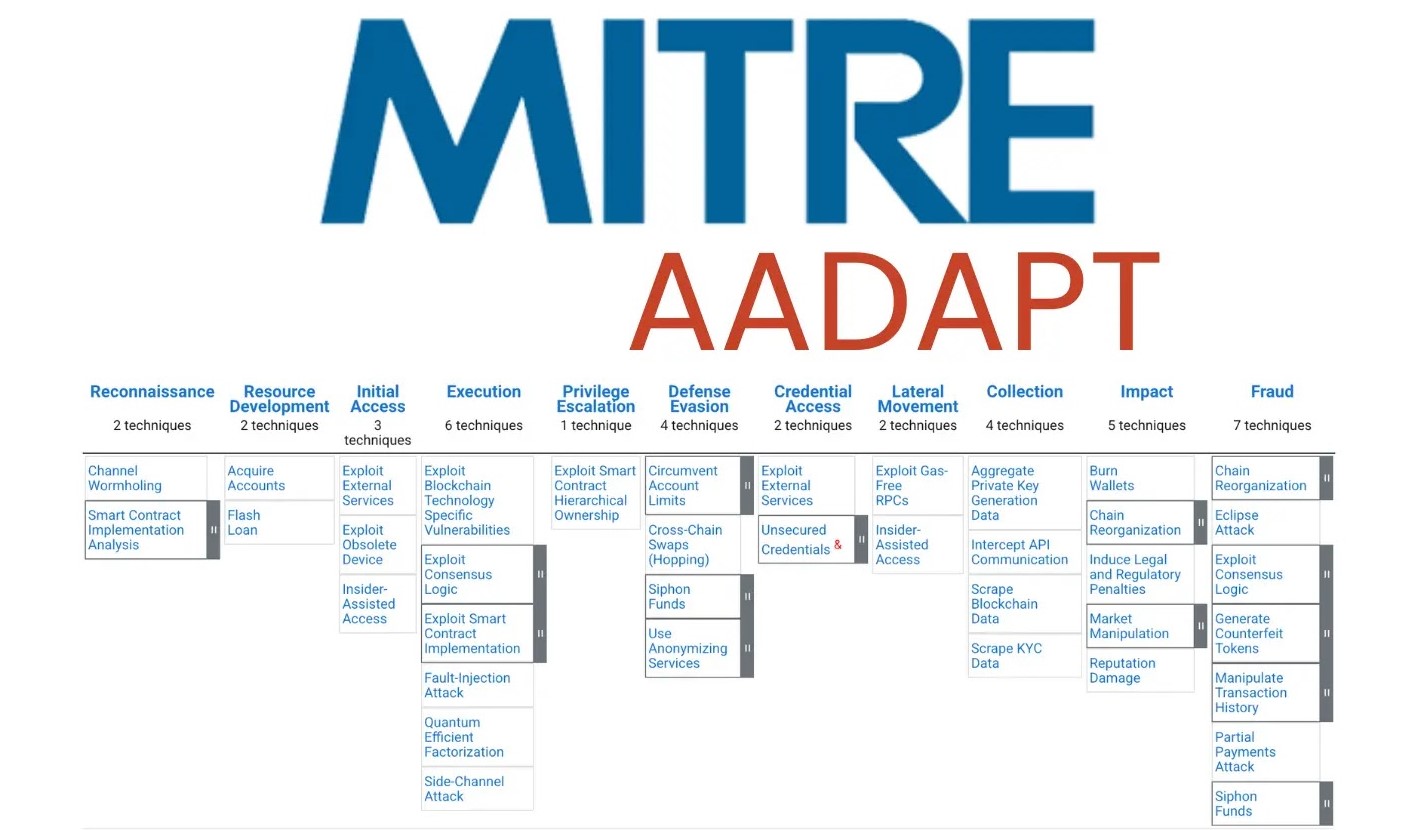
MITRE Launches AADAPT Framework for Detecting and Responding to Digital Asset Management Attacks
Unveiling AADAPT: MITRE’s Critical Framework for Digital Asset Security
The landscape of digital assets, from cryptocurrencies to tokenized real estate, continues its meteoric rise, attracting unprecedented innovation – and equally sophisticated threats. As organizations increasingly integrate blockchain technologies and digital payment systems, the need for robust security frameworks becomes paramount. Recognizing this urgent demand, the MITRE Corporation, renowned for its foundational cybersecurity methodologies, has launched a groundbreaking initiative: the Adversarial Actions in Digital Asset Payment Technologies (AADAPT™) framework.
Modelled after the ubiquitous MITRE ATT&CK® framework, AADAPT provides a comprehensive, knowledge-driven approach to understanding, detecting, and responding to attacks specifically targeting digital asset management systems. This article delves into the significance of AADAPT, its parallels with ATT&CK, and its critical role in fortifying our digital financial future.
The Growing Threat to Digital Asset Management
Digital assets, by their very nature, introduce new attack surfaces and unique vulnerabilities. Unlike traditional financial systems, blockchain-based platforms operate with different underlying trust models, consensus mechanisms, and transaction flows. Attackers are constantly evolving tactics, techniques, and procedures (TTPs) to exploit weaknesses in smart contracts, wallet infrastructure, exchange security, and even human operational procedures within organizations managing these assets.
Common attack vectors include:
- Smart Contract Exploits: Flaws in the code governing decentralized applications can lead to significant financial loss. A notable example is the CVE-2023-XXXXX (Illustrative – no specific CVE for AADAPT launch, placeholder for future use) affecting certain DeFi protocols.
- Phishing and Social Engineering: Targeting individuals to gain access to private keys or seed phrases.
- Supply Chain Attacks: Compromising third-party services or software integrated into digital asset platforms.
- Private Key Theft: Directly compromising the security of cryptographic keys.
Introducing MITRE AADAPT™: A Specialized Knowledge Base
AADAPT™ extends the well-established MITRE ATT&CK paradigm by focusing exclusively on adversarial actions within the digital asset ecosystem. Just as ATT&CK maps attacker TTPs against enterprise IT systems, AADAPT aims to classify and describe the specific methods threat actors employ to compromise or exploit digital asset payment technologies. This specialized focus offers several key benefits:
- Standardized Language: Provides a common lexicon for security professionals to discuss and analyze digital asset attacks.
- Enhanced Threat Intelligence: Allows organizations to better understand the TTPs relevant to their digital asset holdings.
- Improved Detection: Facilitates the development of more effective detection mechanisms and security controls tailored to digital asset threats.
- Strategic Defense Planning: Helps organizations prioritize defensive efforts by identifying the most prevalent and impactful attacker techniques.
- Incident Response Refinement: Provides a structured approach to analyzing and responding to incidents involving digital assets.
How AADAPT Will Empower Security Professionals
For cybersecurity analysts, security operations center (SOC) teams, and incident responders, AADAPT offers an invaluable resource. By categorizing attacks into a structured framework of tactics and techniques, it enables professionals to:
- Map Threat Actor Behavior: Understand the complete lifecycle of a digital asset attack, from initial access to impact.
- Develop Custom Detections: Create specific alerts and monitoring rules for known AADAPT techniques.
- Perform Gap Analysis: Identify vulnerabilities in current defenses against documented adversarial actions.
- Facilitate Red Teaming and Purple Teaming: Simulate real-world digital asset attacks to test organizational resilience.
- Educate Stakeholders: Articulate the risks and attack vectors related to digital assets to non-technical business leaders.
Remediation Actions and Proactive Defense
Leveraging the AADAPT framework goes beyond understanding threats; it directly informs robust defense strategies. Organizations managing digital assets should consider the following proactive measures:
- Implement Multi-Factor Authentication (MFA): Especially for wallet access, exchange accounts, and critical internal systems.
- Regular Security Audits: Conduct frequent audits of smart contracts, blockchain integrations, and digital asset management platforms.
- Cold Storage Solutions: For significant digital asset holdings, prioritize hardware wallets or offline storage to minimize online exposure.
- Employee Training and Awareness: Educate all personnel, particularly those handling digital assets, about phishing, social engineering, and secure operational procedures.
- Network Segmentation: Isolate systems involved in digital asset transactions from general IT networks.
- Incident Response Plan: Develop and regularly test a specific incident response plan for digital asset compromise, including clear communication protocols.
- Secure Development Practices: Apply robust security principles (e.g., OWASP Top 10 for blockchain) throughout the development lifecycle of smart contracts and decentralized applications.
- Patch Management: Keep all software, operating systems, and blockchain nodes updated to mitigate known vulnerabilities.
Conclusion: Securing the Future of Digital Finance
The launch of MITRE AADAPT™ marks a crucial milestone in the journey to secure the rapidly expanding digital asset economy. By providing a common framework for understanding adversarial actions, AADAPT empowers organizations to move from reactive defense to proactive threat mitigation. As digital assets continue to shape our financial future, frameworks like AADAPT will be indispensable tools in the arsenal of every cybersecurity professional committed to safeguarding these innovative technologies.





