Network Security assessment : Techniques and Guide
In today’s digitally-driven landscape, ensuring robust security measures within your network infrastructure is not just a priority—it’s a necessity for effective cyber security. As businesses increasingly rely on digital operations, the risk of cyber threats and data breaches looms large. Network security assessments provide a comprehensive analysis of your current security posture, identifying vulnerabilities and implementing solutions to safeguard your enterprise. At Teamwin Global Technologica, we recognize the paramount importance of our customers’ businesses and are dedicated to ensuring your infrastructure remains secure, safe, and capable of withstanding any cyber threat.
Understanding Security Assessment
What is a Security Assessment?
A security assessment is a systematic evaluation of an organization’s information security measures to identify vulnerabilities and assess the effectiveness of existing security controls. This process involves a detailed examination of network infrastructure, security policies, and potential security gaps that could lead to a data breach. By leveraging automated tools and techniques like penetration testing and network scanning, security professionals conduct a thorough security audit. This assessment helps in determining the organization’s security posture, ensuring that outdated software and network vulnerabilities are promptly addressed. At Teamwin Global Technologica, we empower our clients through a comprehensive suite of IT security solutions to fortify their business against potential threats.
Importance of Network Security Assessments
Network security assessments are crucial in safeguarding your organization’s digital assets and maintaining a strong security posture. By conducting a network security risk assessment, businesses can identify vulnerabilities within their network services and infrastructure before they are exploited. This proactive approach not only prevents potential data breaches but also reassures stakeholders about the organization’s commitment to cybersecurity. Regular assessments evaluate the effectiveness of security measures and ensure compliance with industry standards. At Teamwin Global Technologica, we assure your infrastructure is secure, safe, and resilient, safeguarding your enterprise and ensuring tomorrow’s success.
Key Elements of a Security Risk Assessment
A thorough security risk assessment involves several key elements designed to provide a comprehensive overview of an organization’s security vulnerabilities and overall security. It begins with identifying the types of network services in use, followed by an analysis of current security controls and policies. Key steps in this process include:
- Evaluating potential risks and the impact of security threats on business operations is crucial for effective cyber security.
- Implementing security measures and conducting periodic reviews to maintain a robust security environment.
At Teamwin Global Technologica, we focus on empowering our clients to anticipate and mitigate cyber risks through vigilant monitoring and swift response strategies, ultimately providing peace of mind and value for money.
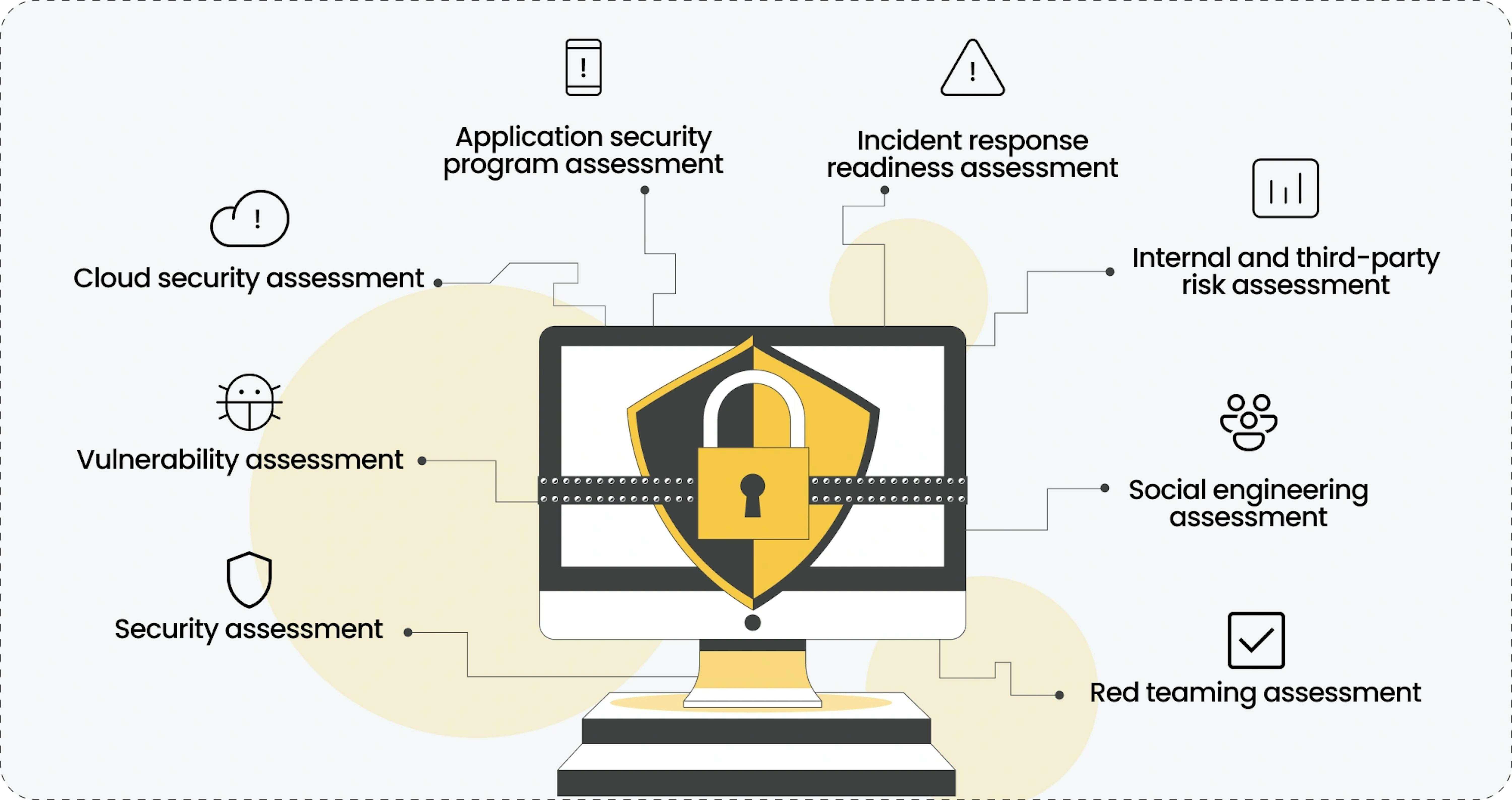
Types of Network Security Assessments
Vulnerability Assessments
An Expert Network Security Assessment is crucial for comprehensively evaluating a client’s network security posture. This process involves meticulously identifying security vulnerabilities that could potentially compromise the integrity of your network. At Teamwin Global Technologica, we focus on pinpointing pain points within your infrastructure and recommending appropriate solutions to address them. Our vulnerability assessments are not merely about detection; they are about proactive prevention. Here are some of the methods we utilize to ensure your network remains robust and secure through effective security analysis:
- Network scanning
- Penetration testing
Our goal is to fortify your defenses and safeguard your enterprise from potential cyber threats through continuous security monitoring.
Security Audits and Their Role
Security audits play a pivotal role in any comprehensive network security assessment. They provide an in-depth analysis of your organization’s existing security controls, policies, and procedures to enhance overall security. At Teamwin Global Technologica, we conduct thorough security audits to ensure that your network infrastructure adheres to industry standards and best practices. This process involves several key steps:
- Evaluating the effectiveness of current security measures and identifying any security gaps that could lead to vulnerabilities.
- Leveraging automated tools to perform audits efficiently is essential for security teams to ensure protection against potential data breaches.
By maintaining a strong security posture, we help you mitigate risks and enhance your enterprise’s cybersecurity resilience.
Conducting a Cyber Risk Assessment
Conducting a cyber risk assessment is essential for understanding and mitigating potential threats to your network. At Teamwin Global Technologica, we recognize the importance of a comprehensive approach to assessing cybersecurity risks. Our assessments focus on identifying and evaluating potential risks that could impact your organization’s operations, ensuring that you are prepared to address them proactively. Through detailed analysis and expert insight, we help you implement security measures that strengthen your defenses against evolving threats. Our team is dedicated to empowering your business with the knowledge and tools necessary to maintain a secure, resilient network environment, ensuring that your enterprise can thrive in the face of cyber challenges.
Performing a Network Security Risk Assessment
Steps to Conduct a Network Security Assessment
Conducting a network security assessment helps in meticulously evaluating your network infrastructure to ensure its integrity. The first step involves gathering comprehensive information about your network assets and current security posture. This is followed by identifying potential security vulnerabilities that could compromise your network. Next, security professionals employ automated tools and techniques like penetration testing and network scanning to conduct a thorough analysis. The assessment evaluates the effectiveness of existing security controls and policies, providing insights into areas that require improvement. At Teamwin Global Technologica, we are committed to empowering our clients with the knowledge and tools necessary to enhance their cybersecurity resilience and safeguard their enterprise from potential threats.
Identifying Vulnerabilities in Your Network
Identifying vulnerabilities is a critical component of any network security assessment. This process involves a detailed examination of your network infrastructure to detect potential security gaps that could lead to a data breach. Security professionals use advanced techniques and tools to identify weaknesses in your network services and outdated software that could be exploited by malicious actors. Understanding these vulnerabilities allows for the implementation of robust security measures to protect your organization. At Teamwin Global Technologica, we prioritize the security of your enterprise by diligently identifying and addressing vulnerabilities, ensuring that your business remains secure, safe, and capable of withstanding any cyber threat.
Tools and Techniques for Network Assessment
Utilizing the right tools and techniques is essential for an effective network security assessment. Automated tools, such as vulnerability scanners and penetration testing software, play a pivotal role in identifying and analyzing security vulnerabilities. These tools provide comprehensive insights into your network’s security posture, allowing security professionals to conduct a thorough security audit. Network scanning helps in detecting potential threats and assessing the risk associated with each vulnerability. At Teamwin Global Technologica, we leverage cutting-edge technologies and expert methodologies to perform detailed network assessments, ensuring that your organization is equipped with the protection it needs to mitigate cybersecurity risks. Our commitment is to provide you with peace of mind by delivering reliable and effective security solutions tailored to your unique needs.
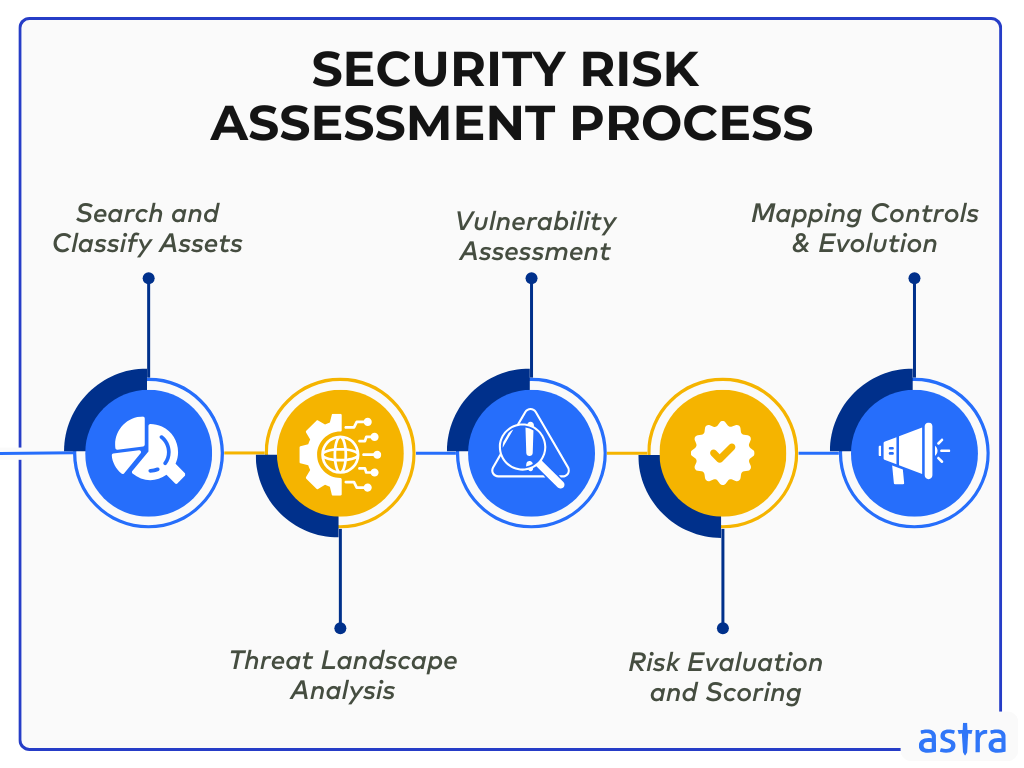
Security Risk Assessment Process
Planning and Preparation
Effective planning and preparation are the cornerstones of a successful security risk assessment. This phase involves gathering crucial information about your network infrastructure, identifying key stakeholders, and defining the scope of the assessment. Security professionals at Teamwin Global Technologica work closely with clients to understand their unique needs and tailor the assessment to address specific security concerns. By setting clear objectives and establishing a detailed roadmap, we ensure that every aspect of your network security is scrutinized through a thorough security analysis. Our proactive approach empowers organizations to anticipate potential threats and implement robust security measures, safeguarding your enterprise against cyber risks.
Data Collection and Analysis
Data collection and analysis are pivotal to identifying network vulnerabilities within your network. During this phase, security professionals employ advanced tools like network scanning and penetration testing to gather comprehensive data on network services, security controls, and potential security gaps. By meticulously analyzing this data, we can evaluate the current security posture and pinpoint areas that require immediate attention. At Teamwin Global Technologica, we leverage automated tools to ensure a thorough and efficient assessment process. This detailed analysis not only highlights critical vulnerabilities but also provides actionable insights to enhance your organization’s cybersecurity resilience.
Reporting and Mitigation Strategies
Once data collection and analysis are complete, the next step is to compile a comprehensive report detailing the findings of the security risk assessment. This report includes an in-depth evaluation of identified vulnerabilities and their potential impact on your network security. At Teamwin Global Technologica, we prioritize transparency and clarity, ensuring that our clients fully understand the assessment results. We also provide tailored mitigation strategies designed to address specific security threats and strengthen your organization’s defenses. By implementing these targeted security measures, you can protect your information assets and maintain a robust security posture.
Hidden Risks in Network Security
Common Security Vulnerabilities
Common security vulnerabilities often lurk unnoticed within network infrastructures, posing significant risks to organizations. These vulnerabilities can stem from outdated software, misconfigured security controls, or unpatched network services. Security professionals at Teamwin Global Technologica are adept at identifying these hidden threats through comprehensive vulnerability assessments. By addressing these vulnerabilities proactively, organizations can prevent data breaches and safeguard their critical information assets. Our commitment to security ensures that your network remains resilient against both known and emerging cyber threats, providing you with the peace of mind to focus on your business objectives.
Impact of Cloud Solutions on Security Risks
The adoption of cloud solutions has revolutionized business operations, but it also introduces new security risks. Cloud environments can present unique challenges, such as data breaches and unauthorized access, if not managed properly, highlighting the need for security monitoring. At Teamwin Global Technologica, we understand the complexities of cloud security and offer expert guidance to mitigate these risks. Our cybersecurity risk assessments evaluate the impact of cloud solutions on your security posture, ensuring that robust security measures are in place to protect your data. By leveraging our expertise, you can confidently embrace cloud technologies while maintaining a secure and compliant network environment with improved security ratings.
Managing Risks in a Complex Network Environment
Managing risks in a complex network environment requires a strategic and multi-faceted approach. With the ever-evolving threat landscape, organizations must remain vigilant in identifying and mitigating security vulnerabilities. Teamwin Global Technologica provides comprehensive assessment services that address the unique challenges of complex network infrastructures. Our security professionals utilize cutting-edge tools and techniques to evaluate your network’s security posture and implement effective security controls. By developing tailored risk management strategies, we empower our clients to navigate the complexities of network security, ensuring their enterprise is well-protected against cyber threats and prepared for future challenges.
What is a network security assessment?
A network security assessment is a comprehensive evaluation of an organization’s network infrastructure. It aims to identify security vulnerabilities, assess the effectiveness of existing security measures, and ensure that your security posture is robust against potential threats.
Why is conducting a network security risk assessment important?
Conducting a network security risk assessment is crucial for organizations to understand their security landscape. It helps identify accessible hosts and network services, evaluate the security controls in place, and implement necessary risk mitigation strategies to protect against cyber threats.
What types of network security assessments can be performed?
There are several types of network security assessments, including vulnerability assessments, security audits, and penetration testing. Each type focuses on different aspects of network security, such as identifying security vulnerabilities, evaluating security processes, and testing the resilience of the network against attacks.
How often should a security risk assessment be conducted?
A security risk assessment should be conducted regularly, ideally at least annually or whenever significant changes are made to the organization’s network. Regular assessments help ensure that your security measures are up-to-date and effective in responding to new vulnerabilities and threats.
What is involved in performing a network security risk assessment?
Performing a network security risk assessment involves a systematic approach that includes identifying accessible hosts, scanning the network for vulnerabilities, analyzing security metrics, and reviewing current security processes. This comprehensive analysis helps identify areas for improvement and strengthen the overall security posture.
What tools are used for conducting a network security assessment?
Various security tools are used for conducting a network security assessment, including automated security scanners, vulnerability management systems, and network intrusion detection systems. These tools aid in identifying security vulnerabilities and assessing the organization’s current security measures.
How can organizations enhance their network security?
Organizations can enhance their network security by regularly conducting network security assessments, implementing robust security measures, and ensuring that all security processes are consistently updated. Additionally, training staff to recognize and respond to security incidents can significantly improve the organization’s overall security posture.
What is the goal of a network security assessment?
The goal of a network security assessment is to provide a thorough analysis of an organization’s network vulnerabilities and security risks. This process helps organizations develop effective security strategies, protect sensitive information, and ensure compliance with industry regulations.
What is a network security assessment?
A network security assessment is an audit that evaluates the security measures and vulnerabilities present within a network. This process aims to identify weaknesses that could be exploited by attackers and to ensure your security posture is robust against potential threats.
Why is conducting a network security assessment important?
Conducting a network security assessment is crucial for maintaining a secure network. It helps organizations understand their security controls and risk mitigation strategies, ensuring that they can effectively protect sensitive data and systems from cyber threats.
What types of network security assessments are available?
There are various types of network security assessments, including vulnerability assessments, penetration testing, and security audits. Each type focuses on different aspects of network security, helping organizations identify security vulnerabilities and enhancing network resilience.
How often should a security risk assessment be performed?
A security risk assessment should be performed regularly to keep up with evolving threats and changes in the network environment. Frequent assessments help find security gaps and ensure that the entire network remains secure against new vulnerabilities.
What does a security risk assessment process involve?
The security risk assessment process involves several steps, including identifying assets, assessing potential threats, evaluating existing security controls, and determining the impact of potential security breaches. This thorough analysis aids in developing effective security strategies.
Can security consultants assist with network security assessments?
Yes, security consultants can provide valuable insights and expertise when conducting a network security assessment. They help organizations identify vulnerabilities, recommend security improvements, and ensure compliance with industry standards.
How does a risk assessment help in securing a network?
A risk assessment helps identify potential security vulnerabilities and threats within a network. By understanding these risks, organizations can implement appropriate security controls and strategies to mitigate risks and enhance overall network security.
What is the role of network enumeration in security assessments?
Network enumeration is a key step in security assessments. It involves gathering information about the network’s devices, services, and configurations. This information is essential for identifying vulnerabilities and assessing the security posture of the network.
What are common security vulnerabilities found in network assessments?
Common security vulnerabilities include weak passwords, unpatched software, open ports, and misconfigured firewalls. Identifying these vulnerabilities during a network security assessment is critical for implementing effective security measures.