New Clever Phishing Attack Uses Japanese Character “ん” to Mimic Forward Slash
The Deceptive “ん” Phishing Attack: A New Twist in URL Mimicry
In the evolving landscape of cyber threats, attackers constantly innovate, finding subtle ways to bypass security measures and human vigilance. A recent discovery highlights this ingenuity: a sophisticated phishing campaign leveraging the Japanese hiragana character “ん” (pronounced “n”) to mimic a forward slash within URLs. This novel approach creates highly deceptive links, capable of fooling even experienced internet users and sophisticated security filters. This post delves into the specifics of this attack, its implications, and crucial remediation actions for individuals and organizations.
Understanding the “ん” Phishing Technique
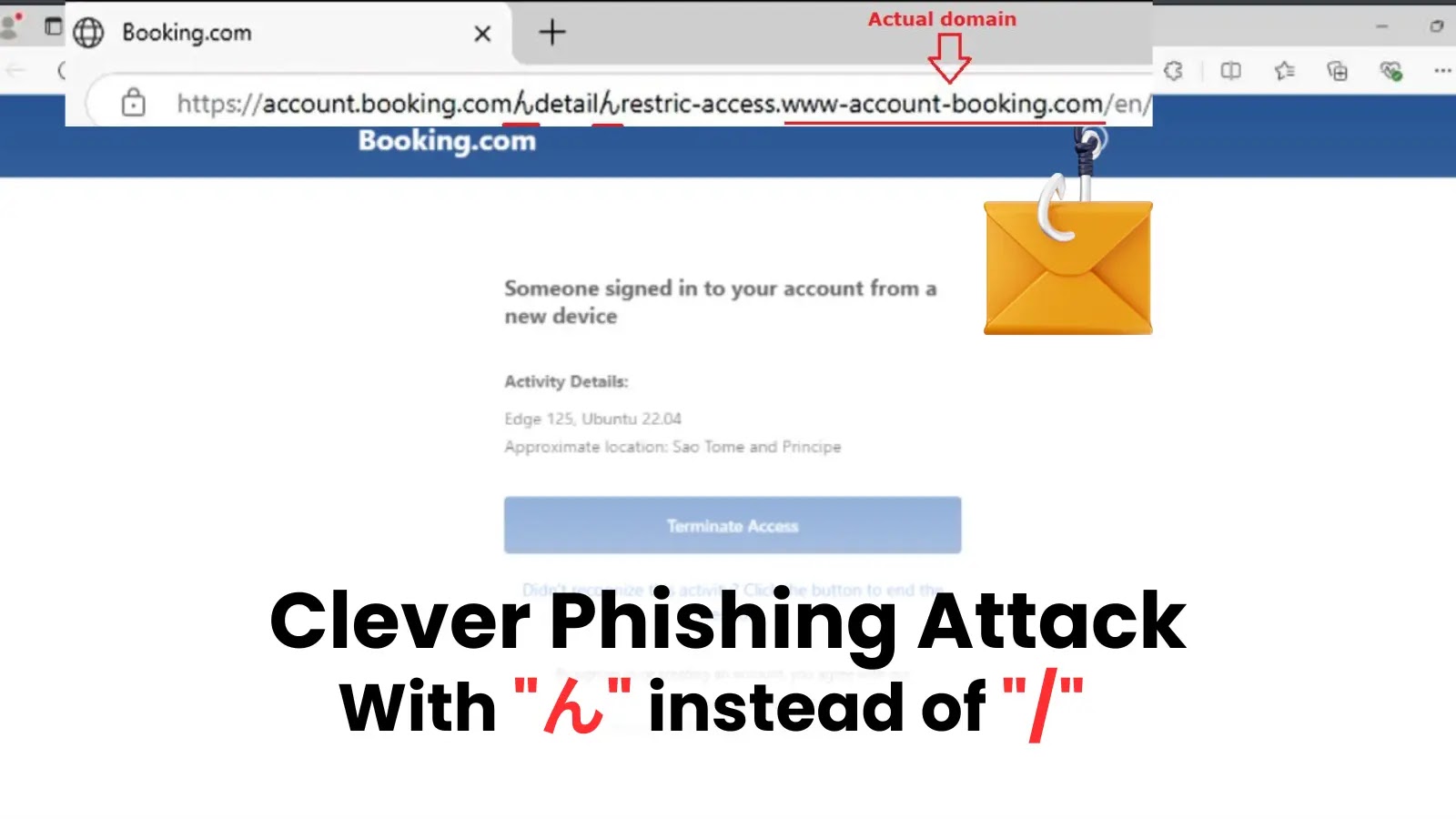
The core of this clever phishing technique lies in visual deception. The Japanese hiragana character “ん” bears a striking resemblance to a forward slash (/) when rendered in certain fonts or at smaller sizes, especially on mobile devices. Attackers exploit this visual similarity by embedding “ん” characters in place of genuine forward slashes in URLs. For instance, a legitimate URL segment like booking.com/myaccount could appear as booking.comんmyaccount. To the untrained eye, or even a rushed one, this distinction is easily missed.
Security researcher JAMESWT was credited with first identifying this campaign, which specifically targets customers of the popular travel booking platform, Booking.com. The malicious URLs are designed to appear as authentic Booking.com links, luring users into disclosing sensitive information such as login credentials, payment details, or personal data.
How the Attack Works
The attack vector typically involves spear-phishing emails or messages. Victims receive communications that appear to originate from Booking.com, perhaps confirming a booking, offering a special deal, or alerting them to an account issue. Within these messages, the crafted URL containing the deceptive “ん” character is embedded. When clicked, the user is redirected to a malicious spoofed website, meticulously designed to mirror Booking.com’s legitimate login or data entry pages.
Because the “ん” is a legitimate Unicode character, many traditional URL parsing mechanisms or basic security filters might not flag it as immediately suspicious, making it a particularly insidious threat. This technique cleverly bypasses common pattern-matching rules that look for malformed URLs or typical phishing indicators.
Implications for Cybersecurity
This “ん” character attack underscores several critical implications for cybersecurity:
- Enhanced Deception: It demonstrates attackers’ increasing sophistication in crafting visually convincing phishing lures that bypass human vigilance.
- Unicode Exploitation: It highlights the ongoing challenge of Unicode character exploitation in phishing and spoofing attacks, where visually similar but technically different characters can be used for malicious purposes.
- User Awareness Gaps: It exposes a significant gap in general user awareness regarding subtle URL inconsistencies, emphasizing the need for continuous security education.
- Limitations of Traditional Filters: While advanced security solutions might detect these anomalies, simpler email and web filters might struggle to differentiate between legitimate and deceptive URLs using such characters.
Remediation Actions and Best Practices
Mitigating the risk of this and similar phishing attacks requires a multi-layered approach, combining technological safeguards with robust user education.
For Organizations:
- Advanced Email Security Gateways: Implement and configure email security solutions that can perform in-depth URL analysis, including Unicode character inspection, and proactively block suspicious links.
- Web Content Filtering: Utilize web filtering solutions that can identify and block access to known malicious domains and dynamically analyze URL structures for anomalies.
- DNS Filtering: Employ DNS filtering services to prevent users from resolving malicious domains, even if they bypass other security layers.
- Employee Training and Awareness: Conduct regular, hands-on phishing simulation exercises and provide continuous education on identifying sophisticated phishing attempts, emphasizing the importance of scrutinizing URLs character by character. Train employees to hover over links to reveal the true URL before clicking.
- Incident Response Plan: Ensure a well-defined incident response plan is in place to quickly address and contain the fallout from successful phishing attacks.
For Individuals:
- Always Verify URLs: Before clicking on any link, especially in emails or messages, hover your mouse over the link to reveal the full URL. Scrutinize the domain name carefully. Even if it looks legitimate, slight variations can indicate a malicious site.
- Type URLs Directly: For sensitive sites like banking, travel booking, or e-commerce platforms, always type the URL directly into your browser or use official bookmarks, rather than clicking links from emails.
- Use Multi-Factor Authentication (MFA): Enable MFA on all your online accounts, especially for financial, email, and social media platforms. MFA adds an extra layer of security, making it harder for attackers to gain access even if they steal your credentials.
- Beware of Urgency or Threats: Phishing emails often create a sense of urgency, fear, or offer irresistible deals. Be skeptical of any message that demands immediate action or threatens account closure.
- Report Suspicious Activity: If you receive a suspicious email or message that appears to be from a legitimate company (e.g., Booking.com), report it to the company directly through their official channels.
- Keep Software Updated: Ensure your operating system, web browser, and security software (antivirus/anti-malware) are always up to date to protect against known vulnerabilities.
Tools for Detection and Prevention
While no single tool is a complete panacea, combining various security solutions can significantly bolster defenses against phishing attacks.
| Tool Category | Purpose | Examples/Key Features |
|---|---|---|
| Email Security Gateways (SEG) | Advanced threat protection for email, including URL sandboxing and anomaly detection. | Proofpoint, Mimecast, Microsoft Defender for Office 365, Barracuda Essentials |
| Web Content Filtering / Secure Web Gateways (SWG) | Block access to malicious websites and analyze web traffic in real-time. | Zscaler, Symantec (Broadcom), Forcepoint, Cisco Umbrella |
| Phishing Simulation Platforms | Educate users through realistic phishing tests and training. | KnowBe4, Cofense, PhishMe, GreatHorn |
| Endpoint Detection & Response (EDR) | Monitor and respond to threats on endpoints, including suspicious browser activity. | CrowdStrike Falcon, SentinelOne, Microsoft Defender for Endpoint |
| Domain Name System (DNS) Security | Block connections to malicious domains at the DNS level. | Cisco Umbrella, Cloudflare Gateway, Infoblox |
Conclusion
The “ん” character phishing attack against Booking.com customers is a stark reminder that cybercriminals are constantly seeking innovative ways to circumvent traditional defenses and exploit human psychology. This particular technique, leveraging a subtle visual similarity for profound deceptive effect, highlights the ongoing need for both advanced technical safeguards and relentless user education. As digital interactions become increasingly ubiquitous, vigilance, critical thinking, and layered security measures are paramount in protecting individuals and organizations from increasingly sophisticated online threats.





